This is the multi-page printable view of this section. Click here to print.
Guide
- 1: ISO Standard-Based Enterprise Open Source Management Guide
- 1.1: 1. Organization
- 1.2: 2. Policy
- 1.3: 3. Process
- 1.4: 4. Tools
- 1.5: 5. Education
- 1.6: 6. Conformance
- 2: NIPA OpenChain Guide
- 2.1: I. OpenChain Project란?
- 2.1.1: 1. OpenChain Specification
- 2.1.2: 2. OpenChain Conformance
- 2.1.3: 3. OpenChain Curriculum
- 2.2: II. OpenChain Specification 준수 방법
- 2.2.1: 1. 프로그램 성립
- 2.2.2: 2. 관련 업무 정의 및 지원
- 2.2.3: 3. 오픈소스 콘텐츠 검토 및 승인
- 2.2.4: 4. 컴플라이언스 결과물 생성 및 전달
- 2.2.5: 5. 오픈소스 커뮤니티 참여에 대한 이해
- 2.2.6: 6. 설명서 요건 준수
- 2.3: 부록
- 3: A Handbook for Software Supply Chain Security in the Telco Industry
- 4: Templates
- 4.1: Open Source Policy
- 4.2: Open Source Process
- 5: Tools
- 6: [out of date] Open Source Governance for Enterprises
- 6.1: 1. What is ISO/IEC 5230
- 6.2: 2. Essential elements
- 6.3: 3. Team
- 6.4: 4. Policy
- 6.5: 5. Process
- 6.6: 6. Tool
- 6.7: 7. Training
- 6.8: 8. Conformance
- 6.9: Appendix
1 - ISO Standard-Based Enterprise Open Source Management Guide
If an organisation fails to manage open source, it may encounter risks such as license non-compliance and security breaches. Therefore, what and how should we manage it?
In this article, we will examine the minimum core requirements and techniques that organisations need to implement for managing open source based on ISO international standards.
Author: Haksung Jang (haksung@sktelecom.com) / CC BY 4.0
International Standards for Open Source Management
There are two global standards for open source management:
- ISO/IEC 5230: OpenChain Specification - International standard for open source compliance.
- ISO/IEC 18974: OpenChain Security Assurance Specification - International standard for Open Source Security
OpenChain Project
The international standard for managing these open sources was created by the OpenChain Project. For an introduction to this, please refer to the following page: OpenChain Project
What should companies do?
If a company complies with the requirements of the two standards (ISO/IEC 5230, ISO/IEC 18974), it can be seen as effectively managing open source.
So, what should companies do to comply with the standards? It needs to have the following six components:
- Organization
- Policy
- Process
- Tools
- Education
- Conformance
To comply with the standards, companies must adhere to these six components:
References
1.1 - 1. Organization
First, companies need to establish an organization responsible for managing open source.
The following should be considered when organizing:
- Roles and responsibilities of the organization
- Required competencies for each role
- The organization/person in charge of each role
1. Defining the roles and responsibilities of the organization
ISO standards commonly require a document describing the roles and responsibilities of various participants in the program.
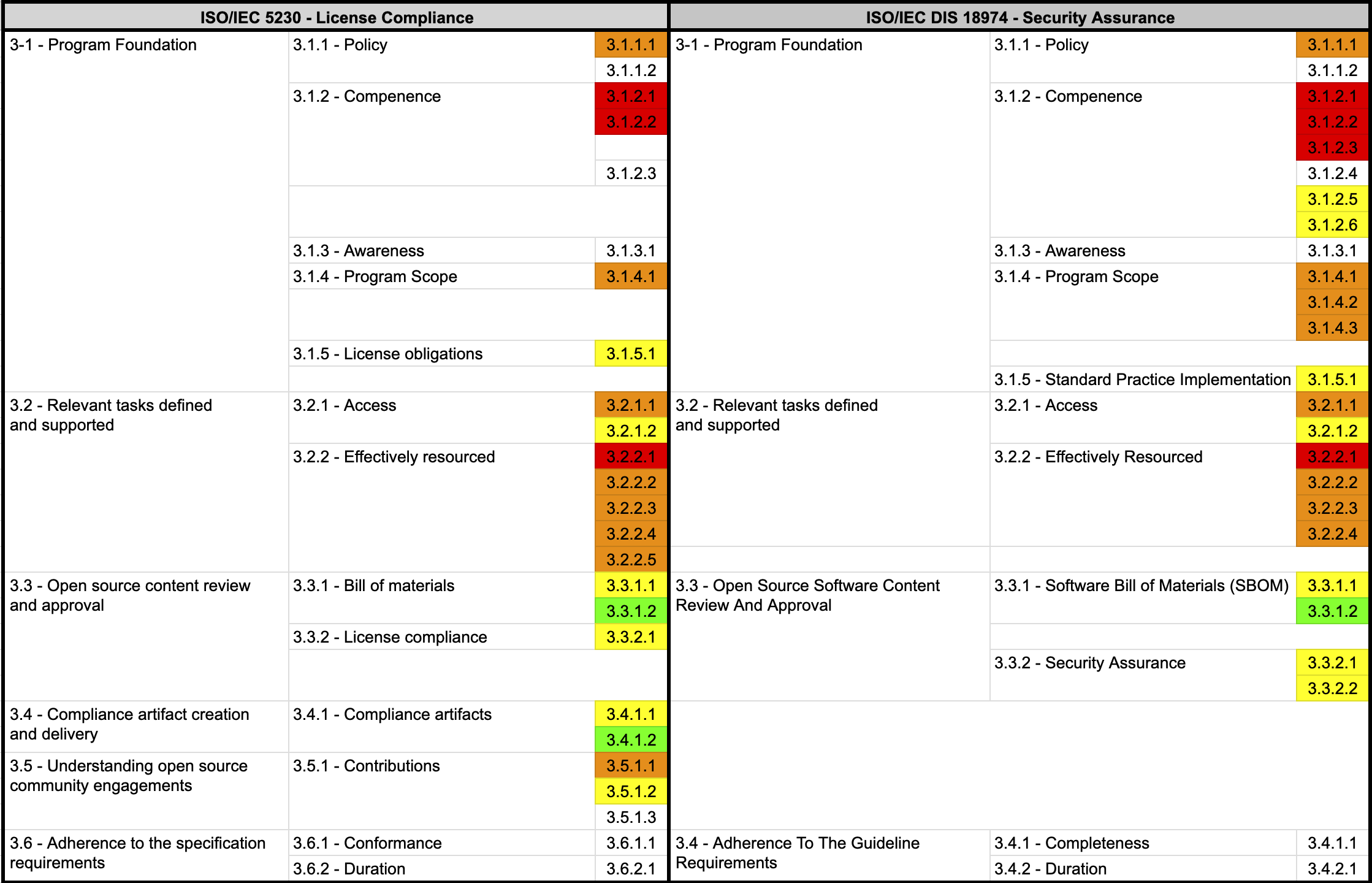
ISO/IEC 5230 - License Compliance
- 3.1.2.1 - A documented list of roles with corresponding responsibilities for the different participants in the program.
ISO/IEC 18974 - Security Assurance
- 3.1.2.1: A documented list of roles with corresponding responsibilities for the different Program Participants
Open Source Program Manager
To build an open source management system, you first need a person responsible for it. This person is called the Open Source Program Manager or Open Source Compliance Officer, and here we use the term Open Source Program Manager.
The Open Source Program Manager is in charge of the company’s Open Source Program Office. The Open Source Program Office refers to the organization responsible for managing the company’s open source, and is also referred to as the Open Source Office.
A person with the following competencies may be suitable for the role of open source program manager.
- Understanding of the open source ecosystem and development experience
- Broad understanding of the company’s business
- Passion and communication skills to propagate effective open source utilization to company members
It is best to ensure that the Open Source Program Manager can perform the role full-time if possible.
Global ICT companies are striving to hire excellent Open Source Program Managers. You can check various job postings on the following site: https://github.com/todogroup/job-descriptions
Documenting roles and responsibilities
Companies need to define the roles needed for the Open Source Program Office and determine what responsibilities to assign.
In the case of small companies, it is possible for the Open Source Program Manager to perform all roles alone. Depending on the size of the company, there may also be a need for an IT officer to operate open source tools, and the role of a legal officer may be required to provide professional legal advice.
Generally, the following roles are needed to build a company’s open source management system.
- Legal officer
- IT officer
- Security officer
- Development culture officer

For this, companies should document the roles and responsibilities of the Open Source Program Office as follows.
| No | Role | Responsibility |
|---|---|---|
| 1 | Open Source Program Manager | Responsible for the company’s open source program. |
| 2 | Legal Officer | Interprets open source licenses and obligations. Provides advice to mitigate legal risks that may arise from using open source. |
| 3 | IT Officer | Operates and automates open source analysis tools to ensure that open source analysis is smoothly performed for all software to be distributed. |
| 4 | Security Officer | Operates open source vulnerability analysis tools to ensure that vulnerability analysis is performed for all software to be distributed, and takes measures to ensure that discovered vulnerabilities are remedied according to standards. |
| 5 | Development Culture Officer | Supports company developers to actively use open source and participate in internal and external communities to acquire advanced development culture. |
| 6 | Business Department | The software development/distribution organization complies with open source policies and processes for proper open source use. |
2. Definition of Required Competencies
Once you have defined each role and its responsibilities, you need to identify what essential competencies are required for the personnel to perform that role.
The ISO standard commonly requires a document that describes the competencies needed for each role.
ISO/IEC 5230 - License Compliance
- 3.1.2.2 - A document that identifies the competencies for each role.
ISO/IEC 18974 - Security Assurance
- 3.1.2.2: A document that identifies the competencies for each role.
This is to evaluate whether the person in charge of each role has the ability to perform that role, and to provide education if necessary.
For this, companies should document the competencies needed for each role as follows:
| No | Role | Required Competencies | ||
|---|---|---|---|---|
| 1 | Open Source Program Manager | 1. Understanding of software development process 2. Understanding of intellectual property related to open source licenses such as copyright, patent, etc. 3. Expert knowledge on open source compliance 4. Open source development experience 5. Communication skills | ||
| 2 | Legal Officer | 1. Basic knowledge of the open source ecosystem 2. Expert knowledge on software copyright 3. Expert knowledge on open source licenses | ||
| 3 | IT Officer | 1. Basic knowledge of open source compliance process 2. Understanding of open source analysis tools 3. Expert knowledge on IT infrastructure | ||
| 4 | Security Officer | 1. Broad understanding of DevSecOps 2. Understanding of open source vulnerability analysis tools 3. Expert knowledge on open source security vulnerabilities 43. Communication skills | ||
| 5 | Development Culture Officer | 1. Understanding of software development process 2. Basic knowledge on open source compliance 3. Understanding of open source policy | ||
| 6 | Business Department | 1. Understanding of software development process 2. Basic knowledge on open source compliance 3. Understanding of open source policy 4. Basic knowledge on open source licenses |
3. Appointment of Responsible Person
The Open Source Program Manager consults with the relevant departments to appoint a person in charge for each role and documents it. Of course, to do this, you need to report the goals and directions for establishing an open source compliance system to the CEO or other top decision-makers and receive the necessary support.
The organization and person in charge of open source do not necessarily have to participate in open source work full-time. It is also possible to form a virtual organization in the form of an OSRB (Open Source Review Board) to perform the necessary roles.
For this, the ISO standard commonly requires a document that lists the names of the persons, groups, or functions in the program roles.
ISO/IEC 5230 - License Compliance
- 3.2.2.1 - Document with name of persons, group or function in program role(s) identified.
ISO/IEC 18974 - Security Assurance
- 3.1.2.3: List of participants and their roles
- 3.2.2.1: Document with name of persons, group or function in Program role(s) identified
For this, companies should document the names of the persons, groups, or functions in the program roles as follows:
| No | Role | Responsible Organization | Responsible Person | ||
|---|---|---|---|---|---|
| 1 | Open Source Program Manager | CTO | OOO | ||
| 2 | Legal Officer | Legal Team | OOO | ||
| 3 | IT Officer | IT Infrastructure Team | OOO | ||
| 4 | Security Officer | Security Team | OOO | ||
| 5 | Development Culture Officer | DR | OOO | ||
| 6 | Business Department | Development Team | All |
You can refer to the sample that documented the roles, responsibilities, required competencies, and appointment of responsible persons in the next page. [Appendix 1] Open Source Policy template - Appendix 1. Status of Responsible Persons
SK Telecom has formed an OSRB to create open source policies and processes within the company, and collaborates to develop countermeasures when issues arise.

Summary
You can check the sample that documented the roles, responsibilities, required competencies, and appointment of responsible persons in the Open Source Policy template: Appendix 1. Status of Responsible Persons
Companies can refer to this to form an open source management organization suitable for their situation.
By designating and documenting the open source program office organization in this way, you will meet the requirements marked in red in the ISO standard specification.

In fact, it is more important to appoint a person who will faithfully perform the actual work and support the person in charge to secure the competency than to document it.
1.2 - 2. Policy
1. Open Source Policy Documentation
Enterprises should establish and document an open source policy, which consists of principles for organizations involved in software development, service, and distribution to properly utilize open source. This policy should be disseminated within the organization.
For this, the ISO standard commonly requires the following documented open source (security assurance) policies:
ISO/IEC 5230 - License Compliance
- 3.1.1.1 - A documented open source policy.
ISO/IEC 18974 - Security Assurance
- 3.1.1.1: A documented Open Source Software Security Assurance policy
A typical open source policy includes the following. Enterprises should create and document an open source policy that includes these principles:
- Principles to minimize license and security vulnerability risks when distributing software products and services
- Principles for contributing to external open source communities
- Principles for releasing the company’s software as open source
2. Contents to be Covered in Open Source Policy
Let’s take a closer look at what an open source policy should include.
Open Source Risk Response
When developing products/services using open source, the policy should include the following principles to minimize license and security vulnerability risks:
- Identification of open source and review of license obligations
- Design considering open source licenses
- Creation of open source compliance deliverables
- Creation of SBOM (Software Bill of Materials)
- Response to open source license compliance issues
- Response to open source security vulnerabilities
You can refer to the principles documented in 6. Open Source Use of [Appendix 1] Open Source Policy template.
1. Open Source Use
When developing and distributing products and services using open source, you must comply with the obligations required by each open source license. This activity is called open source compliance.
For proper open source compliance activities, software development/distribution organizations comply with the following matters and record all processes in the Jira Tracker for preservation.
(1) Identification of open source and review of license obligations
When introducing open source to product/service development, first identify what the open source license is, and review and confirm the obligations required by the license.
The company's [Open Source License Guide] includes a list of major open source licenses, and distinguishes the obligations required by each license according to the following types of distribution:
- Binary form
- Source form
- Strong/weak Copyleft
- SaaS-based provision
- Whether modification is made
- Requirement to indicate the author's open source, etc.
Software development/distribution organizations can refer to this guide when reviewing open source license obligations. If a review of an open source license not mentioned in this guide is required, contact the open source program manager.
(2) Design considering open source licenses
Understand the combination relationship of open source and design the software architecture so that the company's code is not affected by the open source license.
The company's [Open Source License Guide] explains the range of source code disclosure for each open source license and the design method to prevent the disclosure of the company's code.
(3) Creation of open source compliance deliverables
The most basic of open source compliance activities is to understand the status of open source included in the distribution software. This is to properly meet the core of open source compliance, which is the requirements of the open source license. In other words, you need to create a set of compliance deliverables for the open source included in the distribution software.
Open source compliance deliverables are largely divided into two.
1. Open source notice: A document for providing open source license text and copyright information
2. Package of source code to be disclosed: A package that collects source code to be disclosed to fulfill the obligations of open source licenses that require source code disclosure
To collect, distribute, and store these compliance deliverables, comply with the following matters.
- The open source notice or package of source code to be disclosed is collected according to the conditions required by each license. For example, if the license requires the entire text of the license to be enclosed, you should not just provide a link.
- The collected deliverables are stored in a separate repository.
- If the source code to be disclosed is provided by a written agreement, the download link is disclosed so that the repository of the collected deliverables can be accessed from the outside.
You can issue an open source notice and collect a package of source code to be disclosed through the company's open source process.
(4) Creation of SBOM (Bill of Materials)
You need to create and manage the status of open source included in the distribution software (BOM: Bill of Materials).
You can create and preserve SBOM using open source tools through the company's open source process.
(5) Compliance issue response procedure
If a compliance issue is raised, the open source program manager performs the following procedures to respond quickly.
1. Confirm the receipt of the inquiry and specify the appropriate resolution time.
2. Confirm whether the content of the issue points out a real problem. (If not, notify the issue raiser that it is not a problem.)
3. If it is a real problem, prioritize and decide on an appropriate response.
4. Perform the response, and if necessary, appropriately supplement the open source process.
5. The above contents are preserved using the Jira Tracker.
(6) Response to open source security vulnerabilities
- Identify open source vulnerabilities and evaluate their severity.
- Modify vulnerabilities or apply security patches according to the results of open source vulnerability analysis. The decision to take action on vulnerabilities considers the severity of the vulnerability, the importance of the system, the availability of vulnerability modifications or security patches, etc.
- Monitor the announcement of new open source security vulnerabilities and respond quickly when vulnerabilities occur. Open source vulnerability monitoring can be performed through vulnerability databases such as CVE, websites of security professional organizations, etc.
Internal Responsibility Assignment Procedure
The open source policy should cover the procedure for assigning responsibility internally to resolve open source management issues.
The ISO standard commonly requires the following documented procedures that assign internal responsibilities:
ISO/IEC 5230 - License Compliance
- 3.2.2.4 - A documented procedure that assigns internal responsibilities for open source compliance.
ISO/IEC 18974 - Security Assurance
- 3.2.2.4: A documented procedure that assigns internal responsibilities for Security Assurance.
Firstly, the open source program manager must identify compliance issues and appropriately assign responsibilities to the role holders to resolve them. Similarly, for open source security vulnerability issues, the security manager identifies the issues and assigns responsibilities to the appropriate personnel to resolve them.
To do this, you can reflect a documented procedure for assigning internal responsibilities in the open source policy, as shown in the example below:
1. Roles, Responsibilities, and Competencies
To ensure the effectiveness of the policy, we define the roles, responsibilities, and competencies that each role holder should possess.
(2) Open Source Program Manager
- Defines the roles necessary for open source compliance, and designates the responsible organization and person for each role. Consults with the OSRB as necessary. The security manager assigns internal responsibilities for open source security assurance.
(6) Security Manager
- Assigns responsibilities for each task to ensure the success of open source security assurance.
Response to Non-compliance Cases
Companies should document procedures to quickly review and respond when non-compliance cases occur.
ISO/IEC 5230 requires a documented procedure for reviewing and remedying non-compliant cases, as follows:
ISO/IEC 5230 - License Compliance
- 3.2.2.5 - A documented procedure for handling the review and remediation of non-compliant cases.
For this, companies can reflect a documented procedure for reviewing and remedying non-compliance cases in the open source policy, as shown in the example below:
6. Open Source Use
(5) Compliance Issue Response Procedure
When a compliance issue is raised, the open source program manager quickly responds by following the procedure below:
1. Confirm the inquiry and specify an appropriate resolution time.
2. Verify whether the issue content points to an actual problem. (If not, inform the issue raiser that it is not a problem.)
3. If it is an actual problem, prioritize and decide on an appropriate response.
4. Perform the response and, if necessary, appropriately supplement the open source process.
5. Preserve the above content using the Jira Tracker.
Support for Personnel and Budget
Companies should provide sufficient resources to ensure the smooth operation of the open source program. They should properly allocate personnel to handle each role within the program, and guarantee sufficient budget and working hours. If not, procedures should be in place to supplement this.
The ISO standard commonly requires that personnel handling each role within the program be properly allocated and that the budget be adequately supported, as follows:
ISO/IEC 5230 - License Compliance
- 3.2.2.2 - The identified program roles have been properly staffed and adequate funding provided.
ISO/IEC 18974 - Security Assurance
- 3.2.2.2: The identified Program roles have been properly staffed and adequate funding provided;
For this, companies can reflect content on personnel and budget support in the open source policy, as shown in the example below:
4. Roles, Responsibilities, and Competencies
The head of the organization responsible for each role designates a person in charge within the organization and allocates appropriate time and budget for the person in charge to faithfully perform the role.
- If the person in charge of each role finds that they are not receiving appropriate support while performing their role, they should raise the issue with the open source program manager.
- The open source program manager discusses problem-solving with the head of the organization. If it is not resolved appropriately, the open source program manager can request problem-solving from the OSRB.
- The OSRB shares the problem with the head of the upper organization and requests a solution.
Provision of Expert Advice
Companies should provide a way for role holders to request advice when professional review is needed to resolve open source issues.
The ISO standard commonly requires a method to use internal or external expert advice to solve problems, as follows:
ISO/IEC 5230 - License Compliance
- 3.2.2.3 - Identification of legal expertise available to address open source license compliance matters which could be internal or external.
ISO/IEC 18974 - Security Assurance
- 3.2.2.3: Identification of expertise available to address identified Known Vulnerabilities
For open source license compliance issues, the company’s legal team is primarily responsible, and if the issue is acute, an external law firm with an open source specialist lawyer can be used.
For open source security vulnerability issues, the company’s security team is primarily responsible, and if the issue is complex and acute, advice can be requested from an external security technology company.
For this, companies can reflect content on providing advice in the open source policy, as shown in the example below:
4. Roles, Responsibilities, and Competencies
(4) Legal Manager
The legal manager provides advice on legal risks and mitigation measures that may arise during the process of using open source, such as interpreting open source licenses and obligations.
- Provides a reasonable way for members to inquire about open source compliance issues.
- Provides advice on license and intellectual property issues, including conflicts due to incompatible open source licenses.
- Reviews necessary legal matters such as open source licenses, CLA (Contributor License Agreement), etc. when contributing to external open source projects.
- If the issue is acute, requests advice from an external law firm with an open source specialist lawyer.
(6) Security Manager
The security manager operates an open source vulnerability analysis tool to build a system that allows security vulnerability analysis to be performed smoothly for all distribution software.
- Provides a reasonable way for members to inquire about security vulnerabilities, and uses external technical advice as needed to resolve vulnerabilities.
For reference, the OpenChain Project provides a list of global law firms that provide open source related advice through its partner program: https://www.openchainproject.org/partners
Law firms registered as OpenChain partners have met the requirements of the OpenChain Project.
Specifying the Scope of Application
A single open source policy (program) does not necessarily have to be applied to the entire organization. Depending on the characteristics of each organization and product within the company, the scope of application can be specified differently. For example, an organization that does not distribute software at all can be excluded from the scope of the open source program.
The ISO standard commonly requires a documented statement that clearly defines the scope and limits of the program, as follows:
ISO/IEC 5230 - License Compliance
- 3.1.4.1 - A written statement that clearly defines the scope and limits of the program.
ISO/IEC 18974 - Security Assurance
- 3.1.4.1: A written statement that clearly defines the scope and limits of the Program
- 3.1.4.2: A set of metrics the program shall achieve to improve
- 3.1.4.3: Documented Evidence from each review, update, or audit to demonstrate continuous improvement.
Companies should clearly define the scope and limits of the open source program considering the characteristics of the organization and products, and specify this in the open source policy.
Also, as changes occur in accordance with changes in the business environment, situations may arise where the organizational structure, products, and services determine or modify the scope of the program. Companies should establish metrics for evaluating the scope of application and improve deficiencies by performing reviews and inspections for continuous improvement.
For this, companies should have a system that clearly defines the scope of application in the open source policy and documents the activity history, as shown below:
1. Scope of Application
This policy applies to the following three parts:
1. It applies to all products provided or distributed externally by the company. However, the use of open source for internal use only is not included in the scope of this policy.
2. It applies when members contribute to external open source projects.
3. It applies when internal code is disclosed as open source.
The scope of application can be changed to suit the company's business environment. In particular, the open source program manager investigates at least once a month whether there are products that are not subject to this policy and are distributed or serviced externally to ensure continuous effectiveness. This is measured and used as a criterion for changing the scope of application when even one case is found.
The procedure for changing the scope of application is as follows:
1. If the open source program manager determines that it is necessary to change the scope of application of the policy due to changes in the company's business environment such as new business and organizational restructuring, it submits a proposal for this to the OSRB.
2. The OSRB approves an appropriate level of change in the scope of application.
3. The OSRB modifies the open source policy to change the scope of application.
The open source program manager continuously documents the review, update, and inspection history for improving the scope of application at least once a month using the Jira Issue Tracker.
Therefore, companies should have a system that clearly defines the scope of application in the open source policy and documents the activity history.
Responding to External Inquiries
There are cases where customers and open source copyright holders contact the company to make inquiries, requests, and claims about products or services developed using open source.
The main contents of external inquiries and requests are as follows:
- Inquiry about whether open source has been used in a specific product or service
- Request for source code provision under the GPL, LGPL license mentioned in the written agreement (Written Offer)
- Explanation and source code disclosure request for open source that was not specified in the open source notice but was found in the product
- Request for missing files and build methods in the source code disclosed due to obligations such as GPL, LGPL
- Request for copyright notice
- Inquiries and requests related to open source security vulnerabilities
Companies should designate a person in charge of handling these external inquiries. Typically, the open source program manager is in charge.
There are cases where an external open source developer wants to contact a company’s person in charge to discuss an open source related issue of a specific company, but cannot find a way to contact and eventually files a legal claim directly. To prevent this, companies should always publicly disclose a way for third parties to contact the company about open source.
The ISO standard commonly requires a publicly visible method that allows any third party to make an open source license compliance inquiry, as follows:
ISO/IEC 5230 - License Compliance
- 3.2.1.1 - Publicly visible method that allows any third party to make an open source license compliance inquiry (e.g., via a published contact email address, or the Linux Foundation’s Open Compliance Directory).
ISO/IEC 18974 - Security Assurance
- 3.2.1.1: Publicly visible method to allow third parties to make Known Vulnerability or Newly Discovered Vulnerability enquires (e.g., via an email address or web portal that is monitored by Program Participants)
Companies can provide a way to contact the company about open source, as shown below:
Sure, here’s the translation of the guide in professional style:
- The representative email address of the open source responsible organization is made public.
- The Open Compliance Directory of the Linux Foundation is used.
- If the company has an open source website, the email address is made public through it.
Including the representative email address of the open source responsible organization in the open source notice that comes with the product and service and making it public is also a good method.
Companies can reflect the following content on external inquiries in their open source policies:
9. Response to External Inquiries
(1) Responsibility for Responding to External Inquiries
The open source program manager is responsible for responding to inquiries and requests about open source from outside.
- The open source program manager can assign the handling of all or part of the inquiry to appropriate personnel within the company. If necessary, the legal representative is consulted for handling.
- Anyone who receives an inquiry about open source from outside informs the open source program manager so that a quick response can be made.
(2) Disclosure of Contact Information
The open source program manager provides the contact information of the person in charge publicly so that inquiries and requests related to open source can be made from outside.
- Provides email address information that can be contacted in the open source notice.
- Provides email address information on the open source website.
- Registers the contact information in the Open Compliance Directory of the Linux Foundation.
(3) Procedure for Responding to External Inquiries
If you respond quickly and accurately to open source inquiries from outside, you can greatly reduce the risk of claims or legal litigation. To this end, the company complies with the procedure for responding to external inquiries defined in the company's open source process.
SK Telecom includes an open source notice in all products. The open source notice provides the address of the SK Telecom open source website and the email address that can contact the open source program office.

Also, the SK Telecom Open Source Website provides an email address that can contact the open source program office.

Open Source Contribution
Global software companies not only use open source to create products and provide services, but also value the strategic value that can contribute to and create open source projects. However, if you approach without sufficient understanding of the open source project ecosystem and community operation methods and strategies, the company’s reputation may be unexpectedly damaged and legal risks may occur. Therefore, it is important for companies to establish strategies and policies for participating in and contributing to open source projects.
ISO/IEC 5230 requires a documented open source contribution policy.
ISO/IEC 5230 - License Compliance
- 3.5.1.1 - A documented open source contribution policy
You can check the open source contribution policy in [Appendix 1] Open Source Policy template 7. Open Source Contribution.
7. Open Source Contribution
The company encourages participation and contribution to external open source projects to create business value from open source. However, care must be taken to avoid unintentional exposure of the company’s intellectual property or infringement of third-party rights during this process. To this end, members of the company must comply with the following when contributing to external open source projects:
(1) Request for Review and Approval
Contributing to open source is granting the open source project the right to modify, use, and distribute the work from a copyright perspective. Sometimes, you may need to transfer your copyright to the open source project. However, the copyright of works created during the employment period is generally owned by the employer. In other words, the works created by company members are owned by the company. The act of arbitrarily contributing works to open source can trigger unnecessary copyright infringement issues.
Therefore, if there is an open source project you want to contribute to, you must comply with the review request and approval process before making the initial contribution according to the open source contribution process.
However, in the case of simple content such as the following, you can contribute according to the judgment of the member without the review process because the risk of copyright infringement is not high:
- Small code snippets of 10 lines or less
- Questions / Answers on Stack Overflow
- Management activities on GitHub: Creating Issues, Reviewing / Approving Pull Requests, etc.
...
Companies should refer to this and include principles for open source contributions that suit the company’s situation in the open source policy.
Summary
Documenting the open source policy is the most important process for effective open source management.
The next page provides a sample open source policy document that meets the requirements mentioned above in ISO/IEC 5230 and ISO/IEC 18974: [Appendix 1] Open Source Policy template
It is necessary to establish appropriate principles for each requirement according to the company’s situation and to consider executable procedures, not just documents. A policy that is only spoken is useless.
By establishing and documenting an open source policy like this, you can meet the requirements marked in orange in the ISO standard specifications.

1.3 - 3. Process
The open source process is an executable procedure that allows companies to comply with open source policies during the software development and distribution process.
From the perspective of open source license compliance, activities are carried out to comply with the conditions required by each license for the open source used in developing and distributing software, resulting in the creation of deliverables such as open source notices and source code to be disclosed.

For open source security assurance, activities must be carried out to detect the presence of security vulnerabilities in the software to be distributed, identify structural/technical threats, and resolve issues before release.
In order for a company to effectively achieve open source license compliance and security assurance, the following processes must be established:
- Open source process
- Open source vulnerability process
- External inquiry response process
- Open source contribution process
Let’s take a look at how each process should be structured.
1. Open Source Process
Companies should establish an open source process for open source license compliance and security vulnerability management according to the software development process.
The image below is a sample open source process that companies can generally adopt and use.

The procedures to be taken at each stage according to the open source process are as follows:
(1) Identification and Inspection of Open Source
In the identification and inspection stage of open source, it is necessary to identify what license the open source you want to use is, what obligations the license requires, and whether there are known vulnerabilities.
Review and record which open source you want to use, what its license is, what obligations each license imposes, and what known vulnerabilities are.
The ISO/IEC 5230 standard requires a documented procedure to handle common open source license use cases and to review and record the obligations, restrictions, and rights granted by each identified license.
ISO/IEC 5230 - License Compliance
3.3.2.1 - A documented procedure for handling the common open source license use cases for the open source components of the supplied software.
3.1.5.1 - A documented procedure to review and document the obligations, restrictions and rights granted by each identified license.
An example of a procedure for this is as follows:
The open source program manager provides a guide on the obligations, restrictions, and rights of major open source licenses. This guide should include the following use cases to handle common open source license use cases:
- Distribution in binary form
- Distribution in source form
- Integration with other open source that triggers additional license obligations
- Inclusion of modified open source
The business unit checks the license and known vulnerabilities according to the criteria defined in the open source policy.
The business unit consults with the open source program manager and security officer on any questions. If necessary, advice is sought from external experts.
All decisions and related grounds are documented and kept.
For this, companies should establish a documented procedure to review and record the obligations, restrictions, and known vulnerabilities granted by each identified license before product release through the open source identification and inspection stage.
(1) Open Source Identification
The business unit complies with the following matters at the software design stage.
- Identify the anticipated open source usage status and check the license while designing the software.
- Check the obligations of each open source license. The obligations of each license can be checked in the company's open source license guide. : https://sktelecom.github.io/guide/use/obligation/
- Design the software considering the source code disclosure range of each open source license.
The open source program manager creates and publishes a guide on the obligations, restrictions, and rights of major open source licenses so that the business units of the company can refer to it. This guide should include the following use cases to handle common open source license use cases:
- Distribution in binary form
- Distribution in source form
- Integration with other open source that triggers additional license obligations
- Inclusion of modified open source
The business unit marks copyright and license in the source code according to the company rules. The company's source code copyright and license marking rules can be found on the following page. (insert_link)
When the business unit considers introducing new open source, it first identifies the license. According to the company's open source license guide, check the obligations, restrictions, and rights of the license. If the license is not explained in the company's open source license guide, ask the open source program manager about the possibility of introduction and precautions. Create a Jira Ticket for inquiries.
The open source program manager analyzes the obligations of the open source license and guides the software development organization.
- If there is any doubt, consult with the legal officer and provide clear guidance.
- The newly analyzed license information is reflected in the company-wide license guide.
The security officer provides a guide for the company's security assurance.
(2) Source Code Inspection
The business unit requests an open source check according to the guidance of the IT manager and provides the source code.
The IT manager uses the open source analysis tool to check the open source and create an SBOM (Software Bill of Materials).
The open source program manager reviews the possibility of complying with the open source license obligations, checks for conflicts between open source licenses, and if there are issues, requests the business unit to resolve them. Issues are created as Jira Tickets and assigned to the business unit.
The security officer reviews the detected known vulnerabilities and provides a response guide to the business unit according to the pre-defined Risk classification criteria. Risk is classified by CVSS (Common Vulnerability Scoring System) Score, and Critical Risk is guided to establish a plan that can be addressed within 1 week.
In the open source identification and inspection stage, source code scanning tools can be used. More details on this can be found in “1. Source Code Scanning Tools”.
(2) Problem Solving
After identifying open source through open source identification and inspection, and confirming the risks of licenses and security vulnerabilities, a procedure is needed to solve the problem. All detected problems should be solved in the following ways:
- Remove the open source that is causing the issue.
- Replace with open source under a different license to resolve open source license issues.
- Replace with a version of open source where known vulnerabilities have been resolved.
An example of a documented process for this is as follows:
(3) Problem Solving
The business department solves all problems found in the source code inspection stage.
Remove the open source that is causing the issue, or replace it with open source under a different license. In the case of security vulnerability issues, measures such as replacing with a version where known vulnerabilities have been fixed are taken.
Once the business department has resolved all discovered issues, they resolve the Jira Ticket issue and request a re-review.
(3) SBOM Identification, Review, and Storage
The most basic of open source license compliance activities is to understand the status of open source included in the distributed software. You need to build a process to create and manage an SBOM (Software Bill of Materials) that contains information identifying the open source and its licenses included in the distributed software. Knowing which open source is included in each version of the distributed software is essential for complying with the obligations required by each open source license when distributing software. This is also an essential process for discovering and responding to open source security vulnerabilities.
All open source must be reviewed and approved before being integrated into the distributed software. Not only the functionality and quality of the open source, but also whether the origin, license requirements can be met, and whether known vulnerabilities have been resolved, etc., must be reviewed in advance. A review request → review → approval process is required for this.
ISO standards commonly require a documented procedure that ensures that all open source software used in the supplied software is continuously recorded during the lifecycle of the supplied software.
ISO/IEC 5230 - License Compliance
- 3.3.1.1 - A documented procedure for identifying, tracking, reviewing, approving, and archiving information about the collection of open source components from which the supplied software is comprised.
ISO/IEC 18974 - Security Assurance
- 3.3.1.1: A documented procedure ensuring all Open Source Software used in the Supplied Software is continuously recorded across the lifecycle of the Supplied Software. This includes an archive of all Open Source Software used in the Supplied Software;
For this, companies can reflect the following content about SBOM in the open source process:
(4) Review
The open source program manager reviews whether all issues have been properly supplemented. If necessary, the source code inspection is re-performed using the open source analysis tool.
The security officer reviews whether all serious vulnerabilities have been resolved. If there are vulnerabilities that are difficult to resolve, they review whether they can be approved considering the business form and service exposure status.
(5) Approval
The open source program manager finally approves or rejects whether the open source compliance procedure has been properly performed. If rejected, they propose a reason and a modification method to the business department.
(6) Registration
The open source program manager finalizes the BOM to track the list of open source used in each version of the software.
The IT officer registers the finalized BOM in the system. The BOM includes a list of open source included in the distributed software and the following information:
- Product (or service) name and version of the distributed software
- Open source list
- Open source name / version
- Open source license
The open source program manager finalizes the BOM to track the list of open source used in each version of the software.
For more details on tools for managing SBOM, see “SBOM Management Tools”.
Also, all processes and results of such open source processes must be documented. It is more efficient to use an issue tracking system such as Jira, Bugzilla than using email.
(4) Creation of License Compliance Artifacts
As mentioned above, the most basic of open source license compliance activities is to understand the status of open source included in the distributed software. This is precisely because it is the core of open source license compliance to properly meet the requirements of open source licenses. In other words, a process must be established to create a set of compliance artifacts for the open source included in the distributed software.
The ISO/IEC 5230 standard requires a documented procedure that describes the process under which the compliance artifacts are prepared and distributed with the supplied software as required by the identified licenses.
ISO/IEC 5230 - License Compliance
- 3.4.1.1 - A documented procedure that describes the process under which the compliance artifacts are prepared and distributed with the supplied software as required by the identified licenses.
Compliance artifacts are divided into two main categories:
Open Source Notice: A document for providing open source license text and copyright information
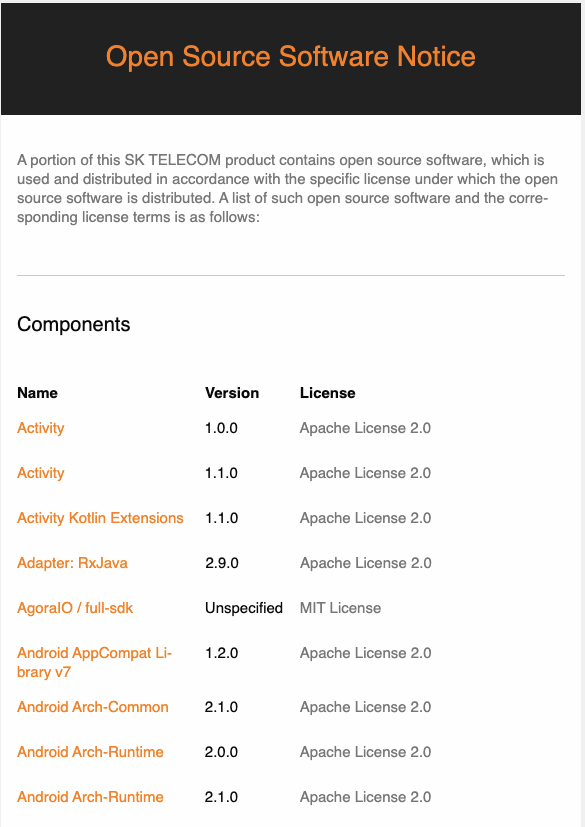
- For how to create an open source notice that aggregates the SBOM using tools, see “Open Source Compliance Artifact Generation Tools”.
Sure, here is the English translation of the Korean guide you provided, written in a professional style suitable for user manuals, help documents, and technical documents:
- Source Code Package to be Disclosed: A package that consolidates source code to be disclosed in order to comply with the obligations of open source licenses that require source code disclosure, such as GPL, LGPL.
Compliance deliverables must be provided along with the distribution of the software for distribution.
For this, companies can reflect the content on the creation of compliance deliverables from the notification stage to the distribution stage in the open source process as follows:
(7) Notification
The open source program manager creates an open source notice to comply with the notification obligation. The open source notice includes the following:
- Open source contact point where open source related inquiries can be made
- Notice content for each open source
- Copyright
- Open source license name
- Copy of open source license
- (If applicable) Written agreement to obtain a copy of the source code (Written Offer)
The open source program manager creates an open source notice and delivers it to the business department. At this time, if source code disclosure is necessary, the method of collecting the source code to be disclosed is guided to the business department.
The business department includes the open source notice when distributing the product. If the product has a screen, measures are taken so that the user can check it through the menu. (Example: App > Menu > Settings > Copyright Information > Open Source License)
The business department, when using open source under a license that requires source code disclosure such as GPL, LGPL, checks the scope of source code disclosure for this and collects the source code to be disclosed.
- The source code collected to comply with the obligations of licenses such as GPL, LGPL must match the source code that constitutes the binary loaded on the product. In other words, if you build the collected source code, it must be the same as the binary loaded on the product.
(8) Confirmation before distribution
The business department submits the following deliverables to prove that the open source compliance activities have been properly performed.
1. Final open source notice included in the product
2. Materials confirming that the open source notice is included in the product (Example: Screen capture image showing the open source notice)
3. (If applicable) Source code to be disclosed (Submit as a single file compressed)
The open source program manager reviews the materials submitted by the business department and checks for any abnormalities.
(9) Distribution
The open source program manager submits the compliance deliverables submitted by the business department to the IT manager.
The IT manager registers the compliance deliverables on the company's open source distribution site.
When distributing software for distribution, it may be difficult to include a package of source code to be disclosed. In this case, you can substitute it by providing a written agreement (Written Offer) that you will provide the source code for at least 3 years. Typically, the written agreement is provided through the product’s user manual, and the example is as follows:
The software included in this product contains copyrighted software
that is licensed under the GPL. A copy of that license is included
in this document on page X. You may obtain the complete Corresponding
Source code from us for a period of three years after our last shipment
of this product, which will be no earlier than 2011-08- 01, by sending
a money order or check for $5 to:
GPL Compliance Division
Our Company
Any Town, US 99999
Please write“source for product Y” in the memo line of your payment.
You may also find a copy of the source at http://www.example.com/sources/Y/.
This offer is valid to anyone in receipt of this information.
<Source: SFLC Guide to GPL Compliance>
Therefore, compliance deliverables must be kept for more than 3 years, and a process for this must be established.
For this, companies can consider building an open source website. You can check the details in “Open Source Compliance Artifact Storage”.
2. Open Source Security Vulnerability Process
Companies must perform activities for security assurance, such as detecting and resolving open source security vulnerabilities, while developing products/services.
The ISO/IEC 18974 standard requires documented procedures and records of actions taken for security assurance methods as follows:
ISO/IEC 18974 - Security Assurance
3.1.5 - Standard Practice Implementation
The Program demonstrates a sound and robust handling procedures of Known Vulnerabilities and Secure Software Development by defining and implementing following procedures:
Method to identify structural and technical threats to the Supplied Software is defined;
Method for detecting existence of Known Vulnerabilities in Supplied Software;
Method for following up on identified Known Vulnerabilities;
Method to communicate identified Known Vulnerabilities to customer base when warranted;
Method for analyzing Supplied Software for newly published Known Vulnerabilities post release of the Supplied Software;
Method for continuous and repeated Security Testing is applied for all Supplied Software before release;
Method to verify that identified risks will have been addressed before release of Supplied Software;
Method to export information about identified risks to third parties as appropriate.
3.1.5.1: A documented procedure exists for each of the methods identified above.
3.3.2 - Security Assurance
- 3.3.2.1: A documented procedure for handling detection and resolution of Known Vulnerabilities for the Open Source Software components of the Supplied Software;
- 3.3.2.2: For each Open Source Software component a record is maintained of the identified Known Vulnerabilities and action(s) taken (including even if no action was required).
In order to address vulnerabilities in the deployed software, enterprises must detect the presence of known vulnerabilities in the distribution-ready software and resolve identified risks before release. Furthermore, they need to establish methods and procedures to respond to newly discovered vulnerabilities post-release.
Initially, enterprises should detect known vulnerabilities in the distribution-ready software and resolve identified risks before release. The procedure for detecting and addressing these known vulnerabilities can be carried out through the open-source identification phase, source code inspection phase, and issue resolution phase of the open-source process, as outlined in Open Source Process.
Additionally, when newly identified vulnerabilities are disclosed after the release of the deployed software, it is imperative to establish a process for confirming their existence in the already distributed software and taking necessary measures to address them.
Below is a sample process for responding to the discovery of new security vulnerabilities:

1. New Security Vulnerability Process
After a product/service is launched in the market, we adhere to the following process to take appropriate measures according to the risk level when a new security vulnerability is reported.
(1) Monitoring
The IT department operates a system that monitors new security vulnerabilities. This system performs the following functions:
- Regularly collects information about newly disclosed security vulnerabilities.
- If an open source with a new known vulnerability is used in a product/service that has already been released, it sends a notification to the business department in charge of the product/service. From notification to review, action, and resolution, everything is documented and recorded using the Jira Issue Tracker.
(2) Initial Response
The security officer provides a response guide to the business department according to the pre-defined risk classification criteria. Risks are classified by CVSS (Common Vulnerability Scoring System) scores, and Critical Risk is guided to establish a plan that can be implemented within 1 week.
If a new security vulnerability is found in a product/service that has already been released, the business department establishes a response plan according to the response guide provided by the security officer.
If there are customers who need assurance, the business department notifies the confirmed known vulnerabilities by email or other means as needed, depending on the risk level.
(3) Problem Solving
The business department solves the security vulnerability problem by deleting the problematic open source or replacing it with a patched version, etc., according to the established response plan. Once all issues are resolved, a re-review is requested.
(4) Review
The IT department uses an open source analysis tool to check whether the problem has been properly resolved.
(5) Approval
The security officer reviews whether all serious vulnerabilities have been resolved. If there are vulnerabilities that are difficult to resolve, the approval is reviewed considering the business form and service exposure status.
(6) Registration
The IT department registers the SBOM, which has resolved the open source security vulnerability, in the system.
(7) Notification
The open source program manager creates an open source notice based on the SBOM that has resolved the open source security vulnerability and delivers it to the business department.
The business department replaces the open source notice included in the product distribution.
The IT department registers the modified open source notice on the company's open source distribution site.
(8) Distribution
The business department redistributes the software version that has resolved the open source security vulnerability.
The security officer identifies whether there is risk information that needs to be disclosed to third parties, and if so, delivers it to the IT department.
The IT department registers the identified risk information on the open source website so that third parties can check it.
3. External Inquiry Response Process
In order for a company not to lead to legal litigation due to external claims, it is important to respond as quickly and accurately as possible to external inquiries and requests. To this end, companies should establish a process that can respond quickly and effectively to external open source inquiries.
ISO standards commonly require the following internal documented procedures to respond to third-party inquiries.
ISO/IEC 5230 - License Compliance
- 3.2.1.2 - An internal documented procedure for responding to third party open source license compliance inquiries.
ISO/IEC 18974 - Security Assurance
- 3.2.1.2: An internal documented procedure exists for responding to third party Known Vulnerability or Newly Discovered Vulnerability inquiries.
The following figure is a sample process that a company should have in order to respond to external inquiries.
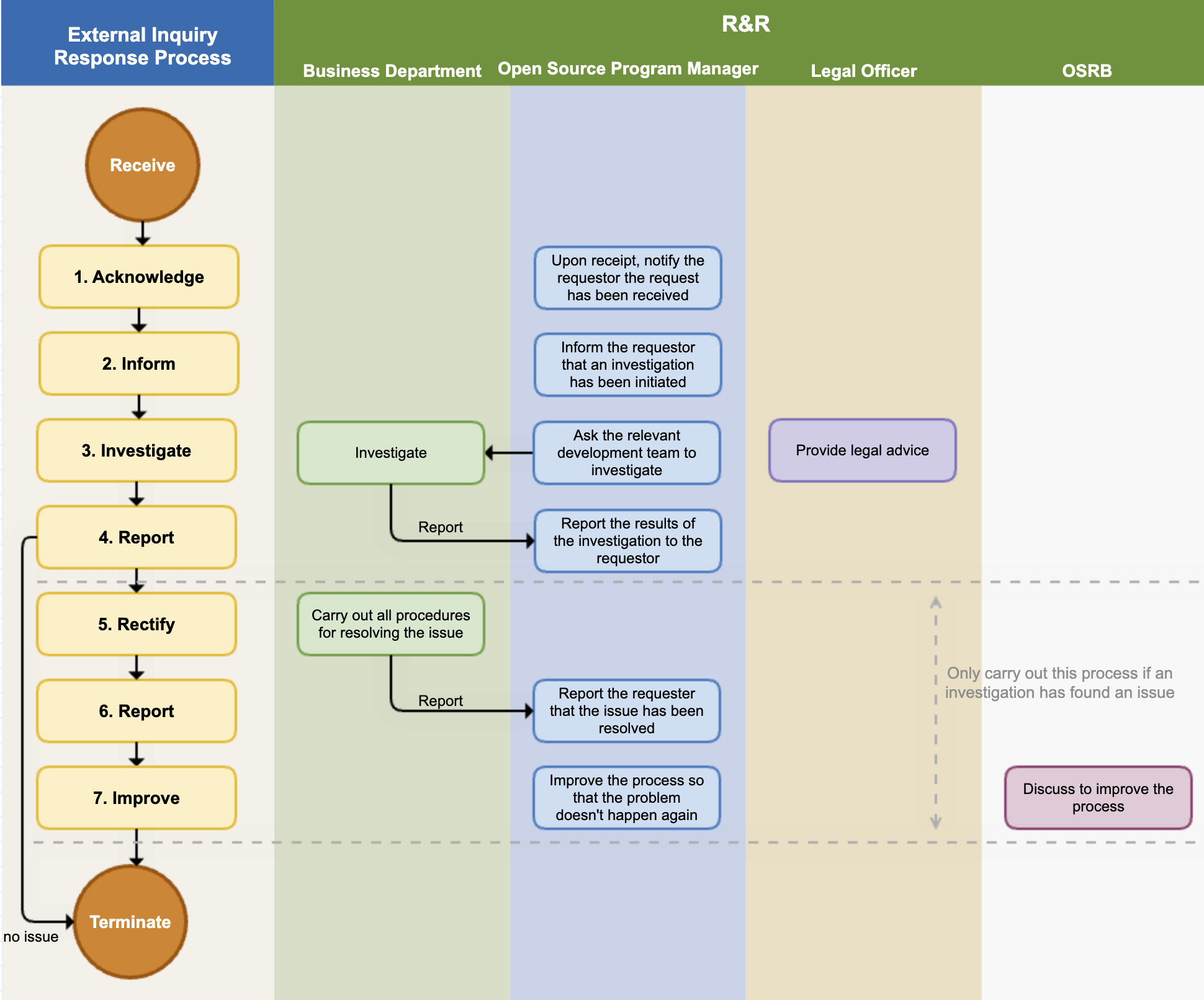
If you respond quickly and accurately to open source compliance inquiries from outside, you can greatly reduce the risk of proceeding to litigation. To this end, the company adheres to the following process to respond to external open source compliance inquiries.
(1) Receipt Notification
As soon as the open source program manager receives an inquiry, they notify the requester that the inquiry has been received. At this time, they also notify the expected date of action. If the inquiry is unclear, they request additional explanation.
The main contents of the inquiries and requests that require response are as follows:
- Inquiry whether open source has been used in a specific product or service
- Request for source code provision under GPL, LGPL license mentioned in written agreement (Written Offer)
- Explanation and source code disclosure request for open source found in the product but not specified in the open source notice
- Request for missing files and build methods in the source code disclosed due to obligations such as GPL, LGPL
- Copyright notice request
The open source program manager creates a Jira Issue for the received request and records all the response situations in detail.
(2) Investigation Notification
The open source program manager notifies the requester that they are investigating the open source compliance. It is good to notify whenever the internal investigation progress is updated.
(3) Internal Investigation
The open source program manager conducts an internal investigation on the request. They check whether the compliance process has been properly performed for the version of the product in question through the BOM and documented review history. If necessary, they request advice from the legal department.
If it is a matter that needs to be confirmed by a specific business department, the open source program manager requests an investigation from the business department. The business department immediately checks whether there is a problem with the compliance deliverables upon receiving the investigation request and reports the results to the open source program manager.
(4) Report to Requester
The open source compliance officer completes the internal investigation within the expected date of action and notifies the requester of the result.
- If the requester's inquiry was a misdirected point due to misunderstanding, they notify the requester and end the process without any additional action.
- If there is a problem, they notify the requester of the exact method and timing to fulfill the obligations of the open source license in question.
(5) Problem Supplement / Notification
If a compliance problem is actually found in the internal investigation, the relevant business department performs all procedures necessary to solve the compliance problem.
(6) Problem Resolution Notification
After solving the problem, they immediately notify the requester and provide the best way to confirm that the problem has been resolved.
(7) Process Improvement
If there was a compliance problem, the OSRB meeting reviews the case, identifies the circumstances of the problem, and improves the process so that the problem does not recur.
Sure, here is the translation of the text you provided:
4. Open Source Contribution Process
If a company has a policy that allows contributions to external open source projects, there should be a documented procedure for how in-house developers can contribute to external projects.
The ISO/IEC 5230 standard requires a documented procedure for managing open source contributions.
ISO/IEC 5230 - License Compliance
3.5.1.2 - A documented procedure that governs open source contributions;The Open Source Contribution Process published by SK Telecom is a good example.
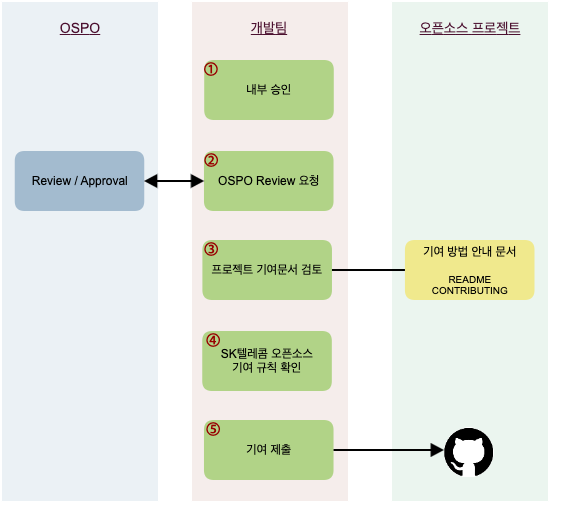 https://sktelecom.github.io/guide/contribute/process/
https://sktelecom.github.io/guide/contribute/process/
5. Process Modernization
It is not desirable for the process to be documented but not actually operated. Also, it is a problem if it does not fit the business situation or organizational composition. Companies should always keep the process up-to-date to match the internal organization and situation of the company.
The ISO/IEC 18974 standard requires periodic review and improvement of the process.
ISO/IEC 18974 - Security Assurance
- 3.1.2.5: Documented Evidence of periodic reviews and changes made to the process;
- 3.1.2.6: Documented verification that these processes are current with company internal best practices and who is assigned to accomplish them.
Companies can define in the open source policy document that they improve the open source policy and open source process every year and document and record all processes.
1. Roles, Responsibilities, and Competencies
To ensure the effectiveness of the policy, we define the roles and responsibilities and the competencies that each role holder should have as follows.
(1) OSRB
The OSRB (Open Source Review Board) is a consultative body composed of the open source program manager and the heads of related organizations such as the legal team, patent team, development team, and infrastructure team for the company's open source management.
The OSRB improves policies and processes on a regular basis every year. All improvement processes are documented and recorded.
- The OSRB always modernizes the company's process performance results, shortcomings, best practices, and reflects the business environment.
- The policy and process for open source compliance are managed by the open source program manager.
- The policy and process for open source security assurance are managed by the security officer.
6. Summary
By building the process up to this point, you can meet the requirements marked in yellow in the ISO standard specifications.

1.4 - 4. Tools
1. Source Code Scanning Tools
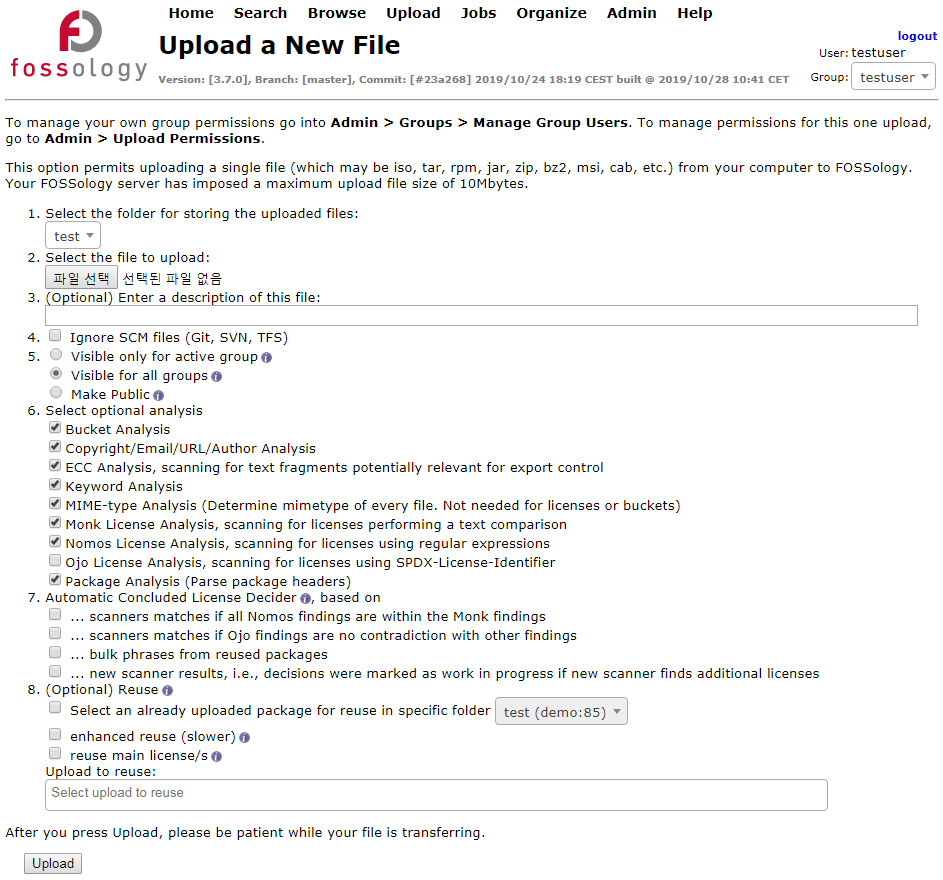
In the open source identification and inspection stages of the open source process, you can use source code scanning tools. These tools range from open source-based tools that can be used for free to commercial tools. Each tool has its strengths, but no tool provides a perfect solution to all problems. Therefore, companies should select the appropriate tool that fits the characteristics and requirements of their products.
Many companies use these automated source code scanning tools in conjunction with manual reviews. The Linux Foundation’s FOSSology project is an open source source code scanning tool that companies can easily use for free.

For information on how to install and use FOSSology, please refer to Get Started with FOSSology.
2. Dependency Analysis Tools
In recent software development, build environments that support package managers such as Gradle and Maven are used. In these build environments, even without source code, the necessary Dependency libraries are fetched from a remote space at build time to compose the distribution software. However, these Dependency libraries are included in the distribution software but are not detected by the source code scanning tools. Therefore, it is also important to use tools for Dependency analysis.
The OSS Review Toolkit, which is open source, provides a Dependency analysis tool called Analyzer.

In addition, LG Electronics has released the FOSSLight Dependency Scanner as open source. The FOSSLight Dependency Scanner supports various package managers such as Gradle, Maven, NPM, PIP, Pub, and Cocoapods.

3. SBOM Management Tools
ISO/IEC 5230 standard 3.3.1.2 requires that the SBOM list included in the distribution software be documented and stored.
ISO/IEC 5230 - License Compliance
- 3.3.1.2 - Open source component records for the supplied software that demonstrates the documented procedure was properly followed.
ISO/IEC 18974 - Security Assurance
- 3.3.1.2: Open Source Software Component Records for the Supplied Software that demonstrates the documented procedure was properly followed.
SBOM can be managed with spreadsheet programs like Excel, but it is not easy to manage manually when the number and version of distribution software exceed hundreds. Therefore, it is recommended to introduce open source automation tools for this purpose.
The SW360 project, sponsored by the Eclipse Foundation, provides the ability to track the list of open sources included in each distribution software.
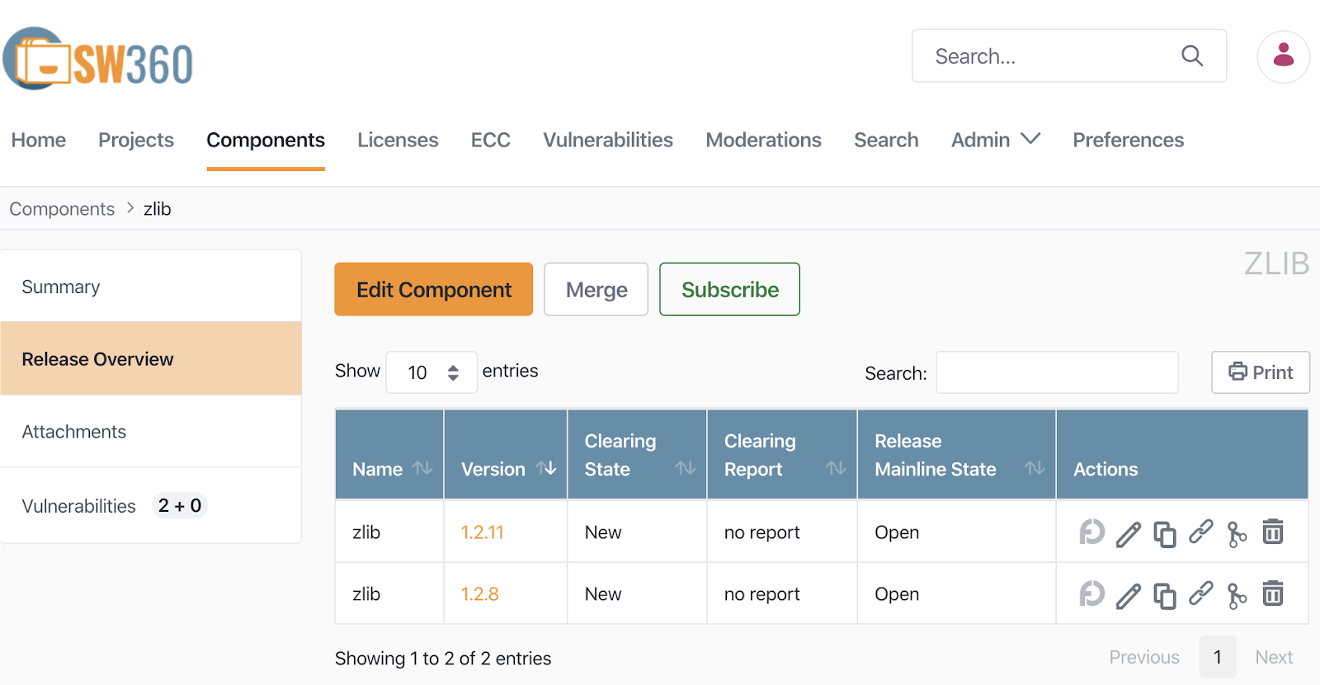
The installation and usage of SW360 can be referred to in the SW360 Docker.
And the aforementioned FOSSLight also provides features for SBOM management.

LG Electronics has been managing the SBOM for all business units’ distribution software for the past several years using FOSSLight, which it developed in-house. In June 2021, it announced that it had released it as open source so that anyone can use it.

4. Open Source Vulnerability Management Tools
Companies need to track products/services that contain known vulnerabilities and resolve them. To do this, companies need to build a tool environment that automates this.
SW360 can automatically check if there are any security vulnerabilities in the registered Release. For this, SW360 provides a feature to schedule the collection of CVE information every 24 hours. If you set up this scheduling, SW360 will collect CVE information from the CVE Search site (https://cve.circl.lu/) at the set time. After the Vulnerabilities information is collected, you can check if there are any security vulnerabilities in the created Project, so you can also track whether newly disclosed vulnerabilities exist in products that have already been released.
The method of managing security vulnerabilities with SW360 can be referred to in the SW360 guide.
FOSSLight also automatically acquires security vulnerability information and automatically checks project information where security vulnerabilities have been detected, providing notifications such as emails as needed.
5. Open Source Compliance Artifact Generation Tool
The main open source compliance artifact, the open source notice, is a document that provides copyright and license information for the open source included in the distributed software. Open source notices can be created using a document editor tool, but it is recommended to use a tool that generates them automatically.
SK Telecom has released an open source notice automatic generation tool (onot: https://github.com/sktelecom/onot) used internally as open source, and Kakao has participated in joint development by contributing major features.
onot is a tool that automatically converts SBOMs written in SPDX document format into open source notice format. It is a Python program that is lightweight and easy to use.

FOSSLight also provides a feature to automatically generate open source notices based on the acquired SBOM.

6. Open Source Compliance Artifact Storage
It is recommended that companies build an open source website and register open source compliance artifacts so that external customers can conveniently download open source notices and source code packages to be disclosed for distributed software at any time.
For this, the ISO/IEC 5230 standard requires a documented procedure for archiving copies of the compliance artifacts of the supplied software.
ISO/IEC 5230 - License Compliance
- 3.4.1.2 - A documented procedure for archiving copies of the compliance artifacts of the supplied software - where the archive is planned to exist for a reasonable period of time (Determined by domain, legal jurisdiction and/or customer contracts) since the last offer of the supplied software; or as required by the identified licenses (whichever is longer). Records exist that demonstrate the procedure has been properly followed.
You can refer to this tool environment on SK Telecom’s open source website.

This website was developed as open source, and the source code is open, so other companies can easily build a similar environment.

7. Summary
If you build up to the tool environment, you can meet the requirements marked in green in the ISO standard specification.
1.5 - 5. Education
1. Education
No matter how excellent the policies and processes are, they will be useless if no one in the organization pays attention to them. For open source policies and processes to work effectively in a company, member education is crucial.
Companies should provide practical means such as education and internal wikis so that all program participants are aware of the existence of open source policies within the organization and can perform necessary activities. Program participants here refer to all employees involved in the development, distribution, and contribution of software, including software developers, distribution engineers, and quality engineers.
For this, the ISO standard commonly requires the following documented procedures to inform about the open source policy:
ISO/IEC 5230 - License Compliance
- 3.1.1.2 - A documented procedure that makes program participants aware of the existence of the open source policy (e.g., via training, internal wiki, or other practical communication method).
ISO/IEC 18974 - Security Assurance
- 3.1.1.2: A documented procedure to make Program Participants aware of the Security Assurance policy.
Many companies make their open source policy documents available through internal wiki sites so that any employee can check the necessary items. In addition, they mandate education on open source policies during the orientation of new hires and provide regular education once a year or every two years to all program participants, ensuring that all program participants are aware of the existence of the open source policy.
Companies should include these methods in the open source policy document as follows:
5. Education and Evaluation
All members in charge of each role defined in Chapter 4 must take the advanced open source education course provided by [Learning Portal]. Through this, they will familiarize themselves with the open source policy, related education policy, and inquiry methods. The education history and evaluation results are kept in [Learning Portal] for at least 3 years.
Companies should ensure that program participants are aware of the company’s open source policy, open source-related goals, participant’s contribution methods for an effective open source program, and the impact of non-compliance with program requirements. To do this, companies should provide education, perform evaluations to confirm correct understanding by program participants, and document and keep the evaluation results.
The ISO standard commonly requires the following documented evidence indicating the assessed awareness of program participants:
ISO/IEC 5230 - License Compliance
- 3.1.3.1 - Documented evidence of assessed awareness for the program participants - which should include the program’s objectives, one’s contribution within the program, and implications of program non-conformance.
ISO/IEC 18974 - Security Assurance
- 3.1.3.1: Documented Evidence of assessed awareness for the Program Participants - which should include the Program’s objectives, one’s contribution within the Program, and implications of Program non-conformance.
Therefore, companies can include the following content in the company’s open source policy:
1. Purpose
(1) Purpose of the policy
This policy provides the following principles for the entire organization involved in software development, service, and distribution at OOO Co., Ltd. (hereinafter referred to as "the company") to properly utilize open source software (hereinafter referred to as "open source").
1. Open source compliance / security assurance principles
2. Principles for contributing to external open source projects
3. Principles for disclosing in-house projects as open source
These principles provide a way for all members of the company to understand the value of open source, use open source correctly, and contribute to the open source community.
All members of the company can check the open source policy at the following link on the internal wiki: [internal_link]
(2) Impact of non-compliance
If this policy is not complied with, the following situations may occur:
- You may receive a request for open source license compliance from the outside.
- You may have to disclose the source code developed by the company against your will.
- You may be sued by the open source copyright holder.
- You may be fined for copyright infringement and contract violation, or receive a product sales suspension order.
- The company's reputation may be damaged.
- You may be claimed for damages due to a contract violation with the supplier.
- You may be exposed to serious security incidents, causing significant damage to the company.
For these reasons, the company takes violations of the open source policy seriously, and members or organizations that violate this may be subject to disciplinary procedures.
(3) Contribution method of members
All members of the company can contribute to the effectiveness of the policy and the improvement of the company's compliance level by understanding the basis and content of this policy and faithfully performing the necessary activities.
The evaluation will be explained in more detail below.
The open source education includes content on the open source contribution policy. Even if an open source contribution policy is created, if no one in the company is aware of its existence, there is a risk of damage to individuals and companies due to indiscriminate contribution activities.
For this, the ISO/IEC 5230 standard requires the following documented procedure to make all program participants aware of the existence of the open source contribution policy.
ISO/IEC 5230 - License Compliance
- 3.5.1.3 - A documented procedure that makes all program participants aware of the existence of the open source contribution policy (e.g., via training, internal wiki, or other practical communication method).
Therefore, companies should provide open source education so that all in-house developers are aware of the existence of an open source contribution policy.
Creating new educational materials may not be easy for those who are just starting out. To help with these difficulties, NCSoft has made its in-house open source educational materials available to everyone by publishing the lecture (PPT) and lecture script on GitHub.

In addition, Kakao, a leading platform company in Korea, has also made its open source educational materials available for anyone to view.

If you haven’t created educational materials yet, it’s a good idea to use the open source educational materials from these excellent open source management companies.
2. Evaluation
Once a company has assigned roles, it must ensure that the assigned individuals are qualified to perform their roles based on education, training, and experience. Adequate education should be provided to program participants who lack competence. And the company must evaluate whether each participant is competent and keep the results.
For this, the ISO standard commonly requires documented evidence of assessed competence for each program participant.
ISO/IEC 5230 - License Compliance
- 3.1.2.3 - Documented evidence of assessed competence for each program participant.
ISO/IEC 18974 - Security Assurance
- 3.1.2.4 - Documented evidence of assessed competence for each Program Participant;
Therefore, companies should perform education and evaluation as follows:
- The company provides education so that each participant can have the necessary competence.
- Perform an evaluation based on the content of the education.
- The evaluation results are kept in the company’s education system or HR department.
If there are hundreds of program participants and it is not easy to provide education, it is a good idea to use the company’s online education and evaluation system.
This content can be included in the company’s open source policy as follows:
4. Roles, Responsibilities, and Competencies
To ensure the effectiveness of the policy, we define the roles and responsibilities and the competencies that each role's manager should have.
The organization/manager in charge of each role and the required competency level are defined in [Appendix 1. Manager Status].
5. Education and Evaluation
All members who are in charge of each role defined in Chapter 4 must take the advanced open source education course provided by [Learning Portal]. Through this, you will be familiar with the open source policy, related education policy, and how to inquire.
The education history and evaluation results are kept in [Learning Portal] for at least 3 years.
3. Open Source License Guide
To properly comply with open source licenses, you need to know exactly what each open source license requires. However, it is difficult for individual software developers to identify this on a daily basis, so the open source program manager should summarize the requirements/precautions for common use cases for frequently used open source licenses and share them internally.
The open source license guide should enable development departments to perform correct license compliance activities when using open source, including general requirements for common open source license use cases.
For this, the ISO/IEC 5230 standard requires a documented procedure for handling common open source license use cases for the open source components of the supplied software.
ISO/IEC 5230 - License Compliance
- 3.3.2.1 - A documented procedure for handling the common open source license use cases for the open source components of the supplied software.
To handle open source license use cases, you need a license guide classified by open source license. General guides and license obligation summary materials for open source licenses can be referred to the License Guide provided by the Korea Copyright Commission.
The License Obligation document in the open source guide of SK Telecom is also a good resource.
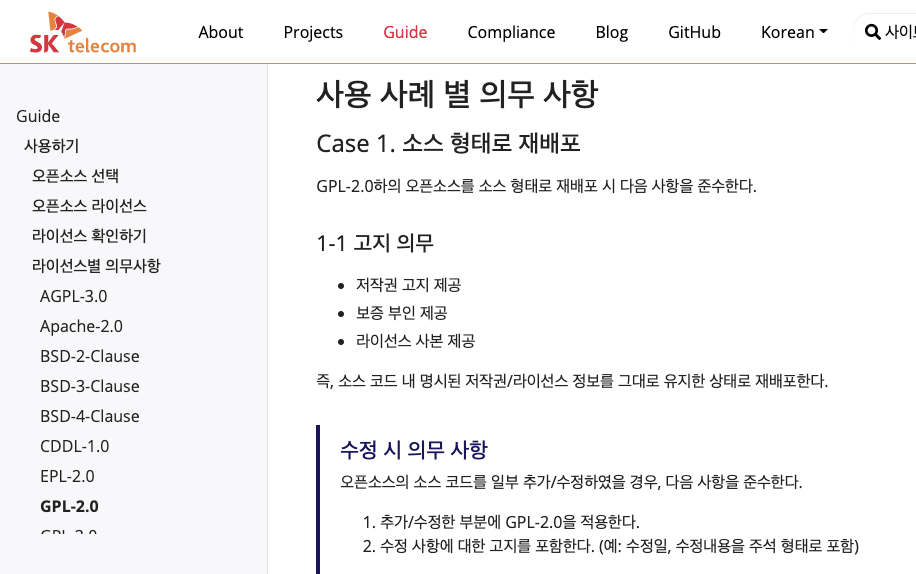 https://sktelecom.github.io/guide/use/obligation/gpl-2.0/
https://sktelecom.github.io/guide/use/obligation/gpl-2.0/
Companies should provide an open source license guide in a space where members can easily access and refer to.
4. Summary
If you have built up to the education, evaluation, and guide provision environment, you can meet the requirements of the ISO standard specifications indicated in sky blue.
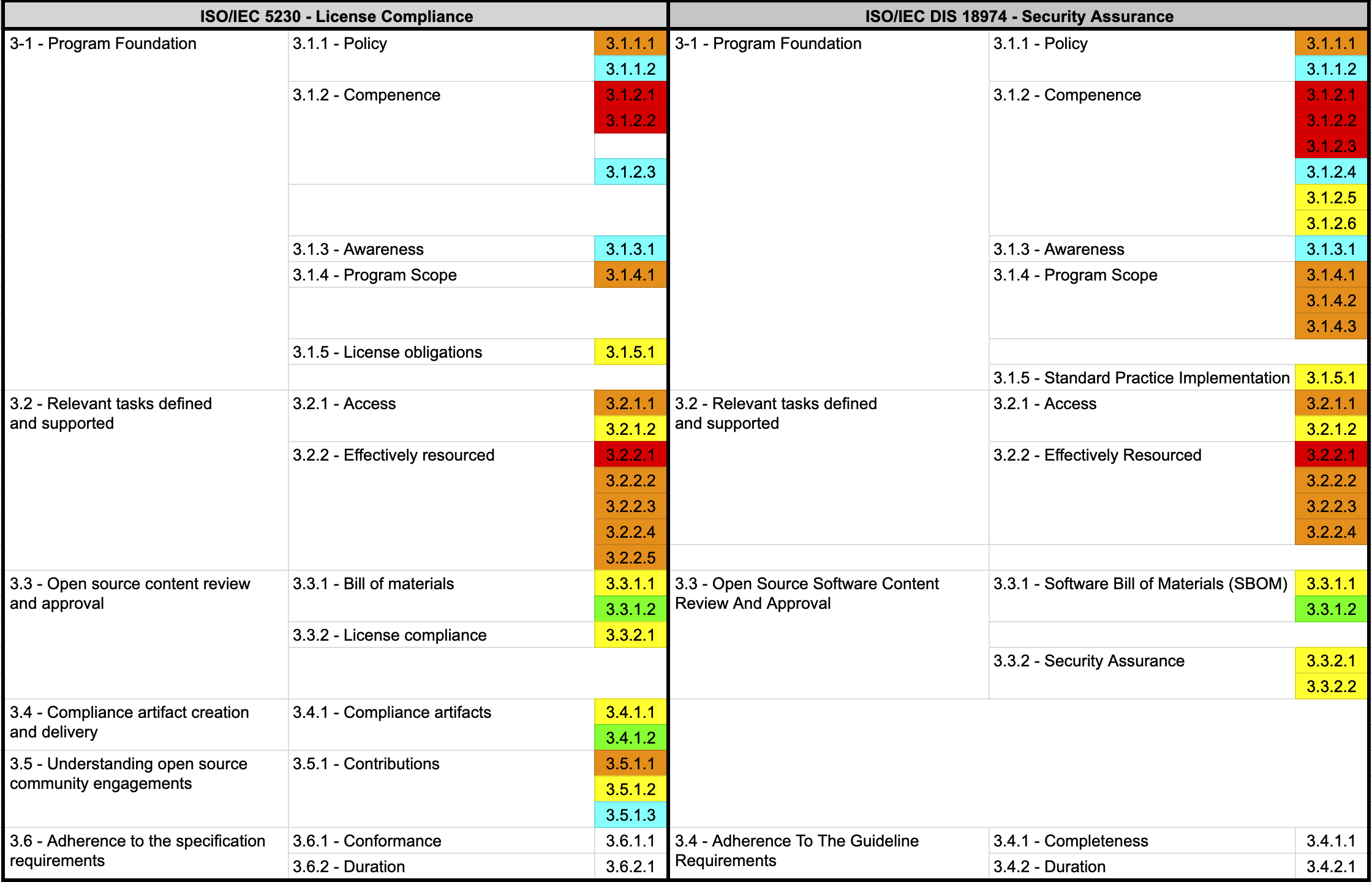
1.6 - 6. Conformance
Companies that have built an open source program (open source policy / process / tools / organization) that complies with all requirements except ISO/IEC 5230 3.6, ISO/IEC 18974 3.4 can document and specify the following two things.
For this, ISO standards commonly require the following documented procedures to announce open source policies.
ISO/IEC 5230 - License Compliance
- 3.6.1.1 A document affirming the program specified in §3.1.4 satisfies all the requirements of this document.
- 3.6.2.1 A document affirming the program meets all the requirements of this document, within the past 18 months of obtaining conformance validation.
ISO/IEC 18974 - Security Assurance
- 3.4.1.1: Documented Evidence affirming the Program specified in §3.1.4 satisfies all the requirements of this document.
- 3.4.2.1: A document affirming the Program meets all the requirements of this specification, within the past 18 months of obtaining conformance validation.
Therefore, you can document the following:
- The company’s open source program complies with all the requirements of ISO/IEC 5230, ISO/IEC 18974
- Guarantee to maintain a state that meets all the requirements of ISO/IEC 5230, ISO/IEC 18974 for more than 18 months after obtaining conformance validation
The company can include the above in its open source policy, or it can be posted through a publicly available website.
You can refer to the content posted on the open source portal site of SK Telecom as shown in the image below.
 https://sktelecom.github.io/compliance/iso5230/
https://sktelecom.github.io/compliance/iso5230/
By doing so, you can meet the requirements marked in blue in the ISO standard specifications.
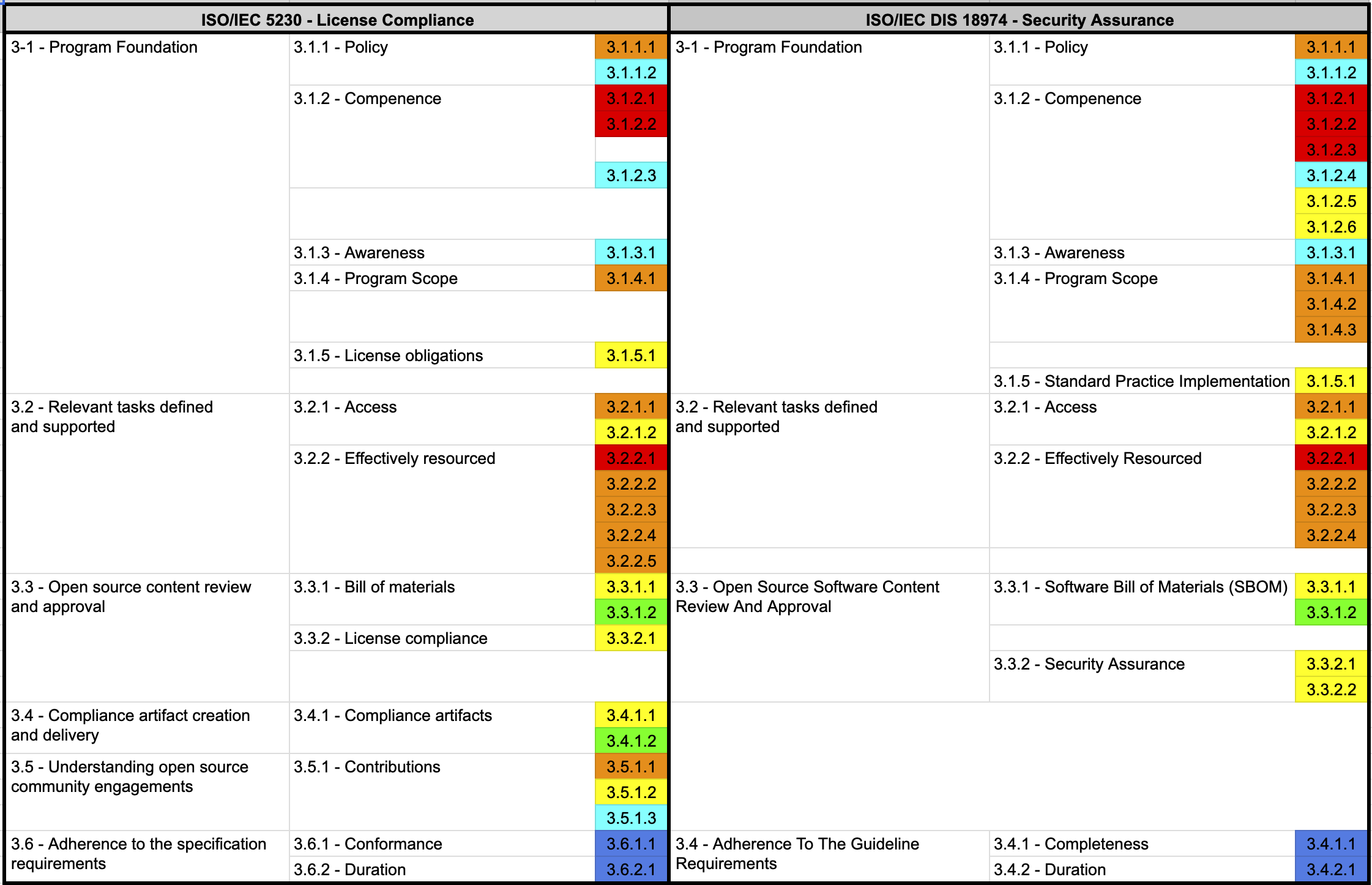
Once you have completed this, your company will finally meet all the requirements of ISO/IEC 5230, ISO/IEC 18974.
2 - NIPA OpenChain Guide
OpenUP conducted research under the supervision of the National Information and Communication Industry Promotion Agency (NIPA) and produced a guidebook explaining detailed methods for companies to comply with the OpenChain Specification. : OpenChain 2.0 Guide for Open Source Governance in the Enterprise

With the permission of NIPA, the contents of the guide are published on GitHub, and anyone can refer to the contents, modify / improve the contents.
References
Language
This page contains only Korean language materials for Korean companies.
2.1 - I. OpenChain Project란?
오늘날 소프트웨어는 갈수록 그 규모와 복잡도가 커지고 있다. 하나의 소프트웨어를 개발하기 위해서는 자체 개발하는 소프트웨어뿐 아니라 오픈소스, 3rd party Software, 반도체 벤더의 SDK 등 소프트웨어 공급망에 걸친 다양한 소프트웨어가 사용될 수 있기 때문이다.
이러한 복잡한 소프트웨어 공급망의 조직 중 한 곳이라도 라이선스 의무를 준수하지 않거나, 올바른 오픈소스 정보를 제공하지 못한 경우, 최종 소프트웨어를 배포하는 기업은 라이선스 준수에 실패하고 이로 인해 제품 판매가 중단되는 상황이 발생할 수 있다. 실제로 2009년 12월, Busybox라는 오픈소스 관련된 소송이 있었다. Busybox는 임베디드 시스템에 광범위하게 사용되고 있는 GPL-2.0 라이선스가 적용된 오픈소스인데, 두 곳의 국내 회사를 포함하여 총 14개 회사가 소송 대상이 되었다. 이 사례에서 주목할만한 점은 이 중에는 제품을 직접 개발하지 않고 배포만 한 회사도 소송을 당했다는 점이다.
이와 같은 복잡한 소프트웨어 공급망 환경에서는 어느 한 기업이 아무리 훌륭한 프로세스를 갖추고 있다고 해도 자체적으로 완벽한 오픈소스 컴플라이언스를 달성하는 건 매우 어렵다. 결국 소프트웨어를 최종 배포하는 기업이 오픈소스 컴플라이언스를 제대로 이행하기 위해서는 소프트웨어 공급망의 모든 구성원이 라이선스 의무를 준수하고 올바른 오픈소스 정보를 제공하여 공급망 전체에 신뢰가 구축되어야 한다.
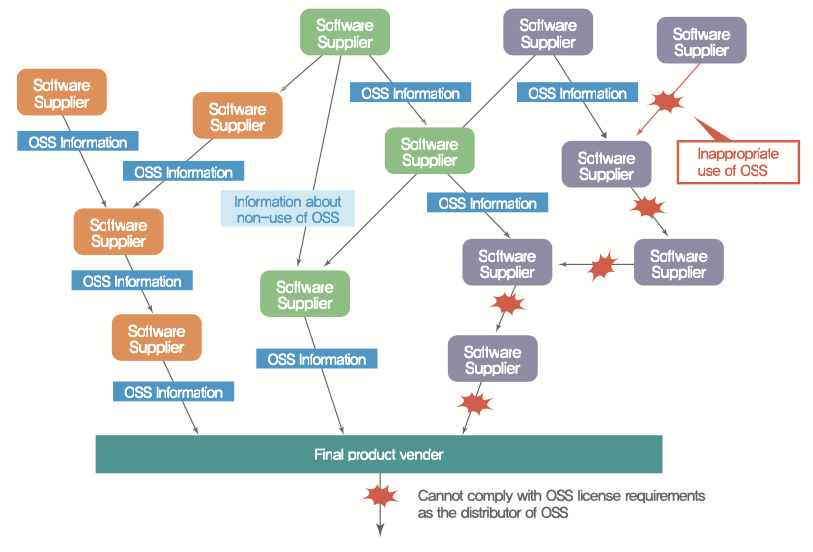
Linux Foundation의 OpenChain 프로젝트는 기업이 오픈소스 컴플라이언스를 위해 준수해야 할 활동을 더 간단하고 일관성 있게 만들어 소프트웨어 공급망 전체에 신뢰를 구축할 수 있도록 해준다.

2016년 유럽의 한 오픈소스 콘퍼런스에서 퀄컴의 오픈소스 변호사인 데이브 머(Dave Marr)는 한 기업의 오픈소스 컴플라이언스 수준을 높이기 위해서는 소프트웨어 공급망 내의 모든 구성원이 오픈소스 컴플라이언스 수준을 높이는 것이 중요함을 강조한 바 있다. 아울러 이를 위해서는 오픈소스를 충분히 이해하고, 정책 및 프로세스를 앞서 구축하고 있는 기업들이 자신들의 자산과 노하우를 공개해 누구나 이를 참고할 수 있게 해야 한다는 의견을 제시했다. 콘퍼런스 참석자들은“오픈소스 컴플라이언스는 기업의 이익을 차별화할 수 있는 분야가 아니다. 기업은 최소한의 리소스를 투입하여 적정한 수준의 리스크 관리를 원하기 때문에 기업들이 가진 자산을 공유하면 할수록 적은 비용으로 모두 함께 컴플라이언스를 달성 할 수 있다”는 아이디어에 공감했다. OpenChain 프로젝트(당시에는 Work Group)는 그렇게 시작됐고, Qualcomm, Siemens, Wind River, ARM, Adobe 등 다수 글로벌 기업들이 참여했다.
2.1.1 - 1. OpenChain Specification
OpenChain 프로젝트는 곧 OpenChain Specification 1.0을 제작하여 배포했다. OpenChain Specification은 오픈소스 컴플라이언스를 위한 핵심 요구사항을 정의한 12페이지 분량의 표준 규격으로, 기업의 규모나 업종과 관계없이 모든 분야의 회사에 적합하도록 고안되었다. 2019년 4월에는 버전 2.0의 Specification이 배포됐으며, 기업이 오픈소스 컴플라이언스 달성을 위해 꼭 수행해야 할 여섯 가지 주요 요건에 대한 설명과 이를 수행하고 있음을 입증하기 위한 검증 자료 목록을 정의하고 있다.
- 오픈소스 컴플라이언스를 관리하기 위한 프로그램
- 효과적인 리소스 제공을 위한 업무 정의 및 지원
- 오픈소스 검토 및 승인을 관리하는 프로세스
- 컴플라이언스 결과물 생성 및 제공을 위한 프로세스
- 오픈소스 커뮤니티 참여를 이해하고 관리하기 위한 정책
- OpenChain Specification 요건 준수
오픈소스 컴플라이언스를 처음 시작하는 기업이라면 이와 같은 OpenChain Specification의 요건을 하나씩 충족해가면서 수준을 향상시키는 것이 좋은 전략이다.

2.1.2 - 2. OpenChain Conformance
OpenChain Project는 기업이 OpenChain Specification을 충족하는지 자체적으로 확인할 수 있도록 온라인 자체 인증 웹사이트를 제공한다.

기업의 오픈소스 담당자는 OpenChain 자체 인증 웹사이트에 가입해 온라인 자체 인증을 시작할 수 있으며, Yes/No 질문에 답변하는 방식으로 진행된다.

자체 인증을 통해 부족한 부분이 무엇인지, 추가로 필요한 활동이 무엇인지 판단할 수 있다.
만약, 오픈소스 컴플라이언스 체계가 잘 구축된 기업이 OpenChain 자체 인증 질문지의 모든 항목을 Yes로 대답할 수 있다면 이 결과를 웹사이트상에 제출할 수 있다(Conforming Submission). 그러면 OpenChain 준수(Conformant) 기업으로 인정됨과 동시에, OpenChain 프로젝트의 웹사이트에서 OpenChain 준수 프로그램을 갖춘 기업 목록에 기업의 로고를 등록할 수 있게 된다.

OpenChain 준수 기업에게는 OpenChain 로고를 사용할 수 있는 자격이 주어진다. 이렇게 OpenChain 준수 프로그램을 갖췄다고 인정받은 기업은 소프트웨어 공급망 내에서 오픈소스 컴플라이언스를 충실하게 수행하고 있음을 보여줄 수 있다.

2.1.3 - 3. OpenChain Curriculum
OpenChain 프로젝트에서는 기업이 컴플라이언스 프로그램을 구축하는데 필요한 정책 문서 템플릿, 교육 자료 등 다양한 참고자료를 제공한다. 이 자료들은 OpenChain Specification 및 일반적인 오픈소스 컴플라이언스 활동을 지원하기 위해 고안됐으며, 누구나 자유롭게 사용할 수 있도록 Public Domain으로 제공된다.

2.2 - II. OpenChain Specification 준수 방법
OpenChain Specifiation에서는 오픈소스 컴플라이언스를 위한 핵심 요구 사항을 정의한다. OpenChain Specification을 준수한다고 인정받은 기업은 소프트웨어 솔루션을 배포하는 조직간에 신뢰를 제공할 수 있게 된다. 여기에서는 기업들이 OpenChain Specification을 준수하기 위해 충족해야 하는 여섯가지 주요 요건과 그 방법을 세부적으로 설명한다.
2.2.1 - 1. 프로그램 성립
1.1 정책 (Policy)
오픈소스를 이용하여 소프트웨어를 개발하고 배포하는 기업이라면 오픈소스를 관리하기 위한 정책과 프로세스를 구축하고, 이를 위한 인력과 자원을 할당해야 한다. OpenChain에서는 이러한 일련의 활동을 관리하는 체계를 오픈소스 프로그램이라고 부르고, OpenChain Specification을 준수하기 위한 첫번째 요건은 바로 이 프로그램을 설립해야 하는것이다. 여기서 오픈소스 프로그램이란 정책, 프로세스, 인원 등 기업이 오픈소스 컴플라이언스 활동을 수행하기 위한 일련의 관리 체계를 의미한다. OpenChain Specification에서는 이를 입증하기 위한 자료로 우선 문서화된 오픈소스 정책을 요구한다. 이 안내서에서는 참고를 위해 OpenChain Specification의 요건을 충족하는 오픈소스 정책 문서 예시를 “[부록 01] 샘플 오픈소스 정책”에서 제공한다.
OpenChain Specification은 이어지는 장에서 오픈소스 프로그램이 갖춰야할 요건들을 설명하고 있다.
OpenChain Specification 2.0
1.1 정책
공급 대상 소프트웨어의 오픈소스 라이선스 컴플라이언스를 관리하는 문서화 된 오픈소스 정책이 존재한다. 정책은 내부적으로 전달되어야 한다.
입증 자료:
1.1.1 문서화 된 오픈소스 정책
1.1.2 소프트웨어 공급 담당자가 오픈소스 정책의 존재를 인식하도록 하는 문서화 된 절차 (교육, 내부 위키, 혹은 기타 실질적인 의사소통 방법 등)
1.1 Policy
A written Open Source policy exists that governs Open Source license compliance of the Supplied Software. The policy must be internally communicated.
Verification Material(s):
1.1.1 A documented Open Source policy
1.1.2 A documented procedure that makes Software Staff aware of the existence of the Open Source policy (e.g., via training, internal wiki, or other practical communication method)
오픈소스 프로그램은 소프트웨어 공급담당자가 이 오픈소스 정책 문서의 존재를 알고, 필요한 활동을 할 수 있도록 교육, 내부 위키 등 실질적인 수단을 제공해야 한다. 여기서 소프트웨어 공급담당자(Software Staff)란 기업이 소프트웨어를 개발하고 배포, 기여하는데 관여하는 모든 직원을 의미하며, 소프트웨어 개발자, 배포 엔지니어, 품질 엔지니어 등을 포함한다.
많은 기업들은 오픈소스 정책 문서를 사내 위키 사이트를 통해 공개하여 직원 누구나 필요한 사항을 확인할 수 있게 한다. 또한, 신규 채용인원의 입사 연수 시 오픈소스 정책에 대한 교육을 의무화하고, 소프트웨어 공급담당자를 대상으로 매년 혹은 2년에 한번씩 주기적인 교육을 제공함으로 모든 소프트웨어 공급담당자가 오픈소스 정책의 존재를 인식하도록 할 수 있다. 이러한 방법들을 오픈소스 정책 문서에 구체화하여 포함해야 한다.
1.2 역량 (Competence)
OpenChain Specification 2.0
1.2 역량
조직은 다음 사항을 수행해야 한다: (The organization shall: )
- 프로그램의 성능 및 효과에 영향을 미치는 역할과 해당 역할에 대한 책임을 확인한다;
- 각 역할을 수행하는 인원의 필요한 역량을 파악한다;
- 해당 인원이 적절한 교육, 훈련 및 경험을 바탕으로 자격을 갖춘 자임을 보장한다;
- 해당되는 경우, 필요한 역량을 확보하기 위한 조치를 취한다;
- 적절히 문서화된 정보를 역량의 증거로 보유한다.
입증 자료:
1.2.1 프로그램 내 여러 참여자에 대한 문서화된 책임과 역할 목록
1.2.2 각 역할에 대한 역량을 확인하는 문서
1.2.3 각 프로그램 참여자에 대해 역량을 평가한 문서화된 증거
1.2 Competence
The organization shall:
- Identify the roles and the corresponding responsibilities of those roles that affects the performance and effectiveness of the Program;
- Determine the necessary competence of person(s) fulfilling each role
- Ensure that these persons are competent on the basis of appropriate education, training, and/or experience;
- Where applicable, take actions to acquire the necessary competence; and - Retain appropriate documented information as evidence of competence.
Verification Material(s):
1.2.1 A documented list of roles with corresponding responsibilities for the different participants in the Program.
1.2.2 A document that identifies the competencies for each role.
1.2.3 Documented evidence of assessed competence for each Program participant.
오픈소스 프로그램이 올바르게 구축되고 운영될 수 있도록 역할과 책임(R&R)을 정의해야 한다. 각 역할을 수행할 담당자가 갖춰야 할 역량을 정의하고, 지정된 담당자가 해당 역할을 수행할 수 있는 역량을 갖추었는지 파악해야 한다. 해당 인원이 교육, 훈련 및 경험을 바탕으로 맡은 역할을 수행할 수 있는 자격을 갖추었음을 보장해야 한다. 이를 위해 각 인원이 필요한 역량을 갖출 수 있도록 교육을 제공한다.
이를 입증하기 위해 기업은 프로그램 내 여러 참여자에 대한 책임 및 역할 목록과 각 역할을 수행하는 담당자가 갖춰야할 역량을 정의하여 문서화 한다. 이 안내서에서는 참고를 위해 오픈소스 프로그램의 각 참여자의 역할과 책임 및 필요한 역량을 정의한 샘플 문서를 “[부록 01] 오픈소스 정책 for OpenChain 2.0(예)의 4. 역할, 책임 및 역량”에서 제공한다.
그리고, 기업은 각 참여자가 역량을 갖추고 있는지 평가하고, 이를 보관한다. 이를 위해 기업은 각 참여자가 필요한 역량을 보유할 수 있도록 교육을 제공한다. 교육 내용을 기반으로 평가하고, 그 결과는 기업의 교육 시스템 혹은 HR 부서에서 보관해야 한다. 소프트웨어 공급담당자가 수천명 이상이어서 교육 제공이 쉽지 않을 경우, 기업의 온라인 교육과 평가 시스템을 이용하는 것도 좋은 방법이다.
1.3 인지도 (Awareness)
OpenChain Specification 2.0
1.3 인지도
조직은 프로그램 참여자가 다음 사항을 알고 있음을 보장해야 한다:
a) 오픈소스 정책;
b) 오픈소스 관련 목표;
c) 프로그램의 효과에 대한 기여;
d) 프로그램의 요건 미준수의 의미.
입증 자료:
1.3.1 각 프로그램 담당자에 대해 프로그램의 목표, 프로그램에 기여, 그리고 프로그램 미준수의 의미를 포함하는 인지도를 평가한 문서화된 증거.
1.3 Awareness
The organization shall ensure that Program participants are aware of:
a) The Open Source policy;
b) Relevant Open Source objectives;
c) Their contribution to the effectiveness of the Program; and
d) The implications of not following the Program’s requirements.
Verification Material(s):
1.3.1 Documented evidence of assessed awareness for each Program personnel including the Program’s objectives, ones contribution within the Program, and implications of Program non-conformance.
프로그램 참여자가 오픈소스 정책, 기업의 오픈소스 관련 목표, 오픈소스 프로그램이 효과적일 수 있도록 참여자의 기여 방법, 그리고 프로그램 요건을 준수하지 않았을 때의 발생할 수 있는 위험에 대해 인식하도록 한다.
이를 위해 오픈소스 정책은 프로그램 참여자가 오픈소스 정책 등의 주요 내용을 인식할 수 있도록 다음의 내용을 포함해야 한다.
- 먼저, 오픈소스를 사용, 배포, 기여하는 일련의 활동을 수행하는 목표를 포함한다. 예를 들어,“오픈소스를 이용하여 제품을 만들때 오픈소스 컴플라이언스 리스크를 최소화하고, 오픈소스 커뮤니티에 참여하고 기여함으로 최고의 가치를 창출한다”와 같은 형태로 목표를 수립할 수 있다.
- 그리고, 프로그램 참여자가 자신의 역할에 대한 책임을 완수함으로써 오픈소스 프로그램의 효과가 증대될 수 있음을 알린다.
- 또한, 오픈소스 프로그램의 요건들을 준수하지 않았을 때 어떠한 위험이 발생하는지에 대해서도 알린다.
대표적인 위험 요소는 다음과 같다.
- 사용한 코드의 저작권자로부터 법적 클레임
- 의도하지 않은 기업 독점 코드의 공개
- 라이선스 의무 위반으로 인한 벌금
- 평판 손실
- 수익 손실
- 공급업체 및 고객과의 계약 위반
각 프로그램 담당자가 프로그램의 목표, 프로그램에 기여 방법, 프로그램 미준수의 의미에 대해 올바르게 인식할 수 있도록 교육을 제공하고, 이를 평가한다. 평가한 결과는 문서화하여 보관한다. 1.2장에서 언급한 교육 및 평가 시 이에 대한 내용을 포함하면 될 것이다.
1.4 프로그램 적용 범위 (Program Scope)
OpenChain Specification 2.0
1.4 프로그램 적용 범위
서로 다른 프로그램들은 서로 다른 수준의 범위까지 적용될 수 있다. 예를 들어, 하나의 프로그램이 하나의 제품 라인, 전체 부서 또는 전체 조직을 관리할 수 있다. 각 프로그램별로 범위 지정이 이루어질 필요가 있다.
입증 자료:
1.4.1 프로그램의 적용 범위와 한계를 명확하게 정의한 문서화된 진술.
1.4 Program Scope
Different Programs may be governed by different levels of scope. For example, a program could govern a single product line, an entire department or an entire organization. The scope designation needs to be declared for each Program.
Verification Material(s):
1.4.1 A written statement that clearly defines the scope and limits of the Program.
오픈소스 프로그램은 반드시 기업 전체에 적용해야 하는 것은 아니다. 기업 내 각 조직의 특성에 따라 프로그램의 적용 범위를 달리 할 수 있다. 예를 들어, 소프트웨어를 전혀 배포하지 않는 조직이라면 오픈소스 프로그램의 적용 범위에 해당하지 않을 수 있다. 따라서, 기업의 오픈소스 정책은 오픈소스 프로그램의 적용 범위와 한계를 명확히 정의해야 한다.
예를 들어, “이 오픈소스 정책은 회사가 외부에 배포하는 모든 제품에 적용한다. 향후 배포하는 제품의 형태에 따라 프로그램의 구성과 적용 범위가 달라질 수 있으며, 이에 대해서는 오픈소스 팀이 OSRB와의 협의를 통해 결정한다.”와 같은 형태로 프로그램 적용 범위를 정의할 수 있다.
1.5 라이선스 의무 (License Obligations)
OpenChain Specification 2.0
1.5 라이선스 의무
각 라이선스에 의해 부여된 의무, 제한 및 권리를 결정하기 위해 식별된 라이선스를 검토하는 프로세스가 존재한다.
입증 자료:
1.5.1 각 식별된 라이선스에 의해 부과되는 의무, 제한 및 권리를 검토하고 문서화하기 위한 문서화된 절차.
1.5 License Obligations
A process exists for reviewing the Identified Licenses to determine the obligations, restrictions and rights granted by each license.
Verification Material(s):
1.5.1 A written statement that clearly defines the scope and limits of the Program.
오픈소스의 사용 가능 여부를 판단하기 위해서는 먼저 오픈소스의 라이선스가 무엇인지 식별하고, 라이선스가 요구하는 의무사항을 검토하고 확인해야 한다. 오픈소스 프로그램은 소프트웨어 개발팀에서 오픈소스 라이선스가 부여하는 의무, 제한 및 권리를 검토할 수 있도록 오픈소스 라이선스 의무 요약 자료를 제공하는 것이 좋다. 공개SW 라이선스(https://www.oss.kr/oss_license )에서는 주요 오픈소스 라이선스의 의무, 제한 및 권리를 자세히 설명한다.
오픈소스를 사용하기에 앞서 라이선스 검토하고 이를 문서화하는 절차는“[부록 02] 오픈소스 컴플라이언스 프로세스 (예시)”절차의 오픈소스 식별 단계에 해당한다.
2.2.2 - 2. 관련 업무 정의 및 지원
2.1 접근성 (Access)
OpenChain Specification 2.0
2.1 접근성
외부 오픈소스 문의에 효과적으로 대응할 수 있는 프로세스를 유지한다. 제 3자가 오픈소스 컴플라이언스 문의를 할 수 있는 방법을 공개적으로 밝힌다.
입증 자료:
2.1.1 제 3자가 오픈소스 컴플라이언스 문의를 할 수 있게 공개적으로 알려진 방법 (공개된 연락처 이메일 주소, 또는 Linux Foundation의 Open Compliance Directory 등).
2.1.2 제 3자의 오픈소스 라이선스 컴플라이언스 문의에 대응하기 위한 내부의 문서화된 절차.
2.1 Access
Maintain a process to effectively respond to external Open Source inquiries. Publicly identify a means by which a third party can make an Open Source compliance inquiry.
Verification Material(s):
2.1.1 Publicly visible method that allows any third party to make an Open Source license compliance inquiry (e.g., via a published contact email address, or the Linux Foundation’s Open Compliance Directory).
2.1.2 An internal documented procedure for responding to third party Open Source license compliance inquiries.
배포한 제품에 사용된 오픈소스에 대해 고객 및 오픈소스 저작권자가 기업에게 오픈소스 관련 문의, 요청 및 클레임을 제기하는 경우가 있다. 소송까지 당하지 않기 위해서는 이러한 외부 문의에 가능한 빠르고 정확하게 대응하는 것이 중요하다. 따라서 기업은 외부에서 기업에게 오픈소스 관련 문의를 할 수 있는 연락 방법을 공개적으로 밝히고, 외부 오픈소스 문의를 접수하였을 때 빠르고 효과적으로 대응 할 수 있는 프로세스를 갖추고 있어야 한다.
외부에서 기업에게 오픈소스 관련 문의를 할 수 있는 연락 방법은 회사의 오픈소스 담당자의 이메일 주소를 공개하거나, Linux Foundation의 Open Compliance Directory를 이용하는 것이다.
오픈소스 개발자들이 기업의 오픈소스 컴플라이언스 관련 이슈를 논의하기 위해 기업 담당자에게 연락하고 싶어도 연락 방법을 찾지 못하다가 결국 법적 클레임까지 제기하는 경우가 있다. Linux Foundation은 이러한 경우를 최소화 하기 위해 기업들에게 오픈소스 관련 문의를 받을 수 있는 연락처를 공개할 수 있도록 Open Compliance Directory라는 공간을 마련하였다.

이를 통해 오픈소스 개발자들은 원하는 기업의 컨택 포인트 정보를 쉽게 확인할 수 있고, 법적 클레임까지 제기하기 이전에 기업의 오픈소스 담당자와 오픈소스 컴플라이언스 이슈를 논의하여 문제를 해결할 수 있다. 기업의 오픈소스 담당자는 Open Compliance Directory에 기업 정보 및 연락 방법을 등록하는 것이 소송 리스크를 줄일 수 있는 방법 중 하나이다.

외부 문의 및 요청의 주된 내용은 다음과 같다.
- 특정 오픈소스가 제품 및 서비스에 사용되었는지 확인 요청
- Written Offer에서 언급된 GPL, LGPL 등의 라이선스 하의 소스 코드 제공 요청
- 오픈소스 고지문에 명시되지 않았지만 제품에서 발견된 오픈소스에 대한 해명 및 소스 코드 공개 요청
- GPL, LGPL 등의 의무로 공개된 소스 코드에 누락된 파일 제공 요청
- Copyright 표시 요청
외부로부터의 이러한 오픈소스 컴플라이언스 문의에 신속하고 정확하게 대응한다면 소송까지 진행되는 위험을 크게 줄일 수 있다. 따라서, 기업은 외부의 오픈소스 컴플라이언스 문의에 대응하기 위한 절차를 갖고 있어야 한다. 컴플라이언스 문의를 대응하기 위한 일반적인 절차는 다음과 같다.

- 접수 확인 (Acknowledge) 문의를 받으면 즉시 응답하여, 문의가 제대로 접수되었음을 알린다. 이때 조치 예정일을 함께 알린다. 요청자의 의도가 무엇인지 정확히 파악하는 것이 중요하기 때문에 문의가 불명확한 경우 추가 설명을 요청한다.
- 요청자에게 알림 (Inform) 요청자에게 오픈소스 컴플라이언스를 충실히 수행하고 있음과 요청자의 문의에 대해 조사하고 있음을 알린다. 내부 조사 진행사항이 업데이트되면 알리는 것이 좋다.
- 내부 조사 (Investigate) 문의에 대해 내부 조사를 진행한다. 문제가 된 제품의 버전에 대하여 컴플라이언스 프로세스가 적절하게 수행되었는지 BOM 및 문서화 된 검토 이력을 통해 확인한다.
- 요청자에게 보고 (Report) 요청자에게 통보했던 조치 예정일 내에 내부 조사를 마치고, 이에 대한 내부 기록을 남긴 후 요청자에게 결과를 알린다.
- 처리 종료 (Close Inquiry) 요청자의 문의가 오해로 인한 잘못된 지적이나 요청이었다면 추가 조치 없이 요청자에게 이를 알리고 처리를 종료한다.
- 문제 보완 (Rectify) 내부조사에서 실제 컴플라이언스 문제가 발견되면 해당 조직은 제품 또는 서비스의 컴플라이언스 문제를 해결하기 위해 필요한 모든 절차를 수행한다. 예상되는 완료 일자를 요청자에게 다시 한번 알린다. 즉, 해당 오픈소스 라이선스의 의무를 이행하기 위한 정확한 방법과 시기를 알려야 한다. 문제를 해결한 후에는 즉시 요청자에게 알리고 문제가 해결되었음을 확인할 수 있는 최선의 방법을 제공한다.
- 프로세스 개선 (Improve) 컴플라이언스 문제가 있었던 경우, OSRB 미팅을 통해 사례를 검토하고, 문제가 발생한 경위를 파악하여, 문제가 재발하지 않을 수 있도록 프로세스를 개선한다.
2.2 효과적인 리소스 제공 (Effectively Resourced)
OpenChain Specification 2.0
2.2 효과적인 리소스 제공
프로그램 업무를 확인하고 리소스를 제공하라:
- 프로그램 업무를 성공적으로 수행할 수 있도록 책임을 할당하라.
- 프로그램 업무를 위해 충분한 리소스가 제공된다:
• 업무를 수행할 시간이 할당되었다;
• 적절한 자금이 할당되었다. - 정책 및 지원 업무를 검토하고 업데이트하는 프로세스가 존재한다;
- 오픈소스 라이선스 컴플라이언스와 관련된 법률 가이드를 필요로 하는 인원이 법률 전문 지식을 이용할 수 있다;
- 오픈소스 라이선스 컴플라이언스 문제를 해결하기 위한 프로세스가 존재한다.
입증 자료:
2.2.1 확인된 프로그램 역할의 담당자 이름, 그룹 또는 기능이 기재된 문서
2.2.2 확인된 프로그램 역할이 적절하게 충원되었고 적합하게 자금이 제공되었다
2.2.3 오픈소스 라이선스 컴플라이언스 문제를 해결하기 위해 내부 또는 외부의 전문 법률 지식을 이용할 수 있는 방법의 확인.
2.2.4 오픈소스 컴플라이언스에 대한 내부 책임을 할당하는 문서화된 절차 2.2.5 미준수 사례의 검토 및 시정을 규정하는 문서화된 절차
2.2 Effectively Resourced
Identify and Resource Program Task(s):
- Assign accountability to ensure the successful execution of Program tasks.
- Program tasks are sufficiently resourced:
• Time to perform the tasks have been allocated; and
• Adequate funding has been allocated. - A process exists for reviewing and updating the policy and supporting tasks;
- Legal expertise pertaining to Open Source license compliance is accessible to those who may need such guidance; and
- A process exists for the resolution of Open Source license compliance issues.
Verification Material(s):
2.2.1 Document with name of persons, group or function in Program role(s) identified.
2.2.2 The identified Program roles have been properly staffed and adequate funding provided.
2.2.3 Identification of legal expertise available to address Open Source license compliance matters which could be internal or external.
2.2.4 A documented procedure that assigns internal responsibilities for Open Source compliance.
2.2.5 A documented procedure for handling the review and remediation of non-compliant cases.
기업은 오픈소스 프로그램이 원활하게 기능을 수행할 수 있도록 리소스를 충분하게 제공해야 한다.
- 프로그램 참여자들이 업무를 수행할 수 있는 시간과 자금을 할당하고, 주기적으로 오픈소스 정책을 검토하여 기업의 소프트웨어 전략에 맞추어 업데이트해야 한다.
- 프로그램 참여자들이 컴플라이언스 이슈 해결을 위한 프로세스가 구축되어야 하고, 이슈 해결을 위해 법적인 검토가 필요할 경우 법무 자문을 요청할 수 있는 방법이 제공되어야 한다.
오픈소스 프로그램이 기능을 수행하기 위해서는 각 역할 별 담당자가 지정되어야 한다.
- 각 역할 별 담당자 혹은 담당 조직을 지정하고, 누구나 이를 참고할 수 있도록 문서화하여 공유한다.
- 각 조직의 책임자는 프로그램 내의 각 역할별 담당자가 적절히 충원되었는지, 업무를 수행하는데 필요한 자금이 적절하게 제공되었는지를 확인한다.
만약, 프로그램 참여자가 자신의 역할을 수행하는데 리소스나 자금 지원이 부족하다고 판단한다면, 반드시 기업의 오픈소스 책임자에게 문제를 제기하여 해결해야 한다. 문제가 효과적으로 해결되지 않을 경우, 오픈소스 이사회에 보고하고, 이사회는 필요한 의사결정을 수행하여 적절한 자원이 할당 될 수 있도록 해야 한다.
기업은 프로그램 참여자가 이슈 해결을 위해 법률적인 검토가 필요할 경우, 이에 대해 법률 자문을 요청할 수 있는 방법을 제공해야 한다. 회사 내의 법무팀을 통해 우선 제공하고, 이슈가 첨예한 경우, 오픈소스 전문 변호사를 보유한 외부 법무 법인을 이용할 수 있다. OpenChain Project에서는 파트너 프로그램을 통해 오픈소스 관련 자문을 제공하는 글로벌 법무법인 리스트를 제공한다.

OpenChain 파트너로 등록된 법무법인은 OpenChain Project에서 요구하는 요건을 충족한 곳들이며, 대한민국에서는 법무법인 태평양이 등록되어 있다.
오픈소스 책임자는 기업의 오픈소스 컴플라이언스 활동을 위한 기업 내부의 역할과 책임을 할당해야 한다. 오픈소스 정책 문서에는 오픈소스 책임자가 오픈소스 컴플라이언스 이슈 해결을 위해 담당해야 할 역할에 대해 기술한다.
컴플라이언스 미준수 이슈가 제기된 경우, 기업은 이를 신속히 검토하고 대응하기 위한 절차를 문서화해야 한다. 이에 대한 자세한 내용은 2.1장에서 외부 문의 대응에 대한 프로세스 설명 부분을 참고할 수 있다.
2.2.3 - 3. 오픈소스 콘텐츠 검토 및 승인
3.1 BOM (Bill of Materials)
OpenChain Specification 2.0
3.1 BOM
공급 대상 소프트웨어를 구성하는 각 오픈소스 컴포넌트(및 식별된 라이선스)를 포함하는 BOM을 작성하고 관리하는 프로세스가 있다.
입증 자료:
3.1.1 공급 대상 소프트웨어를 구성하는 오픈소스 컴포넌트 모음에 대한 정보를 식별, 추적, 검토, 승인 및 보관하는 문서화된 절차
3.1.2 공급 대상 소프트웨어에 대해 문서화된 절차가 적절히 준수되었음을 입증하는 오픈소스 컴포넌트 기록.
3.1 Bill of Materials
A process exists for creating and managing a bill of materials that includes each Open Source component (and its Identified Licenses) from which the Supplied Software is comprised.
Verification Material(s):
3.1.1 A documented procedure for identifying, tracking, reviewing, approving, and archiving information about the collection of Open Source components from which the Supplied Software is comprised.
3.1.2 Open Source component records for the Supplied Software that demonstrates the documented procedure was properly followed.
오픈소스 컴플라이언스 활동의 가장 기본은 바로 공급 대상 소프트웨어에 포함된 오픈소스 현황을 파악하는 것이다. 공급 대상 소프트웨어에 포함된 오픈소스와 그 라이선스를 식별하여 그 정보를 담고있는 BOM을 작성하고 관리하는 프로세스를 구축해야 한다. 공급 대상 소프트웨어마다 어떤 오픈소스가 포함되어 있는지 알고 있어야 소프트웨어를 배포할 때 각 라이선스가 요구하는 의무 사항을 준수할 수 있기 때문이다. 모든 오픈소스는 배포 대상 소프트웨어에 통합하기 전에 검토 및 승인되어야 한다. 오픈소스의 기능, 품질 뿐만 아니라 출처, 라이선스 요건을 충족하는지 검토가 되야 한다. 이를 위해 검토 요청 → 리뷰 → 승인 과정이 필요하다. [부록 02]에서는 기업의 오픈소스 컴플라이언스를 위한 프로세스 전과정에 대해 설명하고 있다. 식별부터 등록까지의 과정을 통해 BOM을 작성하고 관리하게 된다.
{% page-ref page="../../appendix/process.md" %}
공급 대상 소프트웨어에 포함된 오픈소스 목록은 문서화하여 보관해야 한다. Eclipse 재단에서 후원하는 오픈소스 프로젝트인 SW360(https://projects.eclipse.org/proposals/ sw360)은 공급 대상 소프트웨어별로 포함하고 있는 오픈소스 목록을 트래킹할 수 있는 기능을 제공한다. SW360 사용 방법은 [부록 03]을 참고할 수 있다.
오픈소스 컴플라이언스 프로세스의 모든 과정과 결과는 문서화가 되어야 한다. 이메일을 사용하는 것 보다는 Jira, Bugzilla 등의 이슈 트래킹 시스템을 이용하는 것이 이러한 과정을 효율적으로 문서화 할 수 있다.
3.2 라이선스 컴플라이언스
OpenChain Specification 2.0
3.2 라이선스 컴플라이언스
프로그램은 공급 대상 소프트웨어에 대해 소프트웨어 공급 담당자가 접하게 되는 일반적인 오픈소스 사용 사례를 관리할 수 있어야 하며, 다음과 같은 사례가 포함될 수 있다(이 목록이 완전한 것은 아니며, 모든 사용 사례가 적용되어야 하는 것은 아니다).:
- 바이너리 형태로 배포;
- 소스 형태로 배포;
- Copyleft 의무를 발생시킬 수 있는 다른 오픈소스와 통합;
- 수정한 오픈소스를 포함;
- 공급 대상 소프트웨어 내에서 상호 작용하는 다른 컴포넌트와 호환되지 않는 라이선스 하의 오픈소스 또는 기타 소프트웨어를 포함; - 저작자 표시 요건이 있는 오픈소스를 포함.
입증 자료:
3.2.1 공급 대상 소프트웨어의 오픈소스 컴포넌트에 대해 일반적인 오픈소스 라이선스 사용 사례를 처리하기 위한 문서화된 절차.
3.2 License Compliance
The Program must be capable of managing common Open Source license use cases encountered by Software Staff for Supplied Software, which may include the following use cases (note that the list is neither exhaustive, nor may all of the use cases apply):
- distributed in binary form;
- distributed in source form;
- integrated with other Open Source such that it may trigger copyleft obligations;
- contains modified Open Source;
- contains Open Source or other software under an incompatible license interacting with other components within the Supplied Software; and/or - contains Open Source with attribution requirements.
Verification Material(s):
A documented procedure for handling the common Open Source license use cases for the Open Source components of the Supplied Software.
오픈소스 라이선스를 제대로 준수하기 위해서는 오픈소스 라이선스 별로 요구하는 사항에 대해 정확히 알고 있어야 한다. 개별 소프트웨어 개발자가 이를 일일이 파악하는 것은 어렵기 때문에 오픈소스 책임자는 자주 사용되는 오픈소스 라이선스 들에 대해 일반적인 사용 사례별 요구사항/주의사항을 정리하여 회사 내부에 공유하는 것이 좋다. 오픈소스 책임자는 자주 사용되는 오픈소스 라이선스별로 일반적인 사용 사례에 대한 의무 요약 자료를 제공한다. 오픈소스 라이선스에 대한 일반적인 가이드와 라이선스 의무 요약 자료는 NIPA에서 제공하는“공개SW 라이선스 가이드”를 참고할 수 있다. (https://www.oss.kr/oss_license)
[부록 2] 오픈소스 컴플라이언스 프로세스 (예시)의 오픈소스 컴플라이언스 프로세스의 식별, 검사, 문제해결, 리뷰, 승인 단계를 통해 공급 대상 소프트웨어의 오픈소스 컴포넌트에 대해 일반적인 오픈소스 라이선스 사용 사례를 처리할 수 있다.
식별 및 검사 단계에서는 소스코드 스캔 도구를 사용할 수 있다. 소스코드 스캔 도구는 무료로 사용할 수 있는 오픈소스 기반 도구부터 상용 도구까지 다양하게 있다. 각 도구들은 특장점 들이 있지만 어떤 하나도 모든 문제를 해결할 수 있는 완벽한 기능을 제공하지 않는다. 따라서 기업은 제품의 특성과 요구사항에 맞는 적합한 도구를 선택해야 한다. 많은 기업들이 이러한 자동화된 소스 코드 스캔 도구와 수동 검토를 병행하여 이용한다. Linux Foundation의 FOSSology Project는 오픈소스로 공개된 소스 코드 스캔 도구로서 기업들이 손쉽게 무료로 사용할 수 있다. 사용 방법은 [부록 03] 오픈소스도구 (FOSSology, SW360)을 참고할 수 있다.
2.2.4 - 4. 컴플라이언스 결과물 생성 및 전달
OpenChain Specification 2.0
4.1 컴플라이언스 결과물
공급 대상 소프트웨어에 대한 컴플라이언스 결과물 세트를 생성하는 프로세스가존재한다.
입증 자료:
4.1.1 식별된 라이선스에서 요구하는 대로 컴플라이언스 결과물을 준비하고 공급 대상 소프트웨어와 함께 배포하기 위한 프로세스를 설명하는 문서화된 절차.
4.1.2 공급 대상 소프트웨어의 컴플라이언스 결과물 사본을 보관하기 위한 문서화된 절차 - 보관 파일은 공급 대상 소프트웨어의 마지막 제공 이후 적절한 기간(혹은 식별된 라이선스가 요구하는 기간 (둘 중 더 긴 시간)) 동안 보관되어야 한다. 절차가 올바르게 지켜졌음을 입증하는 기록이 존재한다.
4.1 Compliance Artifacts
A process exists for creating the set of Compliance Artifacts for the Supplied Software.
Verification Materials(s):
4.1.1 A documented procedure that describes the process under which the Compliance Artifacts are prepared and distributed with the Supplied Software as required by the Identified Licenses.
4.1.2 A documented procedure for archiving copies of the Compliance Artifacts of the Supplied Software - where the archive is planned to exist for a reasonable period of time since the last offer of the Supplied Software; or as required by the Identified Licenses (whichever is longer). Records exist that demonstrate the procedure has been properly followed.
3.1장에서 오픈소스 컴플라이언스 활동의 가장 기본은 공급 대상 소프트웨어에 포함된 오픈소스 현황을 파악하는 것이라고 하였다. 이는 바로 오픈소스 컴플라이언스의 핵심인 오픈소스 라이선스의 의무를 파악하여 요건들을 충족하기 위해서이다. 즉, 공급 대상 소프트웨어에 포함된 것으로 식별한 오픈소스에 대한 컴플라이언스 결과물 세트를 생성하는 프로세스가 구축되어야 한다.
컴플라이언스 결과물은 크게 두가지로 구분된다.
- 오픈소스 고지문 : 오픈소스 라이선스 전문과 Copyright 정보 제공을 위한 문서
- 공개할 소스코드 패키지 : GPL, LGPL 등 소스 코드 제공을 요구하는 오픈소스 라이선스 의무 이행을 위해 공개할 소스코드를 취합한 패키지
컴플라이언스 결과물은 공급 대상 소프트웨어를 배포할 때 함께 제공해야 한다.“[부록 02] 오픈소스 컴플라이언스 프로세스(예시)”의 고지, 확인, 배포 단계를 통해 컴플라이언스 결과물을 생성하여 배포한다.
공급 대상 소프트웨어를 배포 시, 공개할 소스코드 패키지를 동봉하는 것이 곤란할 경우, 최소 3년간 소스코드를 제공하겠다는 서면 약정서(Written Offer)를 제공하는 것으로 대신할 수 있다. 일반적으로 서면 약정서는 제품의 사용자 매뉴얼을 통해 제공하며, 예시는 다음과 같다.
The software included in this product contains copyrighted software that is licensed under the GPL. A copy of that license is included in this document on page X. You may obtain the complete Corresponding Source code from us for a period of three years after our last shipment of this product, which will be no earlier than 2011-08- 01, by sending a money order or check for $5 to:
GPL Compliance Division
Our Company
Any Town, US 99999Please write“source for product Y” in the memo line of your payment.
You may also find a copy of the source at http://www.example.com/sources/Y/.
This offer is valid to anyone in receipt of this information.
따라서, 컴플라이언스 결과물은 3년 이상 보관해야 하며 이를 위한 프로세스가 구축되어야 한다. 기업들은 자체적인 웹사이트(예: http://opensource.lge.com/) 구축하여 외부 고객들이 공급 대상 소프트웨어에 대한 오픈소스 고지문과 공개할 소스코드 패키지를 언제든지 다운받을 수 있도록 편의를 제공한다.
2.2.5 - 5. 오픈소스 커뮤니티 참여에 대한 이해
5.1 기여 (Contributions)
OpenChain Specification 2.0
5.1 기여
조직이 오픈소스 프로젝트에 기여를 고려한다면
- 오픈소스 프로젝트에 대한 기여를 관리하는 문서화된 정책이 존재한다;
- 이 정책이 내부적으로 전달되어야 한다;
- 정책을 구현하는 프로세스가 존재한다.
입증 자료:
조직이 오픈소스 프로젝트에 대한 기여를 허용한다면 다음이 존재해야 한다:
5.1.1 문서화된 오픈소스 기여 정책;
5.1.2 오픈소스 기여를 관리하는 문서화된 절차;
5.1.3 모든 소프트웨어 공급 담당자가 오픈소스 기여 정책의 존재를 인식하도록 하는 문서화된 절차 (교육, 내부 위키, 또는 기타 실질적인 의사소통 방법 등).
5.1 Contributions
If an organization considers contributions to Open Source projects then
- a written policy exists that governs contributions to Open Source projects;
- the policy must be internally communicated; and
- a process exists that implements the policy
Verification Materials(s):
If an organization permits contributions to Open Source projects then the following must exist:
- 5.1.1 a documented Open Source contribution policy;
- 5.1.2 a documented procedure that governs Open Source contributions; and
- 5.1.3 a documented procedure that makes all Software Staff aware of the existence of the Open Source contribution policy (e.g., via training, internal wiki, or other practical communication method).
글로벌 소프트웨어 기업들은 오픈소스를 사용하여 제품을 만들고 서비스를 하는 것 뿐만 아니라 오픈소스 프로젝트에 기여하며 얻을 수 있는 전략적 가치도 중요하게 여긴다. 그러나 오픈소스 프로젝트 생태계와 커뮤니티 운영방식에 대한 충분한 이해와 전략 없이 접근한다면 예기치 않게 회사의 명성이 손상되고 법적 위험이 발생할 수 있다. 따라서 기업은 오픈소스 프로젝트로의 참여 및 기여를 위한 전략과 정책을 만드는 것이 중요하다.
[부록 01] 오픈소스 정책 for OpenChain 2.0(예시)의 8장 오픈소스 기여 정책을 참고할 수 있다.
2.2.6 - 6. 설명서 요건 준수
6.1 준수 (Conformance)
OpenChain Specification 2.0
6.1 준수
프로그램이 OpenChain을 준수한다고 간주되려면 조직은 프로그램이 이 설명서에 제시된 요건을 충족하는지 확인해야 한다.
입증 자료:
6.1.1 요건 1.4에 명시된 프로그램을 확인하는 문서는 이 설명서의 모든 요건을 충족한다.
6.1 Conformance
In order for a Program to be deemed OpenChain Conformant, the organization must affirm that the program satisfies the requirements presented in this specification.
Verification Materials(s):
6.1.1 A document affirming the Program specified in requirement 1.4 satisfies all the requirements of this specification.
기업이 OpenChain을 준수하는 오픈소스 프로그램을 가지고 있다고 선언한다는 것은 OpenChain Specification의 모든 요건을 충족한다는 것이다. 어느 하나의 요건이라도 충족하지 못한다면 OpenChain을 준수한다고 할 수 없다.
OpenChain Specification의 모든 요건을 충족한다면, [부록 01] 오픈소스 정책 for OpenChain 2.0(예시)의 9장에서와 같이 OpenChain을 충족하고 있음을 문서상에 명시할 수 있다.
6.2 기간 (Duration)
OpenChain Specification 2.0
6.2 기간
이 설명서 버전에 대한 OpenChain 준수 프로그램은 준수한다고 확인이 이루어진 날로부터 18개월동안 지속된다. 준수 확인 등록 절차는 OpenChain 프로젝트의 웹사이트에서 확인할 수 있다.
입증 자료:
6.2.1 준수한다는 확인이 이루어진 후 18개월 이내에 이 설명서 버전(2.0)의 모든 요건을 충족하는 것을 확인하는 문서.
6.2 Duration
A Program that is OpenChain Conformant with this version of the specification will last 18 months from the date conformance validation was obtained. The conformance validation registration procedure can be found on the OpenChain project’s website.
Verification Materials(s):
6.2.1 A document affirming the Program meets all the requirements of this version of the specification (version 2.0), within the past 18 months of obtaining conformance validation.
오픈소스 프로그램이 OpenChain을 준수한다고 선언한 이후에도 계속해서 준수하는 활동을 유지하는 것이 중요하다. OpenChain Specification 2.0의 6.2.1조에서는 OpenChain을 준수한다고 선언한 이후에도 최소 18개월 이상은 변함없이 OpenChain Specification 2.0의 모든 요건을 준수하고 있어야 함을 요구한다.
기업은 오픈소스 프로그램이 OpenChain을 준수함을 선언한 이후 적어도 18개월 이상 계속해서 준수하는 상태를 유지하여야 하며, 그렇게 하고 있다면, [부록 01] 오픈소스 정책 for OpenChain 2.0 (예시)의 9장에서와 같이 OpenChain을 18개월 이상 계속하여 충족하고 있음을 문서상에 명시할 수 있다.
2.3 - 부록
2.3.1 - 1. 샘플 오픈소스 정책 for OpenChain 2.1
Note:
이 오픈소스 정책 for OpenChain 2.0(예)은 다음 두가지 자료를 참고하여 작성하였다.
- OpenChain Open Source Policy Template : https://github.com/OpenChain-Project/Reference-Material/blob/master/Policy-Templates/Official/en/2.0/Open-Source-Policy-Template-2.0-en.xlsx
- Linux Foundation Generic FOSS Policy : https://github.com/todogroup/policies/blob/master/linuxfoundation/lf_compliance_generic_policy.pdf
OO회사 오픈소스 정책
1. 목적
이 정책은 오픈소스를 사용하는 조직 전체가 오픈소스 컴플라이언스 활동을 수행하도록 수립되었다. 또한 이 정책은 직원들이 오픈소스의 가치를 이해하게 하고, 오픈소스 커뮤니티에 기여하기 위한 방법을 제공한다.
<OO회사>의 직원은 이 정책의 근거와 내용을 이해하고 필요한 활동을 충실히 수행함으로써 정책의 효과 및 회사의 컴플라이언스 수준 향상에 기여한다.
이 정책을 준수하는 것은 중요하다. 준수하지 않을 경우 다음과 같은 상황을 초래할 수 있다.
- 사용 중인 코드에 대한 저작권 또는 기타 지식재산권 보유자의 법적 클레임
- 고객으로부터의 클레임
- 회사 독점 코드의 의도치 않은 공개
- 라이선스 의무 위반으로 인한 벌금 부과
- 평판 손실
- 수익 손실
- 공급업체 및 고객과의 계약 위반
이러한 이유로 회사는 코드 침해를 심각하게 간주하며, 코드를 침해하는 개인은 회사의 징계 절차에 처해질 수 있다.
2. 적용
이 오픈소스 정책은 [회사가 외부로 제공하거나 배포하는 모든 제품]에 적용된다. 오픈소스를 내부 사용 목적으로만 사용하는 것은 이 정책의 범위에 포함되지 않는다.
또한 이 정책은 <OO회사>의 직원이 오픈소스 프로젝트에 기여하거나 <OO회사>의 코드를 오픈소스로 공개할때 적용한다.
<OO회사>의 오픈소스 정책은 [LINK]에서 확인할 수 있다.
3. 용어
“오픈소스” - Open Source Initiative(OpenSource.org)에서 발표한 Open Source Definition 혹은 Free Software Foundation에서 발표한 Free Software Definition을 충족하는 라이선스, 혹은 유사한 라이선스가 하나 이상 적용된 소프트웨어.
“공급 대상 소프트웨어” - 회사가 제3자 (다른 조직 또는 개인)에게 배포하는 소프트웨어
4. 역할, 책임 및 역량
이 정책의 효과적인 수행을 보장하기 위해 다음과 같이 필요한 역할 및 책임과 각 역할의 담당자가 갖추어야 할 역량을 정의한다.
<OO회사>의 소프트웨어 개발 및 배포를 담당하는 최고 임원은 각 역할 및 책임을 위한 담당자가 지정되고, 역할을 수행할 적절한 자금과 시간이 할당되도록 보장해야 한다.
각 역할의 담당자는 자신의 역할에 대해 적절하게 지원이 되지 않는다면 반드시 오픈소스 책임자를 통해 문제를 해결해야 한다. 적절하게 해결되지 않는다면, 오픈소스 운영위원회를 통해 문제를 제기할 수 있다.
가) 오픈소스 책임자
오픈소스 책임자는 오픈소스가 사용된 <OO회사> 제품의 컴플라이언스를 보장할 책임과 함께 다음 사항에 대한 책임이 있다.
- 오픈소스 정책을 검토, 개선 및 전파한다.
- 효율적인 오픈소스 정책 수행을 위해 회사 내부의 역할 및 책임을 검토하고 할당한다.
- 오픈소스 컴플라이언스 관련 이슈에 대한 교육과 평가를 검토하고 구현한다.
- 오픈소스 운영위원회의 의장을 맡아서 활동을 지휘한다.
- 소프트웨어 개발팀이 오픈소스 정책과 프로세스를 이해하고 준수하도록 안내하는 역할을 하고, 필요할 경우 경영진에게 문제를 제기한다.
- 외부로부터의 오픈소스 사용 및 컴플라이언스에 대한 문의에 답변한다.
오픈소스 책임자는 업무 수행을 위해 오픈소스 관련 IP 리스크, 개발 프로세스를 이해하고, 커뮤니케이션 스킬에 대한 역량을 갖춰야 한다.
2020년 1월 현재 OOO팀의 OOO가 오픈소스 책임자 역할을 담당한다.
나) 오픈소스 센터
오픈소스 센터는 오픈소스 컴플라이언스를 위한 전문 센터이며, 컴플라이언스를 효과적으로달성하기위한프로세스를정의한다. 오픈소스책임자가리더역할을수행 하고, 센터의 구성원들은 오픈소스 책임자가 원활하게 책임을 수행할 수 있도록 돕는 역할을 맡는다. 오픈소스 센터는 다음과 같은 역할을 수행한다.
- 컴플라이언스 실무 교육을 개발 및 제공한다.
- 컴플라이언스 도구를 선택 / 개발 및 배포한다.
- 코드 검사 및 자동 스캔을 수행하여 <OO회사> 제품 내 오픈소스 포함 여부를 식별한다.
- 오픈소스 사용 요청을 검토하고 승인한다.
- 오픈소스 사용 목록에 관한 기록을 유지한다.
- 오픈소스 고지 및 소스코드 공개를 위한 웹 사이트를 개발하고 유지 관리한다.
다) 소프트웨어 개발팀
소프트웨어 개발팀은 소프트웨어 개발에 사용할 오픈소스를 식별하고 오픈소스 센터에 오픈소스 사용 승인 요청을 제출한다.
소프트웨어 개발팀은 소프트웨어 개발에 사용한 오픈소스에 적용되는 오픈소스 라이선스의 의무를 이행할 책임이 있다.
소프트웨어 개발팀은 오픈소스 정책 및 프로세스와 소프트웨어 아키텍쳐를 이해한다.
라) 법무팀
법무팀은 오픈소스 라이선스와 의무를 해석한다. 이러한 의무를 이행하기 위한 가이드를 소프트웨어 개발팀에 제공한다. 호환되지 않는 오픈소스 라이선스로 인한 충돌을 포함하여 라이선스 및 지식재산권 문제에 대해 자문을 제공한다. 필요할 경우 오픈소스 사용 검토 및 승인 결정에 참여한다.
오픈소스 프로젝트로의 기여를 위한 검토 요청에 의견을 제공한다.
5. 교육 및 평가
소프트웨어 배포에 관여하는 <OO회사>의 모든 직원은 교육 및 평가를 통해 오픈소스 정책을 숙지한다.
이 정책을 수행하는 모든 대상자는 자신의 역할에 필요한 역량을 다루는 최소한의 기본 교육을 수강하고 평가를 받는다.
교육 및 평가 프로그램은 <OO회사> 오픈소스정책의 목표, 컴플라이언스 수준 향상에 기여 하기 위한 참여자의 역할 및 컴플라이언스 미준수 시 회사 및 개인에 미치는 영향 등에 대해 다룬다.
평가 기록은 최소 3년동안 유지한다.
6. 오픈소스 사용 정책
오픈소스를 사용하기 위해서는 먼저 오픈소스 라이선스가 무엇인지 식별하고, 라이선스가 요구하는 의무 사항을 검토하고 확인한다. 그렇게 공급 대상 소프트웨어에 포함된 오픈소스와 라이선스 의무사항을 식별하고, 소프트웨어를 배포 시 라이선스 의무사항을 준수하기 위한 활동을 한다.
이를 효과적으로 수행하기 위해 <OO회사> 오픈소스 컴플라이언스 프로세스를 준수한다.
오픈소스 라이선스 준수를 위한 과정에서 의문사항이 있는 경우 [오픈소스 책임자]는 법무팀에게 문의 할 수 있다.
오픈소스 사용 결정 결과 및 관련 근거는 오픈소스 이슈 추적 시스템에 기록한다.
7. 외부 문의 대응 정책
<OO회사>에서 배포한 소프트웨어에 대해 외부에서 오픈소스 관련한 문의 및 요청을 할 수 있도록 공개된 연락처를 제공한다. 이를 위해 소프트웨어 배포 시 오픈소스 센터의 이메일 주소를 제공하고,
Linux Foundation의 Open Compliance Directory (https://compliance. linuxfoundation.org/ references/open-compliance-directory/)에 <OO회사>의 연락처를 등록한다.
외부로부터 오픈소스 관련 문의를 받은 사람은 누구나 오픈소스 책임자에게 문의한다. 오픈소스 책임자는 문의를 처리하고 회사 내 적절한 개인 또는 조직에 할당한다. 오픈소스 책임자는 문의를 할당하고 처리하는 것에 대한 전반적인 책임이 있다.
<OO회사>에서 배포한 소프트웨어에 대해 외부로부터 컴플라이언스 미준수 이슈가 제기될 경우, 오픈소스 책임자는 다음과 같이 처리한다.
- 질의 접수 승인 및 적절한 해결 시간을 명시한다.
- 질의가 진짜 문제인 것인지를 확인한다. (아니라면 영업일 기준 3일 이내에 질의자에게 응답한다.)
- 이슈가 진짜 문제라면, 3일 이내에 적절한 대응 방법을 결정하고, 질의자에게 대응 계획에 대해 응답한다.
- 결정한 방법에 따라 30일 이내에 대응하고, 질의자에게 문제가 해결되었음을 알린다.
- 이상의 사항을 오픈소스 이슈 추적시스템에 기록한다.
8. 오픈소스 기여 정책
<OO회사>는 오픈소스에서의 비즈니스 가치 창출을 위해 외부 오픈소스 프로젝로의 참여와 기여를 권장한다. 그러나 의도하지 않은 지식 재산의 노출 혹은 침해를 주의해야 한다.
회사의 업무와 관련이 있는 오픈소스 프로젝트에 기여하기 위해서는 먼저 SW개발팀 리더에게 승인을 받아야 한다.
그리고 오픈소스 프로젝트의 오픈소스 라이선스와 특허 조건을 검토한다. 또한 기여 하고자 하는 오픈소스 프로젝트가 요구하는 DCO (Developer Certificate of Origin), CLA (Contributor License Agreement)등의 문서 서명에 대해 검토해야 한다. 필요할 경우 법무팀에 검토를 요청할 수 있다.
9. OpenChain 준수
<OO회사>는 소프트웨어 공급망에서의 오픈소스 컴플라이언스 수준 향상을 위해 Linux Foundation의 OpenChain 프로젝트의 정신을 지지하며 적극적으로 참여한다. <OO회사>의 오픈소스 정책은 OpenChain Specification 2.0을 준수하도록 설계되었다.
<OO회사>는 <OO회사>의 오픈소스 정책을 포함하는 오픈소스 프로그램이 OpenChain Specification 2.0의 모든 요건을 준수하고 있음을 확약한다.
<OO회사>는 <OO회사>의 오픈소스 정책을 포함하는 오픈소스 프로그램이 OpenChain Specification 2.0의 모든 요건을 준수하고 있음을 확약한 이후 18개월 동안 여전히 모든 요건을 준수하기 위한 활동을 수행하고 있음을 확약한다.
2.3.2 - 2. 오픈소스 컴플라이언스 프로세스 (template)
오픈소스 컴플라이언스의 주요 두가지 목적은 다음과 같다.
- 의무 파악 : 공급 대상 소프트웨어가 포함하고 있는 오픈소스를 식별하고 각 오픈소스 라이선스가 요구하는 의무를 파악한다.
- 의무 사항 이행 : 식별한 의무 사항을 이행한다.
이를 위해 기업은 공급 대상 소프트웨어를 배포하는 시점에 오픈소스 라이선스 의무사항을 준수할 수 있도록 오픈소스 컴플라이언스 프로세스를 구축해야 한다. 여기서는 일반적인 오픈소스 컴플라이언스 프로세스의 구성요소와 각각의 기능 및 역할을 포함하는 프로세스(예시)를 제안한다.
Note:
이 오픈소스 컴플라이언스 프로세스 (예시)는 다음 자료를 참고하여 작성하였다.
- Open Source Compliance In The Enterprise / Ibrahim Haddad : https://www.linuxfoundation.org/compliance-and-security/2018/12/open-source-compliance-in-the-enterprise/
<OO 회사> 오픈소스 컴플라이언스 프로세스 (예시)
<OO 회사>의 오픈소스 정책에 근거하여 오픈소스를 사용하기 위해서는 먼저 오픈소스 라이선스가 무엇인지 식별하고, 라이선스가 요구하는 의무 사항을 검토하고 확인해야 한다. 그렇게 공급 대상 소프트웨어에 포함된 오픈소스와 라이선스 의무사항을 식별하고, 소프트웨어를 배포 시 라이선스 의무사항을 준수하기 위한 오픈소스 컴플라이언스 활동을 해야 한다.
<OO회사>의 오픈소스 컴플라이언스 프로세서는 공급 대상 소프트웨어에 사용되는 오픈소스를 관리하는 일련의 과정을 정의한다. 이 과정에는 다음 사항이 포함된다.
- 공급 대상 소프트웨어에 사용된 모든 오픈소스 식별
- 식별한 오픈소스에 의해 발생하는 모든 의무를 식별하고 추적
- 모든 의무를 충족하기 위한 활동
이를 효과적으로 수행하기 위해 <OO회사>의 모드 소프트웨어 공급관리자는 다음 10단계를 수행한다.
Step 1. 오픈소스 식별 (Identification of Open Source)

오픈소스 식별 단계는 오픈소스 컴포넌트를 식별하기 위한 검토 단계이다. 자체 독점 소프트웨어인지, 제3자 소프트웨어인지 여부에 관계 없이 공급 대상 소프트웨어에 포함된 오픈소스를 모니터링한다. 오픈소스 식별 방법은 다음과 같다.
- 오픈소스 사용 요청 접수 : SW개발자는 특정 제품에 오픈소스를 사용하고자 함을 오픈소스 책임자 또는 오픈소스 센터에 알리고, 검토 및 승인을 위한 오픈소스 패키지의 용도에 관한 정보를 제공한다.
- 회사 개발 소프트웨어 검사 (Auditing) : 개발자가 오픈소스의 소스코드를 복사해서 가져와 소프트웨어를 개발할 수 있기 때문에 회사가 개발한 소프트웨어에 대해서도 검사를 수행한다.
- 제3자 소프트웨어 실사 (Due diligence)
| 식별 단계 시작 조건 | 식별 단계 결과 | ||
|---|---|---|---|
| • 개발자로부터 특정 오픈소스 사용 요청 접수 • 개발 프로세스 상 소프트웨어 검사 단계 • 제3자 소프트웨어 입수 및 개발소프트웨어로의 통합 | • 오픈소스에 대한 컴플라이언스 기록 생성 (Jira 등 활용) • 소스코드 스캔 대상 선정 및 요청 |
Step 2. 소스 코드 검사 (Auditing Source Code)

소스 코드 검사 단계에서는 소스 코드 분석 도구를 사용하여 소스 코드를 스캔하여 오픈소스를 발견한다. 소스 코드 스캔도구는 FOSSology를 이용한다. GPL-3.0 등 정책적으로 사용할 수 없는 오픈소스 라이선스가 적용된 오픈소스 혹은 라이선스 충돌로 양립할 수 없는 오픈소스가 발견될 경우 문제로 식별하여 개발팀에 보완을 요청한다.
| 식별 단계 시작 조건 | 식별 단계 결과 | ||
|---|---|---|---|
| • 개발자로부터 특정 오픈소스 사용 요청 접수 • 개발 프로세스 상 소프트웨어 검사 단계 • 제3자 소프트웨어 입수 및 개발소프트웨어로의 통합 | • 오픈소스에 대한 컴플라이언스 기록 생성 (Jira 등 활용) • 소스코드 스캔 대상 선정 및 요청 |
Step 3. 문제 해결 (Resolving Issues)

소스 코드 검사 단계에서 식별된 모든 문제를 해결한다. 문제 사항은 Jira Ticket으로 생성하여 개발팀에 할당되고, 오픈소스 책임자는 모든 문제가 적절하게 해결되었는지 확인한다.
| 문제 해결 단계 시작 조건 | 문제 해결 단계 결 |
|---|---|
| • 소스 코드 스캔 완료 및 결과 생성 • 문제 식별 | • 식별된 문제를 모두 해결 |
Step 4. 검토 (Reviews)

식별된 모든 문제가 해결되면 검토 단계로 이동한다. 검토 단계의 절차는 다음과 같다.
- 소프트웨어 PL : 소프트웨어에 포함된 오픈소스에 대한 사용 승인 요청서를 제출한다.
- 오픈소스 책임자 : 사용 승인 요청서를 접수하면 모든 정보가 누락없이 포함 되었는지를 확인하고, Jira ticket을 생성하여 검토 절차를 진행한다.
- 소스코드 검사 담당자: Jira ticket이 생성되면 소스코드 검사를 수행하여 문제가 모두 해결되었는지 확인한다.
- 법무팀 : 라이선스 이슈를 검토한다.
| 검토 단계 시작 조건 | 검토 단계 결과 |
|---|---|
| • 식별된 모든 문제 해결 | • 오픈소스 책임자, 소스코드 검사 담당자, 법무팀 등의 검토를 완료하여 승인 준비가 된 상태 |
Step 5. 승인 (Approval)

검토가 완료되면 Jira ticket은 승인 단계로 이동한다. OSRB는 오픈소스의 사용을 승인하거나 거절한다. 거절시에는 이유에 대한 설명과 수정 방법을 제안한다. OSRB가 오픈소스 구성요소의 사용을 승인하면 개발팀은 라이선스 의무를 이행하기 위한 준비를 시작한다.
| 승인 단계 시작 조건 | 승인 단계 결과 |
|---|---|
| • 검토가 완료된 상태 | • OSRB는 오픈소스의 사용을 승인하거나 거절함 • 거절 시에는 이유에 대한 설명과 수정 방법 제안 |
Step 6. 등록 (Registration)

사용이 승인된 오픈소스 구성요소는 오픈소스 사용을 추적하는 BOM (소프트웨어 인벤토리)에 추가한다. BOM에는 오픈소스 구성요소 이름, 버전, 관리 담당자 이름, 이를 사용하는 제품 이름, 제품 버전, 제품 릴리즈 번호 등의 정보를 포함한다. BOM을 관리하는 도구는 SW360을 사용한다.
| 등록 단계 시작 조건 | 등록 단계 결과 |
|---|---|
| • OSRB가 오픈소스 사용을 승인 | • 오픈소스 구성요소를 BOM에 등록 |
Step 7. 고지 (Notices)

오픈소스를 사용할 때 주요 의무 중 하나는 고지 의무이다. 이를 위해 다음 사항을 수행 한다.
- 저작권, 라이선스 고지를 제공한다.
- 라이선스 사본을 제공한다.
- (해당되는 경우) 소스 코드 사본을 얻을 수 있는 방법을 최종 사용자에게 알린다.
| 고지 단계 시작 조건 | 고지 단계 결과 |
|---|---|
| 오픈소스를 BOM에 등록 | 저작권, 라이선스 고지를 준비하고, 이를 제품에 포함되도록 관련 부서로 전달 |
이와 같은 사항을 제품 배포 시 포함시킬 수 있도록 관련 부서에 전달한다. 화면이 있는 제품이면 사용자가 메뉴 > 오픈소스 고지 정보에서 오픈 소스 고지 내용을 확인할 수 있게 한다. 제품에 화면이 없을 경우, 사용자 매뉴얼에 오픈소스 고지 내용을 포함시킨다.
Step 8. 배포 전 확인 (Pre-Distribution Verifications)

이 단계에서는 다음 사항을 보장하기 위한 확인을 수행한다.
- 오픈소스 라이선스가 요구하는 공개할 소스 코드를 취합한다.
- 취합한 소스 코드는 제품에 탑재된 바이너리와 매치되어야 한다.
- 소스 코드 내 부적절한 주석을 제거한다.
- 적절한 고지문이 제품에 포함되었다. 여기에는 최종 사용자가 소스 코드를 받을 수 있는 방법 (Written Offer)도 함께 제공한다.
| 배포 전 확인 단계 시작 조건 | 배포 전 확인 단계 결과 |
|---|---|
| • 모든 오픈소스 구성요소가 BOM에 등록 | • 고지 의무를 이행할 수 있도록 조치 • 공개할 소스 코드 취합 • 소스 코드 제공 방법 결정 • 배포 전 확인 수행 완료 |
Step 9. 배포 (Distribution)

배포 전 확인이 완료되면 공개할 소스 코드 패키지를 오픈소스 배포사이트에 업로드한다. 오픈소스 배포사이트에는 제품 및 버전별로 등록할 수 있다. 최종 사용자는 자신이 원하는 제품의 버전에 해당하는 소스 코드 패키지를 오픈소스 배포사이트에서 검색하여 다운로드 받을 수 있다.
| 배포 단계 시작 조건 | 배포 단계 결과 |
|---|---|
| • 모든 배포 전 확인 완료 | • 특정 제품의 버전에 대한 공개할 소스 코드 패키지를 오픈소스 배포사이트에 업로드 |
Step 10. 최종 확인 (Final Verifications)

공개할 소스 코드 패키지를 오픈소스 배포사이트에 업로드 후 패키지가 올바르게 업로드 되었고, 외부에서 오류 없이 다운로드 및 압축 해제가 되는지 확인한다. 라이선스에 따라 빌드하여 바이너리 생성까지 보장을 요구하는 경우, 외부에서 다운받은 소스 코드가 README의 안내대로 오류 없이 빌드하여 바이너리가 생성되는지, 생성된 바이너리가 제품에 탑재된 바이너리와 동일한지 확인한다.
| 최종 확인 단계 시작 조건 | 최종 확인 단계 결과 |
|---|---|
| • 공개할 소스 코드가 오픈소스 배포사이트에 게시 | • 외부에서 다운로드가 이상없이 수행되는지, 제품과 동일한 버전의 바이너리와 매치가 되는지 확인 |
2.3.3 - 3. 오픈소스도구 (FOSSology, SW360)
오픈소스 컴플라이언스 활동을 위해서는 정책, 프로세스나 교육자료뿐만 아니라 소스코드 스캔, Dependency 분석, 오픈소스 BOM 관리 등을 위한 다양한 도구와 시스템도 요구된다. 때문에 다수의 기업이 이러한 도구와 시스템을 도입하고 활용하는데 많은 리소스를 투입하고 있다. 특히 오픈소스 컴플라이언스를 처음 시작하는 기업은 프로세스뿐 아니라 비용 측면에서도 어려움을 겪고 있다.
이런 어려움을 해결하기 위해, 2019년 6월, OpenChain 프로젝트에 참여하고 있는 지멘스, 보쉬, 도시바, 후지쓰, 히타치 등의 오픈소스 컴플라이언스 도구 전문가들을 주축으로 OpenChain Tooling Work Group이 시작되었다.
OpenChain Tooling Work Group은 여러 기업의 오픈소스 전문가들이 이슈를 함께 해결하고 결과물을 공유해 오픈소스 컴플라이언스 비용을 절감하고 양질의 컴플라이언스 결과물을 만들어 내기 위해 구성되었다.
구체적으로는 FOSSology, SW360, Software Heritage, ClearlyDefined, SPDX 등의 기존 오픈소스 프로젝트를 활용하여 통합(turn-key) 오픈소스 툴 체인을 만들고, 모든 기업이 이를 자유롭게 사용할 수 있도록 하는 것을 목표로 삼고 있다. (https://groups.io/g/oss-based-compliance-tooling)
여기서는 FOSSology와 SW360에 대해 소개 및 간단한 사용 방법에 대해 알아본다.
2.3.3.1 - FOSSology
오픈소스 컴플라이언스를 위해 소프트웨어 내에 포함된 오픈소스와 라이선스 정보를 검출하기 위해 소스코드 스캔 도구를 사용할 수 있다.

Linux Foundation의 FOSSology 프로젝트는 이러한 스캔 도구를 개발하고 오픈소스로 공개해 누구나 자유롭게 사용할 수 있게 한 도구이다.
주요 특징
FOSSology는 웹기반의 프로그램으로 사용자는 웹사이트에 로그인하여 개별 파일 혹은 소프트웨어 패키지를 업로드할 수 있다. FOSSology는 업로드된 파일 내에 라이선스 텍스트와 Copyright 정보를 검출한다. 개발자는 사용하고자 하는 오픈소스의 라이선스가 무엇인지, Copyright은 어떻게 되는지에 대한 정보를 확인하고자 할때 FOSSology를 이용하는 것이 좋다. FOSSology는 개발자가 업로드한 오픈소스 패키지 내의 모든 파일을 스캔하여 각 파일 내 라이선스 관련 텍스트와 Copyright 정보를 자동으로 검출하고, 이를 리포트로 생성한다. FOSSology 주요 특징에 대한 자세한 내용은 다음 페이지를 참고할 수 있다. : https://www.fossology.org/features/
설치
기업 내에서 FOSSology를 사용하기 위해서는 사내에 FOSSology 서버를 구축해야 한다. 이를 위해 리눅스 기반의 서버 시스템에 FOSSology를 설치해야 한다. FOSSology는 다음 세 가지 방법으로 설치할 수 있다.
- Docker 사용
- Vagrant와 VirtualBox 사용
- Source build하여 설치
여기서는 가장 간편한 방법인 Docker를 사용하는 방법에 대해 설명한다.
FOSSology는 컨테이너화 된 Docker 이미지를 Docker Hub (https://hub.docker.com/)를 통해 공개하고 있다. : https://hub.docker.com/r/fossology/fossology
Pre-built 된 Docker 이미지는 다음 명령어를 사용하여 실행할 수 있다.
$ docker run -p 8081:80 fossology/fossology
Docker 이미지는 다음 URL과 계정 정보로 사용할 수 있다. : http://[IP_OF_DOCKER_HOST]:8081/repo
- Username : fossy
- Passwd : fossy
설치와 관련한 자세한 내용은 다음 페이지를 참고할 수 있다. : https://github.com/fossology/fossology/blob/master/README.md
테스트 서버
FOSSology를 설치할 수 있는 시스템 구축이 곤란한 상황이라면, FOSSology Project에서 제공하는 테스트 서버를 이용할 수 있다. FOSSology 프로젝트에서는 테스트를 위한 환경을 제공한다. (테스트 서버는 예고없이 중단될 수 있다.)
사용자는 다음 계정으로 FOSSology 테스트 서버에 접속하여 FOSSology 기능을 시험해볼 수 있다.
테스트 서버 URL: https://fossology.osuosl.org/
- Username: fossy
- Password: fossy

Basic Workflow
FOSSology의 기본 사용 절차는 다음과 같다.
- 사용하고자 하는 오픈소스의 라이선스와 Copyright 정보를 확인하기 위해 오픈소스의 소스 코드를 하나의 파일로 압축하여 FOSSology에 업로드한다.
- 이를 위해 메뉴 > Upload > From File을 선택합니다.
- 업로드할 파일을 선택하고 Upload 버튼을 클릭한다.
- 업로드가 완료되면 Job Agent에 의해 자동으로 분석을 수행한다.
- 메뉴 > Jobs > My Recent Jobs에서 분석 중인 Status를 확인할 수 있다.
- 분석이 완료되면 메뉴 > Browse에서 분석 결과를 확인할 수 있다.
- 개별 파일을 선택하면 FOSSology가 검출한 라이선스 관련 텍스트가 무엇인지 확인할 수 있다.
- 메뉴 > Browser > 파일 혹은 디렉터리를 선택 > Copyright/Email/Url/Author에서는 FOSSology가 검출한 Copyright/Email/Url/Author 정보를 보여다.
사용자는 FOSSology는 이렇게 분석한 결과가 유효한지 여부에 대해 확인 후 잘못 검출된 항목에 대해서는 분석 결과에서 제외시키는 작업을 할 수 있다. FOSSology는 이를 Clearing 과정이라고 설명하며, 자세한 사항은 다음 페이지를 참고할 수 있다. : https://www.fossology.org/get-started/basic-workflow/
위와 같은 방법으로 사용하고자 하는 오픈소스의 라이선스는 무엇인지, Copyright 정보는 어떻게 되는지를 간단히 확인할 수 있다.
2.3.3.2 - SW360
오픈소스를 포함하는 제품을 개발하고 배포하는 기업이라면 각 제품과 릴리스 버전마다 사용한 오픈소스의 버전, 라이선스 등의 정보를 수집하고 추적해야 한다. 이를 통해 기업은 올바른 오픈소스 컴플라이언스 활동을 수행할 수 있다.
특히, NVD (https://nvd.nist.gov/vuln)에서 특정 오픈소스 버전에 보안 취약점이 보고 되었을때, 해당 버전을 사용하고 있는 제품이 무엇인지 추적을 할 수 없다면, 그 기업은 어느 제품에 보안 패치를 적용해야 할 지 알 수 없는 상황에 처하게 되고, 그 기업의 제품들은 보안취약점에 그대로 노출이 될 수 밖에 없다.
이렇듯, 오픈소스 정보를 추적하는 활동은 꼭 필요하다. 기업들은 이를 위해 자체 시스템을 구축하거나, 상용 서비스를 구매하여 사용하기도 한다. SW360은 Eclipse 재단에서 후원하는 오픈소스로서 소프트웨어 BOM에 대한 정보를 수집 및 추적하기 위한 웹 애플리케이션 및 저장소를 제공한다.

주요 특징
SW360은 웹 기반의 UI를 제공하며 주요 기능은 다음과 같다.
- 제품에 사용된 컴포넌트 추적
- 보안 취약점 평가
- 라이선스 의무 관리
- 고지문 등 법적 문서 생성
설치
SW360은 다음과 같이 구성된다.
- Frontend : Liferay-(Tomcat-)based portal application
- Backend : Tomcat-based thrift service
- Database : CouchDB
Project 구조와 설치를 위해 요구되는 소프트웨어 등 자세한 내용은 README의 Required software 부분에서 확인할 수 있다. : https://github.com/eclipse/sw360/blob/master/README.md
SW360은 다음 세 가지의 설치 방법을 제공한다. 사용자는 이 중 하나를 선택하여 설치할 수 있다.
- Vagrant (https://www.vagrantup.com/) 기반 설치 : Vagrant는 가상화 인스턴스를 관리하는 도구로서 sw360vagrant에서는 SW360을 한 번에 Deploy 하기 위한 환경을 제공한다. : https://github.com/sw360/sw360vagrant
- SW360의 구성요소를 개별적으로 설치할 수 있다. : https://github.com/eclipse/sw360
- Docker를 통해 Deploy 할 수 있다. : https://github.com/sw360/sw360chores
여기서는 CentOS 7.6 시스템에 Vagrant 기반으로 설치하여 Deploy하는 방법을 소개한다. 자세한 사항은 README를 참고한다. : https://github.com/sw360/sw360vagrant/blob/master/README.md
1) 사전 설치
vagrant box에 SW360을 설치하기 위해서는 openjdk, VirtualBox 및 Vagrant를 설치해야 다. 먼저 openjdk 1.8.0을 설치한다.
$ yum install java-1.8.0-openjdk
$ java -version
openjdk version "1.8.0_191"
OpenJDK Runtime Environment (build 1.8.0_191-b12)”
OpenJDK 64-Bit Server VM (build 25.191-b12, mixed mode)
VirtualBox를 설치한다.
$ sudo wget https://download.virtualbox.org/virtualbox/rpm/el/virtualbox.repo -P /etc/yum.repos.d
$ sudo yum install VirtualBox-5.2
CentOS 7에서 VirtualBox 설치 시, “kernel module is not loaded’ 에러가 발생할 경우, kernel-devel을 설치하여 해결한 후 VirtualBox를 재설치한다.
$ sudo yum install https://centos7.iuscommunity.org/ius-release.rpm
$ sudo yum install dkms
$ sudo yum install kernel-devel
# reboot
$ sudo /sbin/vboxconfig
$ systemctl status vboxdrv
● vboxdrv.service - VirtualBox Linux kernel module
Loaded: loaded (/usr/lib/virtualbox/vboxdrv.sh; enabled; vendor preset: disabled)
Active: active (exited) since Wed 2020-02-19 09:06:02 KST; 20min ago
Vagrant와 vagrant-aws plugin을 설치한다.
$ sudo yum install https://releases.hashicorp.com/vagrant/2.2.6/vagrant_2.2.6_x86_64.rpm
# vagrant-aws plugin 설치
$ vagrant plugin install vagrant-aws
그리고, sw360vagrant 코드를 Clone 한다.
$ git clone https://github.com/sw360/sw360vagrant.git
2) Dependency 다운로드
Vagrant box를 빌드하는 시간을 줄이기 위해 Dependency Package들을 미리 다운로드 받는다.
$ cd sw360vagrant
$ ./download-packages.sh
그러면 다음의 package들이 ./shared/package 폴더 안에 다운로드 된다.
- Liferay 7.2.1 CE GA2 with Tomcat (9.0.17)
- Postgresql-42.2.9 ODBC client for Java as *.jar file
- SW 360에서 필요한 11개의 *.jar 파일
- Thrift 0.11
- A box images from the Ubuntu 16.04 LTS (xenial-server-cloudimg-amd64-vagrant.box)
3) Base box 생성
이제 다음 명령어로 Base box를 생성한다.
$ cd generate-box
$ ./generate_box.sh
이 작업은 수십 분 소요될 수 있다.
4) Box 실행
다음 명령어로 Box를 실행한다.
# If you have built a vagrant box from this directory earlier, you will have to destroy it first via
$ vagrant destroy
$ cd ../sw360-single
$ vagrant up
Box를 실행하면 liferay, postgresql 및 couchdb가 구성된다. 이상없이 실행이 될 경우, https://localhost:8443/ 로 Liferay 화면에 접근할 수 있다.
5) SW360 Layout Deploy
마지막 단계는 Liferay에서 SW360의 Layout을 Deploy하는 것이다. 이 작업은 아직 자동화가 되지 않아 관리자가 수동으로 수행해야 다. https://localhost:8443/에 접근하여 다음 계정으로 로그인한다.
- id : setup@sw360.org
- pw : sw360fossy
이후에는 다음 사이트의 안내에 따라 Layout deploy를 수행한다. https://github.com/eclipse/sw360/wiki/Deploy-Liferay7
Deploy가 완료되면 다음과 같은 화면을 볼 수 있다.
Basic Workflow
1) License 등록
SW360을 처음 설치하면 먼저 자주 사용하는 오픈소스 라이선스 들을 등록해야 한다. 라이선스 다음과 같은 정보를 포함한다.
- Full Name
- Short Name
- License Type
- GPL-2.0 Compatibility (예: yes, no)
- License Text
메뉴 > Licenses > Add License를 선택하면 다음과 같이 Create License 화면으로 진입한다.
이와 같이 라이선스를 하나씩 수동으로 등록하는 일은 상당히 수고스러울 수 있는데, 다행히 SW360은 SPDX License List를 한 번에 Import 하는 기능을 제공한다. 메뉴 > Admin < Import SPDX Information을 클릭한다.
그러면, 곧 SPDX License List가 자동으로 등록됩니다. 메뉴 > Licenses에서 338개의 License가 등록된 것을 확인할 수 있다.
2) Component 및 Release 등록
SW360에서 Component는 하나의 소프트웨어 단위이다. 여기에는 다양한 형태의 소프트웨어가 해당할 수 있으며, 그 예는 다음과 같다.
- 오픈소스 소프트웨어
- 라이브러리
- 3rd party 소프트웨어
Component는 다음과 같은 정보를 포함한다.
- Component Name
- Main Licenses
- Categories (예: Library, Cloud, Mobile, …)
- Component Type (예: OSS, Internal, InnerSource, Service, Freeware)
- Default Vendor
- Homepage URL
Release는 Component에서 하나의 Version을 가리키는 단위이다. 따라서 하나의 Component는 여러 개의 Release를 가질 수 있다. Release는 하나의 Component 하위에 생성되어 관리된다.
Release는 다음과 같은 정보들을 포함한다.
- Component Name
- Version
- License
- Download URL
- CPE ID (예: cpe:2.3:a:apache:maven:3.0.4)
예를 들어, zlib-1.2.8을 등록해야 한다면, 먼저 Component에 zlib을 먼저 등록한 후, Release에 zlib 1.2.8을 등록한다. Menu > Components > Add Component를 선택하면 Create Component 화면으로 진입하여 zlib에 대한 정보를 등록할 수 있다.
Component를 생성하면, Components > Releases > Add Release에서 zlib-1.2.8 version에 대한 정보를 등록할 수 있다.
하나의 zlib이라는 Component에 1.2.8과 1.2.11 version을 각각의 Release로 등록하였을 때, Release Overview 화면에서 다음과 같이 2개의 Release가 존재하는 것을 볼 수 있다.
SW360은 다수의 Component 정보를 Import 시키기 위한 기능을 제공한다. 메뉴 > Admin > Import / Export에 CSV template에 등록을 원하는 Component 정보를 입력 후 Import 할 수 있다.
단, 이 기능은 2020년 2월 기준 아직 안정적으로 동작하지 않을 수 있다.
3) Project 생성
Project는 하나의 제품을 가리킨다. 사업 유형에 따라 제품일수도 있고, 서비스 혹은 소프트웨어 일수도 있다. Project에는 제품에 사용된 Component/Release를 등록하여 관리한다.
Project 생성 시에는 다음과 같은 정보를 등록한다.
- Project Name
- Version
- Project type (예: Product, Customer Project, Service, Internal Project, InnerSource)
메뉴 > Projects > Add Project를 통해 Project를 생성할 수 있다.
Project를 생성하고 나면, 포함하는 Release나 하위 Project를 등록한다. 메뉴 > Projects에서 해당 Project를 선택하면 “Linked Releases and Projects”에서 Linked Projects와 Linked Releases를 등록할 수 있다.
다음은 SuperCalc라는 Project에 OpenSSL 1.0.1과 zlib 1.2.8을 Linked Releases로 등록한 이후의 화면이다.
4. 보안 취약점 관리
SW360은 등록된 Release에 대해 보안 취약점이 있는지 자동으로 확인할 수 있다. 이를 위해 SW360은 CVE 정보를 주기적으로 수집하도록 스케쥴링하는 기능을 제공한다. 메뉴 > Admin > Schedule 에서 CVE SEARCH 정보를 24시간마다 수집하도록 스케쥴링을 설정할 수 있다.
이렇게 스케쥴링을 설정하면 SW360은 정해진 시간에 CVE Search 사이트(https://cve.circl.lu/)에서 CVE 정보를 수집한다. 수집한 CVE 정보는 메뉴 > Vulnerabilities에서 확인할 수 있다.
이렇게 Vulnerabilities 정보가 수집된 이후에는 생성한 Project에 보안 취약점이 있는지 조회할 수 있다. 위에서 생성한 SuperCalc Project에서는 85개의 보안 취약점이 보고된 것을 확인할 수 있다.
이와 같은 방법으로 기업에서 개발/배포하는 소프트웨어를 SW360에 등록하여 관리한다면, 오픈소스 컴플라이언스뿐만 아니라 보안 취약점에 대해서도 리스크를 최소화할 수 있는 형태로 관리가 가능하다.
또한 SW360은 위와 같은 Web Interface 뿐만 아니라 대부분의 기능을 REST API로 제공하여서 FOSSology 등의 다른 도구와의 연동이 가능하다. : https://github.com/eclipse/sw360/wiki/Dev-REST-API
즉, 소스 코드 스캐닝 도구의 분석 결과를 SW360에 Import 시키는 등의 방법으로 DevOps에 Integration 시켜서 Project, Release 등록을 자동화시켜서 관리한다면 효율성이 크게 증가될 것이다.
3 - A Handbook for Software Supply Chain Security in the Telco Industry
This handbook offers practical, step-by-step guidance for organizations in the telecommunications industry to implement the ‘OpenChain Telco SBOM Guide’.
It provides implementation plans and use-case scenarios tailored to each stakeholder, helping organizations establish effective SBOM management systems and strengthen their software supply chain security.
Author : OpenChain Korea Work Group / CC BY 4.0
Chapter 1: Why the Telco Industry Needs SBOMs Now
1.1. The New Threat Landscape in the Global Software Supply Chain
1.1.1. Growing Reliance on Open Source in 5G and Cloud-Native Environments
The telecommunications industry is undergoing a period of rapid digital transformation. The rollout of 5G networks, adoption of cloud-native technologies, and explosive growth of IoT devices have exponentially increased software complexity and interdependence.
Today, over 90% of software development relies on open source. In telecom infrastructure, open-source communication protocols like OPC UA and MQTT are vital for real-time data exchange. The complex architecture of 5G networks involves thousands of software components, with increasingly intricate dependency relationships.
1.1.2. The Log4j Incident: A Supply Chain Wake-Up Call
The Log4Shell (Log4j vulnerability) disclosed in December 2021 had a profound impact on the global software ecosystem, including the telecommunications industry. This vulnerability exposed several critical issues:
- Widespread Impact: Log4j is one of the most widely deployed open-source libraries globally, affecting millions of systems. According to IBM’s X-Force Threat Intelligence Index, vulnerabilities surged by 34% between 2020 and 2021, largely attributed to Log4Shell.
- Detection and Response Challenges: Many companies spent significant time simply identifying whether their systems used third-party products containing the Log4j library. Even two years after its disclosure, 38% of applications using Log4j remained vulnerable.
- Discovery of Subsequent Vulnerabilities: Following the initial vulnerability (CVE-2021-44228), seven additional vulnerabilities were discovered, highlighting the need for continuous monitoring and updates.
1.1.3. The Push for Transparency with SBOMs
The Log4j incident starkly demonstrated the dangers of lacking visibility into software components. In its wake, governments and industries worldwide began pushing for the adoption of a Software Bill of Materials (SBOM) to secure the software supply chain.
In May 2021, the Biden administration issued an Executive Order on Improving the Nation’s Cybersecurity, which mandated strengthening software supply chain security. Similarly, the South Korean government announced plans to reinforce software development and supply chain security in its K-Cyber Quarantine Promotion Strategy.
1.2. Unique Challenges of the Telco Industry
1.2.1. A Complex Ecosystem with a Multi-Layered Supply Chain
The telecommunications industry features a complex, multi-layered supply chain structure:
- Hardware Layer: Network equipment manufacturers supply firmware and embedded software for base stations, routers, and switches.
- Software Layer: Various network software suppliers provide solutions like SDN/NFV, network management, and security.
- Service Layer: Telecom operators deliver end-user services such as 5G, cloud, and IoT.
In this structure, a single vulnerability can create a massive cascading effect across the entire network.
1.2.2. Demanding Standards for Reliability and Security
Telecommunications infrastructure is designated as critical national infrastructure, requiring exceptionally high levels of security and reliability. 5G networks, in particular, introduce new security challenges:
- Massive IoT Connectivity: A 5G environment connects billions of IoT devices, each a potential attack vector.
- Distributed Edge Computing: As data processing shifts to the network edge, centralized security management becomes more difficult.
- Network Slicing Isolation: A security breach in one network slice could potentially impact others.
- The Rise of Open RAN (O-RAN): The promotion of open RAN interfaces, mainly driven by the O-RAN Alliance, allows equipment from multiple vendors to be used together, breaking away from traditional single-vendor lock-in. However, this introduces new supply chain risks. For equipment from different vendors to interoperate safely and securely, they must exchange mutually trusted information about their software composition. An SBOM is the foundational mechanism that provides this basis of trust.
1.2.3. Mounting Regulatory and Customer Pressure for SBOMs
The demand for SBOMs from regulators and customers is rapidly intensifying:
- Government and Public Sector: Public institutions, like the Korea Meteorological Administration, are beginning to require SBOM submission in procurement notices.
- Global Regulatory Trends:
- United States: Mandated the provision of SBOMs for all software delivered to the federal government.
- EU: Is advancing SBOM mandates through the Cyber Resilience Act (CRA).
- Other major countries like Japan and South Korea are pursuing similar policies.
- Customer Demands: Large telecom operators, equipment manufacturers, and network solution providers increasingly specify SBOM delivery as a contractual requirement.
- Industry Momentum: Industry-led initiatives like the OpenChain Project are building consensus and proposing practical, industry-specific SBOM guides for telecommunications to address these growing needs from the ground up.
- Future Standardization: It is anticipated that formal Standards Development Organizations (SDOs), such as ETSI, will address this topic more formally in the future, potentially building on the work done by industry groups in response to regulations like the EU’s Cyber Resilience Act (CRA).
These shifts signal a fundamental need to innovate software supply chain security in the telecommunications industry. An SBOM is no longer an option but a core requirement for survival and competitiveness in the telco sector.
Chapter 2: An Introduction to the OpenChain Telco SBOM Guide
- English (Original): OpenChain Telco SBOM Guide 1.1
- Korean (한국어): OpenChain Telco SBOM 가이드 1.1
2.1. Background and Core Objectives
2.1.1. Addressing SBOM Fragmentation in the Telco Industry
The telecommunications industry is one of the world’s most complex and interconnected software ecosystems. As 5G infrastructure, cloud-native solutions, and network virtualization converge, organizations have adopted disparate methods and requirements for creating SBOMs.
This fragmentation has created several significant challenges:
- Lack of Compatibility: An SBOM from a telecom operator might not match the format provided by an equipment manufacturer, leading to added conversion work and costs.
- Redundant Investment: As each organization developed its own tools and processes, the industry as a whole made inefficient, redundant investments.
- Limited Risk Management: Non-standardized SBOMs made it difficult to track vulnerabilities and respond quickly across the entire supply chain.
In response, the OpenChain Project formed the Telco Working Group in 2023 to develop a specialized SBOM guide for the telecommunications industry.
2.1.2. A New Standard for Interoperability, Repeatability, and Efficiency
The OpenChain Telco SBOM Guide introduces a practical approach that reflects the unique needs of the telecommunications industry while ensuring compatibility with global standards. The guide’s core objectives are:
- Repeatability: Provide clear criteria to ensure that an SBOM of consistent quality can be generated for the same software, regardless of who creates it or when.
- Streamlined Tooling: Enable various SBOM generation tools to produce standardized outputs that are compatible across organizations.
- Supply Chain Transparency: Allow all entities that produce and consume SBOMs to exchange software component information based on a common standard.
2.2. The Three Core Principles of the Guide
2.2.1. Principle 1: Standardization
The OpenChain Telco SBOM Guide adopts the SPDX (Software Package Data Exchange) format, which is certified as international standard ISO/IEC 5962:2021. This choice was driven by several strategic factors:
- International Standard Compliance: SPDX is the only SBOM format officially adopted by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC) as of September 2021.
- Technical Advantages: SPDX offers more robust features for license compliance than other formats and supports a human-readable structure.
- Industry Validation: Global companies like Ericsson, Intel, Microsoft, Siemens, Sony, and Nokia use SPDX for their software supply chain management, making it a proven standard.
The guide requires compliance with SPDX version 2.2 or 2.3 and specifies that SBOMs be provided in Tag:Value or JSON format.
2.2.2. Principle 2: Clarity
The OpenChain Telco SBOM Guide builds on the minimum requirements from the NTIA (National Telecommunications and Information Administration) but establishes clear, practical criteria tailored to the telecommunications industry’s needs:
Required SPDX Elements:
- Document Creation Information:
SPDXVersion,DataLicense,Creator,Created, etc. - Package Information:
PackageName,PackageVersion,PackageSupplier,PURL, etc. - Relationship Information: Dependency relationships like
DESCRIBES,CONTAINS, etc.
- Document Creation Information:
Delivery Timing and Method:
- Timing: The SBOM must be delivered concurrently with the software.
- Method: The primary method is to embed the SBOM within the software package. If technically infeasible, web hosting is permitted, with access guaranteed for at least 18 months.
- Note: The SBOM may be made available before delivery is the SBOM provider so wishes, however, it is still a requirement to also deliver it concurrently with the software.
Mandatory Generation Information:
- The
Creatorfield must include the organization’s name and the tool’s name/version. - The
CreatorCommentfield must include the CISA-defined SBOM Type (e.g., Design, Source, Build).
- The
2.2.3. Principle 3: Comprehensiveness
Modern software has numerous transitive dependencies, which are major vectors for security vulnerabilities. As the Log4j incident demonstrated, the spread of vulnerabilities through these dependencies is unpredictable and can cause extensive damage.
The OpenChain Telco SBOM Guide reflects this reality by requiring a comprehensive scope:
- All Open Source Included: All open-source software delivered with the product, including all transitive dependencies, must be listed.
- Commercial Components Recommended: The guide recommends including all commercial components. If excluded, they must be reported as “known unknowns.”
- Container Environment Support: The scope includes packages installed in a container, components copied or downloaded to it, and dependencies used to build compiled components within it.
2.3. Key Requirements at a Glance
The following table summarizes the key requirements of the OpenChain Telco SBOM Guide:
| Category | Requirement | Details |
|---|---|---|
| Data Format | SPDX 2.2/2.3 | Tag:Value or JSON format |
| Required Elements | NTIA Minimum Elements + Telco Additions | Document Creation, Package, and Relationship Info |
| Delivery Timing | Concurrent with software delivery | Delivered no later than the software itself |
| Delivery Method | Embedded in package (primary) | Web hosting if infeasible (18-month access guaranteed) |
| SBOM Scope | Open Source + Transitive Dependencies | Commercial components recommended; “known unknowns” if excluded |
| Generation Info | Organization, Tool Name/Version | Must include CISA SBOM Type |
| Verification | Digital Signature Recommended | Tools like Sigstore are encouraged |
Through this systematic and practical approach, the OpenChain Telco SBOM Guide provides a solid foundation for advancing software supply chain management in the telecommunications industry. Nokia’s adoption of this guide for its internal framework testifies to its practicality and effectiveness.
Chapter 3: The Business Value of Guide Compliance
Adhering to the OpenChain Telco SBOM Guide is not just a compliance task; it’s a strategic investment that delivers tangible business value. By standardizing SBOM practices, your organization can enhance risk management, boost business competitiveness, increase operational efficiency, and reduce costs.
3.1. Strengthened Supply Chain Risk Management
3.1.1. Proactive Vulnerability Analysis and Rapid Response
Complying with the guide dramatically accelerates vulnerability response times. Organizations with mature SBOM-driven vulnerability management systems can reduce response times by 30%.
During the Log4j incident, companies with SBOMs identified affected systems in minutes, while those without took weeks or even months. One software vendor testified that “an SBOM capability alone could have easily saved 240 hours”.
Japan’s Ministry of Economy, Trade and Industry (METI) reported that using SBOMs for vulnerability management in the medical device sector reduced the workload by approximately 70% compared to manual methods.
3.1.2. Automated Open Source License Compliance
By managing component license information in the standardized SPDX format, organizations can proactively prevent legal risks and fines from license violations. Automating compliance tasks, such as license scanning and policy enforcement, significantly reduces administrative overhead.
3.2. Enhanced Business Competitiveness
3.2.1. Meeting Customer and Partner Demands for SBOMs
Many System Integrators (SIs) and Software Vendors (SVs) now view SBOM adoption as a key driver for regulatory compliance and building trust. An organization with proven SBOM capabilities gains a clear competitive advantage by:
- Securing a differentiated position with security-conscious customers.
- Meeting mandatory requirements in contracts with government agencies and large corporations.
- Demonstrating compliance with global regulations like the EU’s Cyber Resilience Act (CRA) and the US Executive Order 14028.
3.2.2. Gaining an Edge in RFPs and Contracts
The ability to provide a standardized SBOM is a tangible asset that can shorten sales cycles. An API management vendor CEO noted, “Being able to present an SBOM early in the conversation enables a completely different level of dialogue.”
3.2.3. Demonstrating Compliance for Global Market Access
The guide’s foundation in the ISO/IEC 5962:2021 (SPDX) standard ensures that your SBOMs can be submitted for international procurement and exports without costly format conversions, ensuring compatibility and trust with global partners.
3.3. Increased Development and Operational Efficiency
3.3.1. Standardized and Automated Processes
By adopting a standard format (SPDX 2.2/2.3) and clear requirements, organizations can automate the SBOM generation, verification, and delivery processes. This can lead to significant time savings—over five hours per engineer per week—that can be reinvested into core development tasks.
3.3.2. Clearer Internal Guidelines for Development Teams
A consistent, organization-wide standard for SBOMs eliminates the confusion and inefficiency of redundant scans and manual management. This efficiency is accelerated by integrating automated tools into CI/CD pipelines.
3.4. Significant Cost Reduction
3.4.1. Preventing Losses from Supply Chain Attacks
A single software supply chain attack costs an average of $4.35 million, with the total annual impact projected to reach $80.6 billion by 2026. A systematic approach using the OpenChain Telco SBOM Guide can proactively prevent these multimillion-dollar losses.
3.4.2. Operational Savings through Automation
There are numerous cases of organizations saving hundreds of hours on vulnerability analysis with an SBOM. One company reported reducing its vulnerability review time “from a full day to less than an hour,” saving an estimated 500 hours per open-source project.
3.5. Simplified Regulatory and Standards Compliance
3.5.1. A Clear Path to Global Regulatory Compliance
The OpenChain Telco SBOM Guide provides a practical foundation for responding to global requirements from bodies like NTIA, CISA, and ISO. This is crucial as key regulations take full effect:
- USA: SBOM provision is mandatory for federal government software procurement.
- EU: SBOM mandates under the Cyber Resilience Act (CRA) are being actively advanced.
- Japan, South Korea: Similar policies are being rolled out.
3.5.2. Stronger Multinational Partnerships
Standardized SBOM exchange is a global imperative. Adhering to the guide ensures compatibility with third-party SBOMs, eliminating collaboration barriers. Nokia’s adoption of the guide for its internal framework is a prime example of its practicality and business value.
Chapter 4: Role-Based Applications and Scenarios
The OpenChain Telco SBOM Guide is designed to be flexible, offering distinct value depending on each stakeholder’s role within the telecommunications ecosystem. This chapter provides specific scenarios for telecom operators (consumers), equipment manufacturers (producers), solution providers (producers), and compliance officers (practitioners) to strategically leverage the guide.
4.1. For Telecom Operators (as Consumers)
Telecom operators are the primary stewards of the supply chain and key consumers of SBOMs. They procure equipment and solutions from numerous suppliers to deliver final services. Their main objective is to proactively identify security risks in procured software and ensure transparency across their entire supply chain.
4.1.1. Scenario: Verifying the Supply Chain for External Solutions
Situation: A telecom operator plans to introduce a new orchestration solution for 5G network slicing. They receive proposals from several global vendors, but the lack of standardized SBOMs makes an objective risk assessment difficult.
Applying the OpenChain Telco SBOM Guide:
Step 1: Set Clear Requirements
- Mandate Guide Compliance in RFPs: Include the submission of an SBOM in SPDX 2.2 or 2.3 format as a mandatory evaluation criterion. This establishes a single standard for quality and format.
- Require Complete SBOMs: In line with the guide, demand an SBOM that includes not only direct dependencies but also all transitive dependencies to uncover hidden security and license risks.
Step 2: Perform Quantitative Risk Assessments
- Use Automated Analysis: Feed the standardized SBOMs into an internal Software Composition Analysis (SCA) tool to automatically scan for known vulnerabilities (CVEs) and quantify their severity.
- Verify License Compliance: Analyze the license information (
PackageLicenseConcluded,PackageLicenseDeclared) to check for conflicts with internal policies or commercial use restrictions. - Assess Transparency: Use the
known unknownsfield as a metric to evaluate how transparently a vendor manages its software components.
Step 3: Ensure Continuous Management
- Define Contractual Obligations: For instance, the contract could include a clause specifying that “an updated SBOM must be provided concurrently with any software patch or version update.” As the OpenChain Project does not provide legal advice, all contractual clauses should be developed in consultation with your legal counsel.
- Guarantee Accessibility: As per the guide, ensure that web-hosted SBOMs are accessible for at least 18 months to support long-term security management and audits.
Expected Benefits:
- Rapid Threat Response: During a zero-day event like Log4j, identify affected systems across the supply chain in minutes and prioritize the response.
- Data-Driven Vendor Selection: Objectively compare supplier security levels based on standardized data, not just on business relationships.
- Stronger Security Governance: Gain a transparent view of software assets across the supply chain, simplifying compliance with regulatory audits and internal policies.
4.1.2. Tip: Specifying SBOM Requirements in RFPs and Contracts
Formalizing SBOM requirements is the most effective way to drive supplier accountability.
Standard RFP Clause Example:
“All proposals must include an SBOM compliant with the ‘OpenChain Telco SBOM Guide v1.1’ for all software products. The SBOM must be in SPDX v2.2 or v2.3 (Tag:Value or JSON format) and include all open source and commercial components, along with their transitive dependencies. SBOM quality and completeness will be a key evaluation criterion.”
Key Contractual Clauses:
- SBOM Provision and Timing: “The Supplier shall provide an SBOM compliant with the ‘OpenChain Telco SBOM Guide,’ as specified in Appendix X, concurrently with each software delivery.”
- Accuracy Warranty: “The Supplier warrants that the information in the provided SBOM is materially accurate and complete.”
- Update Obligation: “The Supplier shall provide an updated SBOM to the Client within seven (7) days of releasing a major update or security patch for the software.”
- Breach of Contract: “Failure to comply with these SBOM obligations shall be considered a material breach of this contract, and the Client may pursue remedies including, but not limited to, termination and claims for damages.”
4.2. For Telecom Equipment Manufacturers (Hardware-Coupled Producers)
Telecom equipment manufacturers develop software tightly integrated with hardware, such as firmware and embedded OS, making them critical producers of SBOMs. Their goal is to efficiently meet diverse customer requirements and demonstrate the reliability and competitiveness of their products.
4.2.1. Scenario: Automating SBOM Delivery for Network Equipment
Situation: An equipment manufacturer supplies 5G routers to global telecom operators, but varying SBOM requirements lead to costly manual work for each product release.
Applying the OpenChain Telco SBOM Guide:
Standardize Internal Processes with an ‘SBOM Factory’
- CI/CD Pipeline Integration: Integrate automated SBOM generation and validation into the CI/CD pipeline for firmware builds. A successful build is contingent on generating a compliant SBOM.
- Automate Metadata: Automatically populate the
Creatorfield with the organization name and tool version, and setSBOM Type: Buildbased on the build time to ensure traceability.
Implement Product-Centric SBOM Management
- Version Control: Integrate with Git to automatically generate and link SBOMs to each firmware version, simplifying version-specific vulnerability analysis.
- Design for Accessibility: Embed a compressed SBOM within the package or print a QR code linking to the SBOM download on product packaging.
- Ensure Integrity: Apply a digital signature (e.g., using Sigstore) to the SBOM file to prevent tampering and increase customer trust.
Establish an Efficient Customer Response System
- Provide a Single Standard: Offer a standard SBOM based on the guide to all customers by default.
- Enable Flexible Conversion: If a customer requires a different format (e.g., CycloneDX), use a conversion tool with the standard SPDX SBOM as the source for a quick response.
- Integrate with Technical Support: Train support teams to instantly access the SBOM for a specific product version to accurately answer customer questions about vulnerabilities and licenses.
Expected Benefits:
- Increased Productivity: A ‘Create Once, Use Many’ approach can reduce custom SBOM work by over 80%.
- Enhanced Trust and Competitiveness: Proactively providing a standardized, verified SBOM demonstrates product transparency and security, creating a competitive advantage.
- Simplified Global Compliance: Adherence to an ISO-based guide streamlines entry into regulated markets like the US and EU.
4.2.2. Tip: Managing SBOMs for Firmware and Embedded OS
Managing SBOMs for embedded environments requires special consideration.
Technical Implementation:
- Build System Integration: Integrate SBOM generation tools or plugins into embedded Linux build systems like Yocto or Buildroot to automatically extract component data during the build.
- Use Binary Analysis: For third-party binaries or drivers without source code, use SCA tools with binary analysis capabilities to identify components for the SBOM.
Management Processes:
- Product Lifecycle Integration: Align SBOM creation, updates, and retirement with the full product lifecycle, from development to end-of-life.
- Sync with Security Patches: When deploying a new firmware version, ensure the corresponding SBOM is updated to reflect the patch details and communicated to customers.
- Manage Legacy Products: For out-of-production but still-supported products, retroactively generate SBOMs and provide information on known vulnerabilities to minimize customer risk.
4.3. For Network Solution & Service Providers (Software-Only Producers)
Network solution and service providers are key SBOM producers in modern software environments like cloud-native, SaaS, and containers. Their goal is to develop flexible SBOM strategies that adapt to rapid technological changes and leverage this capability for a competitive service advantage.
4.3.1. Scenario: SBOM Strategy for SaaS and On-Premise Solutions
Situation: A network security company offers both a cloud-based SaaS solution and an on-premise firewall. A major client requests detailed SBOMs for both, creating challenges, especially for the continuously updated SaaS environment.
Applying the OpenChain Telco SBOM Guide:
Develop Differentiated Strategies by Solution Design distinct SBOM strategies tailored to each solution’s deployment model.
On-Premise Solution (Installable):
- Embed in Package: As recommended by the guide, embed the SBOM file directly into the installation package (e.g., RPM, DEB, MSI).
- Container-Based Deployment: For Docker/Kubernetes deployments, include the SBOM in a container image layer or store it alongside the image in a registry, following OCI (Open Container Initiative) standards.
SaaS Solution (Service):
- Tiered Service Offering: Since SaaS application is optional in the guide, structure SBOM delivery as a premium service. Offer summary information to basic customers and detailed, API-accessible SBOMs to enterprise customers for a fee, creating a new revenue stream.
- Provide a Security Portal: Offer a dedicated portal for enterprise customers to securely view and download the latest SBOMs for the service.
- Enable API-Based Access: Provide SBOM data via API to allow integration with customer security systems (e.g., SOAR).
Integrate Fully with Your DevSecOps Pipeline
- Generate SBOMs per Microservice: In a microservice architecture (MSA), generate individual SBOMs in each service’s build pipeline.
- Define Relationships: During deployment, merge the individual SBOMs into a unified SBOM using SPDX relationship definitions (e.g., DESCRIBES, CONTAINS) to clearly map the solution’s architecture.
- Automate with Continuous Deployment (CD): Establish a system where an SBOM is automatically updated whenever a new microservice version is deployed, reflecting the change in the unified SBOM in real-time.
Expected Benefits:
- Create New Business Opportunities: Position SBOM delivery as a premium security service to generate additional revenue.
- Increase Customer Retention: Strengthen partnerships with large, security-conscious customers by offering advanced, API-integrated security services.
- Demonstrate Technological Leadership: Showcase your ability to systematically manage complex SBOMs in a cloud-native environment, building a brand image as a technology leader.
4.3.2. Tip: Using SBOMs for Customer Support and Maintenance
SBOMs create significant value in post-sales support and maintenance.
Proactive Vulnerability Management:
- When a new CVE is disclosed, automatically scan all product SBOMs to instantly identify affected customers.
- Proactively notify them before they inquire: “The
[Component Name]in v2.1 of the[Product Name]you are using is affected by CVE-2025-XXXX. A patch is in development; temporary mitigation measures are available here.”
Transparent License Compliance:
- During a customer audit, provide the precise SBOM for that point in time to support license status reporting.
Efficient Maintenance:
- Before an update, compare the old and new SBOMs to proactively identify changed components and potential conflicts, reducing the risk of update failures.
4.4. For Open Source & Compliance Officers
Open source and compliance officers are the central architects of an organization’s SBOM governance. Their goal is to create clear, actionable policies that reduce developer workload while minimizing organizational risk.
4.4.1. Scenario: Establishing an Internal SBOM Policy
Situation: The head of the open source program office (OSPO) at a large company needs to create a company-wide SBOM policy but faces conflicting requirements from development, security, procurement, and legal teams.
Establishing a Policy Based on the Guide: Use the objective, internationally recognized guide as the foundation to mediate disagreements and build consensus.
Construct the Policy Framework
[Internal SBOM Management Policy] Article 1 (Purpose): To ensure software supply chain transparency and systematically manage related risks by complying with the 'OpenChain Telco SBOM Guide v1.1'. Article 2 (Scope): This policy applies to all software developed, purchased, or distributed by the company. Article 3 (Quality Requirements): All SBOMs must meet the requirements of the 'OpenChain Telco SBOM Guide' (e.g., data format, required fields, delivery method).Define Clear Departmental Roles (R&R)
- Development: Generate SPDX-format SBOMs using standard tools in the CI/CD pipeline.
- Procurement: Include standard SBOM clauses in all software purchase contracts.
- Security: Conduct regular vulnerability monitoring and analysis using SBOMs.
- Legal/Compliance: Review license information in SBOMs for compliance risks.
Standardize Processes and Tools
- Approve Standard SCA Tools: Define and support a list of official SCA tools.
- Automate Quality Gates: Use open-source tools like
sbomqsto automatically score SBOM quality during generation and fail builds that fall below a set threshold. - Provide Education and Support: Offer regular training, online guides, and internal communities to help developers follow the policy.
4.4.2. Tip: Selecting and Adopting an SBOM Tool (SCA Tool)
Successful SBOM management depends on choosing the right tool.
- Phased Adoption Plan:
- Define Requirements: List essential features based on your tech stack, budget, and security policies.
- Market Research: Select 3-4 candidate tools based on industry reports (e.g., Gartner, Forrester) and community evaluations.
- Conduct a Proof of Concept (PoC): Test the candidates on a real project to compare performance, accuracy, and usability.
- Select and Roll Out: Choose the optimal tool based on PoC results and implement a phased, organization-wide rollout, starting with a pilot team.
4.5. Collaborative Scenario: A Unified Supply Chain
The ultimate value of an SBOM is realized when it connects the entire supply chain, acting as a common language.
Integrated Scenario: A major 5G private network project involves a telecom operator, an equipment manufacturer (tier 1), and a solution provider (tier 2), all collaborating based on the OpenChain Telco SBOM Guide.
- Project Kick-off: The project contract mandates compliance with the guide for all parties. They exchange initial SBOMs to jointly analyze the system’s integrated security posture.
- Development and Integration: The solution provider delivers its SBOM to the equipment manufacturer. The manufacturer merges this with its own firmware SBOM using SPDX relationship definitions to create a unified equipment SBOM for the operator.
- Operation and Maintenance: The operator ingests the final SBOM into a central monitoring system for real-time asset management. When a zero-day vulnerability appears, the operator can instantly identify the affected equipment and solution and demand a patch from the responsible supplier.
Expected Benefits:
- End-to-End Supply Chain Visibility: Immediately pinpoint the source of a problem instead of wasting time in multi-vendor blame games.
- Maximized Collaboration Efficiency: Eliminate the costs and delays of data conversion and re-interpretation by using a shared standard.
- Strengthened Critical Infrastructure Security: Enhance the resilience of the nation’s critical telecommunications infrastructure beyond the efforts of any single company.
Chapter 5: A Phased Implementation Plan
Successfully adopting the OpenChain Telco SBOM Guide is not a one-time project but a continuous journey of cultural and procedural integration. This chapter presents a practical, three-phase plan—Assess → Build → Scale—to help your organization effectively implement and operate its SBOM management system.
5.1. Phase 1: Assess – Diagnosis and Goal Setting
Goal: To accurately assess your current state and define clear objectives.
This foundational phase is crucial for success. Rushing to adopt tools or policies without a proper diagnosis can lead to inefficient outcomes disconnected from business needs. The first step is to clearly understand your organization’s current capabilities and challenges.
5.1.1. Organizational Assessment and Maturity Evaluation
Objectively assess your organization’s current software supply chain management practices to identify risks and improvement opportunities.
Map the Current Software Supply Chain:
- Product/Service Inventory: List all software currently in development and operation to define the scope of SBOM management.
- Component Management Practices: Review how open-source and commercial components are introduced, used, and retired. Determine if management is manual (e.g., spreadsheets) or automated.
- Risk Management Process Review: Analyze existing vulnerability management and license compliance processes.
- Historical Analysis: Review supply chain-related security incidents from the past 2–3 years to identify key vulnerabilities.
SBOM Maturity Self-Assessment: Use this three-stage model to diagnose your organization’s current maturity level.
| Maturity Level | Characteristics | Key Challenges |
|---|---|---|
| Beginner (Reactive Stage) | Has a basic awareness of SBOMs but lacks concrete plans or execution. Relies on manual management. | To champion the need and value of SBOM adoption internally and secure executive buy-in. |
| Early Adopter | Is planning SBOM adoption or piloting it in some projects. Lacks a standardized, enterprise-wide process. | To establish a standard process and policy based on successful pilots and scale across the organization. |
| Innovator | Operates a standardized, automated SBOM process integrated into the CI/CD pipeline. | To leverage SBOM data for advanced strategies like predictive threat intelligence and proactive response. |
- Gap Analysis:
Based on the assessment, identify the gaps between the OpenChain Telco SBOM Guide’s requirements and your current capabilities.
- Data Format: Does your current SBOM comply with SPDX 2.2/2.3?
- Required Fields: Are all required fields (e.g.,
PackageName,PURL) included? - Process: Is there a process to deliver the SBOM concurrently with the software?
- Resources: Are the necessary tools, personnel, and budget secured?
5.1.2. Stakeholder Identification and Task Force Formation
SBOM adoption is an enterprise-wide project that requires cross-functional collaboration.
Secure Key Stakeholder Involvement:
- Development: Responsible for SBOM generation and CI/CD integration.
- Security: Responsible for vulnerability analysis and policy validation.
- Compliance/Legal: Responsible for license management and legal risk review.
- Procurement: Responsible for including SBOM requirements in supplier contracts.
- Executive Leadership: Responsible for providing strategic direction and resources.
Form an SBOM Adoption Task Force: This should be an execution-oriented team with clear Roles & Responsibilities (R&R).
- TF Lead: Manages the overall project and reports to the executive team.
- Technical Expert: Evaluates and implements tools.
- Process Architect: Designs the end-to-end SBOM workflow.
- Change Manager: Leads training and communication to drive adoption.
5.1.3. Goal Setting and Scope Definition
Set realistic, measurable goals to focus resources and define success.
Set SMART Goals:
- (Example) “By Q4 2025, automate the generation and delivery of SBOMs compliant with the OpenChain Telco SBOM Guide for our three flagship telecom equipment product lines.”
Define Scope by Priority: Expand the scope in phases based on business importance and risk.
- Priority 1 (Strategic): Core products or new flagship services delivered to external customers.
- Priority 2 (Risk-Based): Product lines subject to regulatory requirements or with high open-source dependencies.
- Priority 3 (Internal): Internally used development projects.
5.2. Phase 2: Build – Tool Selection and Process Integration
Goal: To build a sustainable, automated system based on the established plan.
This phase involves implementing the systems and processes defined in Phase 1. The key is to create an automated system that is naturally integrated into the development lifecycle.
5.2.1. SBOM Generation Tool Evaluation and Selection
Select the optimal tool for your organization’s tech stack, budget, and goals.
- Establish Tool Selection Criteria: Create an objective evaluation model by weighting criteria based on organizational needs.
| Evaluation Criteria | Details |
|---|---|
| Format Support | Ability to generate and parse SPDX 2.2/2.3 format. |
| Language/Framework Support | Coverage of key programming languages and frameworks used in-house. |
| Integration | Ease of integration with CI/CD pipelines like Jenkins and GitHub Actions. |
| Accuracy | High accuracy in transitive dependency detection; low false positive rate. |
| Scalability/Performance | Performance on large-scale projects and scalability for future growth. |
| Cost-Effectiveness | Value provided relative to license and maintenance costs. |
- Compare Tools and Conduct a Proof of Concept (PoC):
Test 2–3 candidate tools in a real development environment.
- Apply them to a pilot project to compare performance, accuracy, and usability.
- Gather developer feedback to assess practical utility.
- Conduct a Return on Investment (ROI) analysis to inform the final selection.
5.2.2. Process Design and Standardization
Design a standardized SBOM management process that fits your development culture.
Design a CI/CD-Integrated Workflow: Make SBOM generation an automated part of the development process, not an extra task.
- Code Commit: The pipeline is triggered when a developer commits code.
- Build & Scan: The code is built, and an SCA tool scans for dependencies.
- SBOM Generation: An SPDX-formatted SBOM is automatically generated.
- Quality Validation: The SBOM is automatically validated against the guide’s requirements.
- Policy Check: The SBOM is used to scan for vulnerabilities and license violations. (Fail the build if policies are violated).
- Sign & Store: A digital signature is applied, and the SBOM is stored in a central repository.
- Deploy: The SBOM is included in the final deployment package.
Document Policies and Guidelines: Provide clear, written standards for all team members.
- Corporate SBOM Policy: Defines principles and responsibilities for SBOM management.
- Tool Usage Guide: Provides step-by-step instructions and best practices.
- Quality Checklist: A self-verification checklist for guide compliance.
5.2.3. Internal Training and Capability Building
New tools and processes require sufficient training to ensure adoption.
- Customized Training Programs:
- Executives: Briefing on the strategic value and business impact of SBOMs.
- Developers: Hands-on training on tool usage and CI/CD integration.
- Security/Compliance Teams: Advanced training on SBOM-based vulnerability and license auditing.
5.3. Phase 3: Scale – Pilot Project and Enterprise Rollout
Goal: To prove value through a small success and expand across the organization.
Apply the SBOM process to a real project to verify its effectiveness, then drive company-wide adoption.
5.3.1. Execute a Pilot Project
Follow the principle: “Start small, succeed fast, and scale.”
Pilot Project Selection Criteria:
- Representative: Has moderate complexity and represents a typical project.
- Cooperative: Involves a development team that is receptive to change.
- Influential: Is a project whose success can positively influence other teams.
Pilot Execution and Performance Measurement: Run the pilot for a defined period (e.g., 8 weeks) and measure performance using Key Performance Indicators (KPIs).
| KPI Area | Measurement Metric | Example Target |
|---|---|---|
| Quality | Inclusion rate of required SBOM fields | > 95% |
| Efficiency | Automation rate of SBOM generation | > 90% |
| Security | Time to identify new vulnerabilities | 50% reduction |
| Satisfaction | Team satisfaction survey score | > 4 out of 5 |
5.3.2. Gradual Rollout Strategy
Use the successes and lessons from the pilot to create a systematic roadmap for enterprise-wide expansion.
Establish a Rollout Roadmap: Expand the scope in phases by product line and business unit.
- (Example) Phase 1 (3 months): Pilot completion & rollout to 3 core products → Phase 2 (6 months): Expansion to 50% of major product lines → Phase 3 (12 months): Enterprise-wide standardization complete.
Lead Change and Overcome Resistance:
- Communication: Transparently share the reasons for adoption and regularly communicate progress.
- Support: Operate dedicated support channels (helpdesk, internal community) to resolve issues promptly.
- Participation: Actively listen to feedback from the field and reflect it in process improvements.
5.3.3. Establish and Advance Governance
Build a continuous management system to embed SBOM management as a core competency.
- Operate an SBOM Center of Excellence (CoE): Establish an expert organization to oversee the company-wide SBOM strategy, quality management, technical support, and training.
- Create a Continuous Improvement Process: Identify improvement opportunities through quarterly performance reviews and incorporate evolving external standards and technologies.
- Measure Performance and Demonstrate Value: Quantitatively analyze the ROI of SBOM adoption—such as reduced vulnerability response times and lower license violation risks—to report to management and secure ongoing investment.
Chapter 6: Conclusion – The First Step Toward a More Secure Telco Ecosystem
6.1. The Significance and Future of the OpenChain Telco SBOM Guide
The OpenChain Telco SBOM Guide represents a pivotal step forward in securing the telecommunications software supply chain. In an era where large-scale attacks like Log4Shell and SolarWinds threaten global digital infrastructure, the guide provides a crucial solution: a specialized SBOM standard built for the telecommunications industry.
The guide’s development over 18 months, the release of Version 1.1, and its adoption as an internal framework by global leaders like Nokia prove that it is more than a document—it is an industry standard driving tangible change.
Its greatest significance lies in fostering interoperability and standardization, which maximizes efficiency across the entire industry. As Gergely Csatári of Nokia noted, the guide addresses the real-world need for “harmonization of completeness, quality, and content to ensure interoperability of SBOMs, both internally and at external interfaces.”
Furthermore, the announcement of commercial tool support from SCANOSS marks a significant milestone, signaling the guide’s evolution from a theoretical standard to a practical, automated solution.
6.2. Why You Must Start Now
The window of opportunity for proactive adoption is closing. Three key trends underscore the urgency of implementing a robust SBOM strategy today.
6.2.1. The Shifting Regulatory Landscape
The years 2025–2026 represent a critical inflection point for SBOM mandates. Key regulatory deadlines are fast approaching:
- USA: Full implementation of mandatory SBOM provision for federal government software procurement.
- EU: SBOM requirements under the Cyber Resilience Act (CRA) will be fully enforced from September 2026.
- Japan, South Korea: Acceleration of government-led SBOM adoption policies.
Experts predict that “2026 will be the real year of SBOM adoption,” making early action a competitive necessity.
6.2.2. The Exponential Growth of Supply Chain Attacks
The threat landscape continues to escalate, underscoring the urgency:
- Threats in open-source package repositories have increased by 1,300% (Source).
- Weaponized vulnerabilities have increased by 10%, with nearly 1% of all vulnerabilities actively exploited in attacks (Source).
- The average loss from a single software supply chain attack is $4.35 million (Source).
Two years after Log4Shell, 38% of applications remain vulnerable, highlighting the critical need for systematic SBOM management.
6.2.3. The Maturation of the Tool Ecosystem
The year 2025 marks a turning point as SBOM management shifts from manual effort to an automated system. Tools that support the OpenChain Telco SBOM Guide are now readily available:
- Validation Tool: The Nokia-contributed OpenChain Telco SBOM Guide Validator.
- Commercial Tool: Native support from SCANOSS.
- Next-Generation Tool: AI-based accuracy enhancement solutions like SIT.
These developments signal a decisive turning point in the history of software supply chain security.
This guide is not about pursuing a grand, unattainable transformation. It is about taking a small but definitive first step. We encourage you to take that step, use this guide to advance your organization’s software supply chain security, and help build a more resilient telecommunications ecosystem for everyone.
Appendix
Appendix A: Full Text of the OpenChain Telco SBOM Guide
- Download the official guide (English): OpenChain-Telco-SBOM-Guide_EN.md
- Download the official guide (Korean): OpenChain-Telco-SBOM-Guide_KR.md
Appendix B: Glossary
| Term | Definition |
|---|---|
| SBOM | Software Bill of Materials. An inventory listing all software components, libraries, and their dependencies that constitute a piece of software. |
| SPDX | Software Package Data Exchange. An open standard for communicating SBOM information, recognized as international standard ISO/IEC 5962:2021. |
| PURL | Package URL. A standardized URL format used to uniquely and universally identify software packages. |
| Transitive Dependency | An indirect dependency. If your project uses Library A, and Library A uses Library B, then Library B is a transitive dependency of your project. |
| NTIA Minimum Elements | A baseline set of SBOM fields defined by the U.S. National Telecommunications and Information Administration to ensure basic interoperability. |
| CreatorComment | A free-text field in the SPDX format used to record additional metadata, such as the tool used or the CISA-defined SBOM Type. |
| Known Unknowns | A field used to transparently document software components that were intentionally excluded from an SBOM, such as proprietary commercial components. |
| Tag:Value | A human-readable text format for SPDX, structured as a series of “key: value” pairs. |
| JSON | JavaScript Object Notation. A machine-readable data format ideal for automated processing and API exchange. |
| Digital Signature | A cryptographic signature applied to an SBOM file to verify its integrity and authenticity, ensuring it has not been tampered with. |
| Container SBOM | An SBOM that documents all software components within a container image, including base image layers, installed packages, and application code. |
| SaaS SBOM | An SBOM for a Software-as-a-Service application. The OpenChain Telco SBOM Guide defines this as optional but recommended for enterprise customers. |
Appendix C: Frequently Asked Questions (FAQ)
Q1. Do I have to use a specific tool to create an SBOM?
A. No. The guide is tool-agnostic and only defines the requirements for the final output (SPDX 2.2/2.3 format). You are free to choose any Software Composition Analysis (SCA) tool—such as Syft, FOSSA, SCANOSS, or Black Duck—that best fits your technology stack and budget.
Q2. Is providing an SBOM for our SaaS offering mandatory?
A. The guide defines SBOMs for SaaS as optional (MAY), recognizing the operational complexities. However, it is a recommended best practice, especially for enterprise customers who require transparency. If you choose to provide one, you can deliver it through a secure customer portal or via API.
Q3. How can I quickly verify if an SBOM complies with the guide?
A. To verify compliance, check that the SBOM meets these key requirements:
- Format: Adheres to SPDX 2.2 or 2.3 in either Tag:Value or JSON format.
- Completeness: Includes all required fields for Document Creation, Package, and Relationship Information.
- Traceability: Contains creator information, tool version, and the appropriate CISA SBOM Type (e.g., Build, Source).
- Scope: Covers all open source and transitive dependencies.
- Integrity: Includes a digital signature (recommended) to ensure the file is authentic and unaltered.
Q4. How should we update an existing, non-compliant SBOM?
A. Follow these steps:
- Analyze: Scan the existing SBOM to identify missing fields and format inconsistencies compared to the guide’s requirements.
- Enrich: Use an SCA tool to re-scan the software and add missing data, such as PURLs, license information, and transitive dependencies.
- Convert: Transform the enriched data into the required SPDX 2.2/2.3 format (Tag:Value or JSON).
- Update Metadata: Add the required
Creator,Created, andCreatorCommentfields. - Verify: Apply a digital signature and use a validator tool to confirm full compliance.
Q5. How can we generate an SBOM for a legacy product with limited source code access?
A. For legacy products, a multi-faceted approach is needed:
- Binary Analysis: Use an SCA tool with binary analysis capabilities to generate an SBOM directly from the compiled artifacts.
- Documentation: Supplement the analysis with information from existing build scripts, developer notes, and product documentation.
- Transparency: If some components cannot be identified, explicitly list them as
known unknownsto maintain transparency. - Delivery: If embedding the SBOM is not possible, provide it via a web-hosted link, ensuring access for at least 18 months.
Q6. When and how should we merge multiple SBOM files?
A. Merging is necessary when a single product is assembled from multiple, independently developed components (e.g., microservices, firmware + application). You can use SPDX’s Relationship fields (like CONTAINS or DESCRIBES) to define how the individual SBOMs relate to each other, creating a single, comprehensive SBOM for the entire product. Tools like sbomasm can automate this process.
4 - Templates
4.1 - Open Source Policy
Note:
This sample open source policy was written with reference to the following two materials.
1. Purpose
(1) Purpose of the Policy
This policy provides the following principles for the entire organization involved in software development, service, and distribution at the OOO company (hereinafter referred to as “the company”) to properly utilize open source software (hereinafter referred to as “open source”).
- Principles of open source compliance / security assurance
- Principles of contribution to external open source projects
- Principles for releasing internal projects as open source
These principles provide a way for all members of the company to understand the value of open source, use open source correctly, and contribute to the open source community.
All members of the company can check the open source policy at the following link on the internal wiki: [internal_link]
(2) Impact of Non-compliance
If this policy is not complied with, the following situations may occur:
- You may receive a request for open source license compliance from outside.
- You may have to disclose the source code developed by the company against your will.
- You may be sued by the open source copyright holder.
- You may be fined for copyright infringement and breach of contract, or receive an order to stop selling products.
- The company’s reputation may be damaged.
- You may be claimed for damages due to breach of contract with the supplier.
- You may be exposed to serious security incidents, causing significant damage to the company.
For these reasons, the company takes violations of the open source policy seriously, and members or organizations that violate it may be subject to disciplinary procedures.
(3) How Members Can Contribute
All members of the company can contribute to the effectiveness of the policy and the improvement of the company’s compliance level by understanding the basis and content of this policy and faithfully performing the necessary activities.
2. Scope of Application
This policy applies to the following three parts:
- It applies to all products provided or distributed by the company. However, the use of open source for internal use only is not included in the scope of this policy.
- It applies when members contribute to external open source projects.
- It applies when internal code is released as open source.
The scope of application can be changed to suit the company’s business environment. In particular, the Open Source Program Manager investigates at least once a month whether there are products that are not applied and are distributed or serviced externally to ensure continuous effectiveness. This is used as a criterion for changing the scope of application when even one case is found.
The procedure for changing the scope of application is as follows:
- If the Open Source Program Manager determines that changes to the scope of application of the policy are necessary due to changes in the company’s business environment such as new business and organizational restructuring, he/she submits a proposal to the OSRB.
- The OSRB approves an appropriate level of change in the scope of application.
- The OSRB modifies the open source policy to change the scope of application.
The Open Source Program Manager continuously reviews, updates, and inspects the scope of application at least once a month to improve it, and documents the history using the Jira Issue Tracker.
3. Terminology
- SBOM (Software Bill of Materials): List of software components
- Software Distribution Participants: Refers to all employees involved in software development, distribution, and contribution in the company, including software developers, distribution engineers, quality engineers, etc.
- …
4. Roles, Responsibilities, and Competencies
The following roles, responsibilities, and competencies required for each role are defined to ensure the effectiveness of the policy.
The responsible organization/person and the level of required competencies for each role are defined in [Appendix 1. Status of Responsible Persons].
- The Open Source Program Manager regularly updates the list according to the company’s business situation.
- The head of the organization responsible for each role appoints a person in charge within the organization and allocates appropriate time and budget to ensure that the person in charge can faithfully perform the role.
- If the person in charge of each role finds that they are not being properly supported in performing their role, they should raise the issue with the Open Source Program Manager.
- The Open Source Program Manager discusses problem-solving with the head of the organization. If it is not resolved appropriately, the Open Source Program Manager can request problem-solving from the OSRB.
- The OSRB shares the issue with the head of the upper organization and requests a solution.
(1) OSRB
The OSRB (Open Source Review Board) is a consultative body composed of the Open Source Program Manager and responsible persons from related organizations such as the legal team, patent team, development team, infrastructure team, etc., for managing open source in the company.
- The OSRB establishes policies and processes for managing open source in the company and defines the roles and responsibilities within the company to implement them.
- The OSRB reviews and improves policies and processes annually. All improvement processes are documented and recorded.
- The OSRB always updates the policies and processes for open source compliance and security assurance to reflect the business environment by analyzing the company’s process performance, shortcomings, and best practices.
- The Open Source Program Manager is responsible for managing the policies and processes for open source compliance.
- The security officer is responsible for managing the policies and processes for open source security assurance.
- The OSRB discusses solutions and prepares countermeasures when open source issues occur within the company.
- The OSRB reports issues to the executive management when necessary and receives feedback on risk mitigation measures.
(2) Open Source Program Manager
The Open Source Program Manager is responsible for the overall responsibility of the company’s open source program. It has the following responsibilities to ensure the management activities of open source used in products and services:
- Defines the roles necessary for open source compliance and assigns the responsible organization and person for each role. Consults with the OSRB if necessary. The internal responsibility for open source security assurance is assigned by the security officer.
- Organizes and evaluates open source education.
- Serves as the chairman of the OSRB and directs activities.
- Responds to inquiries and requests related to open source use and compliance from outside.
- Reviews and approves open source use requests.
- Maintains SBOM records.
- Provides a way for members to receive open source related advice.
- Maintains a repository for open source notices and source code disclosure.
(3) OSPO
The Open Source Program Office (OSPO) supports and nurtures open source activities both inside and outside the company.
- It provides guidelines for contributing code to external open source projects.
- It provides guidelines for releasing internal projects as open source.
- It develops and operates an open source portal.
- It develops and selects open source tools.
- It sponsors open source project events.
- It manages relationships with open source communities.
(4) Legal Officer
The Legal Officer provides advice on legal risks and mitigation measures that may arise in the process of using open source, such as interpreting open source licenses and obligations.
- It provides a reasonable method for members to inquire about open source compliance issues.
- It provides advice on license and intellectual property issues, including conflicts due to incompatible open source licenses.
- It reviews necessary legal matters such as open source licenses, CLA (Contributor License Agreement), etc. when contributing to external open source projects.
- In acute cases, it requests advice from external law firms with open source specialist lawyers.
(5) IT Officer
The IT Officer operates open source analysis tools and automates them to build a system that allows open source analysis to be smoothly performed for all distributed software.
- It operates open source analysis tools.
- It integrates with the DevOps environment to automate open source analysis.
- It builds systems and processes to perform open source analysis for all distributed software.
- It secures and maintains SBOM for all distributed software.
(6) Security Officer
The Security Officer operates open source security vulnerability analysis tools to build a system that allows security vulnerability analysis to be smoothly performed for all distributed software.
- It assigns responsibilities for each task to ensure successful open source security assurance.
- It operates open source security vulnerability analysis tools.
- It integrates with the DevSecOps environment to automate open source security vulnerability analysis.
- It builds systems and processes to perform open source security vulnerability analysis for all distributed software.
- It provides a reasonable method for members to inquire about security vulnerabilities, and uses external expert technical advice if necessary to resolve vulnerabilities.
(7) Development Culture Officer
The Development Culture Officer supports in-house developers to actively use open source and participate in in-house and external communities to acquire advanced development culture.
- It encourages participation in open source communities.
- It creates a culture that recognizes active external open source project activities as in-house performance.
- It creates a development culture that can be recognized as an attractive company by open source developers.
(8) Quality Assurance Officer
The Quality Assurance Officer, such as QA, checks whether the open source license obligations have been properly performed when distributing software.
- It checks whether open source management activities are performed according to the development process stage.
- It checks whether the deliverables are created as required by the open source license.
- It checks whether the open source notice and the source code to be disclosed are provided together when distributing software.
- If there is an issue, it notifies the software development/distribution organization and guides them to correct the issue immediately.
5. Education and Evaluation
All members who are responsible for the roles defined in Chapter 4 must take the advanced open source education course provided by the [Learning Portal]. Through this, they will familiarize themselves with the open source policy, related education policy, and how to look it up.
The education history and evaluation results are kept in the [Learning Portal] for at least 3 years.
6. Open Source Use
When developing and distributing products and services using open source, you must comply with the obligations required by each open source license. This activity is called open source compliance.
For proper open source compliance activities, the software development/distribution organization complies with the following matters and all processes are recorded and preserved in the Jira Tracker.
(1) Open Source Identification and License Obligation Review
When introducing open source to product/service development, first identify what the open source license is, and review and confirm the obligations required by the license.
The company’s [Open Source License Guide] includes a list of major open source licenses, and explains the obligations required by each license according to the following types of distribution:
- Binary form
- Source form
- Strong/Weak Copyleft
- SaaS-based provision
- Whether modified
- Including open source that requires author indication, etc.
The software development/distribution organization can refer to this guide when reviewing open source license obligations. If you need to review an open source license not mentioned in this guide, contact the open source program manager.
(2) Open Source License Consideration Design
Understand the combination relationship of open source and design the software architecture so that our code is not affected by the open source license.
The company’s [Open Source License Guide] explains the range of source code disclosure for each open source license and how to design to prevent the disclosure of our code.
(3) Creation of Open Source Compliance Deliverables
The most basic of open source compliance activities is to understand the status of open source included in distributed software. This is to properly meet the core of open source compliance, which is the requirements of the open source license. In other words, you need to create a set of compliance deliverables for the open source included in the distributed software.
Open source compliance deliverables are divided into two main categories.
- Open Source Notice: A document for providing the full text of the open source license and copyright information
- Source Code Package to be Disclosed: A package that collects the source code to be disclosed to fulfill the obligations of open source licenses that require source code disclosure, such as GPL, LGPL
To collect, distribute, and store these compliance deliverables, comply with the following matters.
- The open source notice or source code package to be disclosed is collected according to the conditions required by each license. For example, if the license requires the entire text of the license to be enclosed, you cannot just provide a link.
- The collected deliverables are stored in a separate repository.
- If the source code to be disclosed is provided by a written agreement, the download link is made public so that the repository of the collected deliverables can be accessed from the outside.
You can issue an open source notice and collect a source code package to be disclosed through the company’s open source process.
(4) Creation of SBOM (Bill of Materials)
You must create and manage the status of open source included in distributed software (BOM: Bill of Materials).
You can create and preserve SBOM using open source tools through the company’s open source process.
(5) Compliance Issue Response Procedure
If a compliance issue is raised, the open source program manager performs the following procedures to respond quickly.
- Confirm the inquiry receipt and specify a reasonable resolution time.
- Check whether the issue content is pointing out a real problem. (If not, inform the issue raiser that it is not a problem.)
- If it is a real problem, prioritize and decide on an appropriate response.
- Perform the response and, if necessary, appropriately supplement the open source process.
- The above contents are preserved using the Jira Tracker.
(6) Open Source Vulnerability Response
- We identify open source vulnerabilities and evaluate their severity.
- Based on the analysis of open source vulnerabilities, we either fix the vulnerability or apply a security patch. The decision to address vulnerabilities takes into account the severity of the vulnerability, the importance of the system, and the availability of vulnerability fixes or security patches.
- We monitor the announcement of new open source security vulnerabilities and respond quickly when vulnerabilities occur. Open source vulnerability monitoring can be performed through vulnerability databases such as CVE and websites of security specialist organizations.
7. Open Source Contribution
The company encourages participation and contribution to external open source projects to create business value from open source. However, care must be taken to avoid unintentional exposure of the company’s intellectual property or infringement of third-party rights during this process. To this end, members of the company must comply with the following when contributing to external open source projects:
(1) Request for Review and Approval
Contributing to open source is granting the open source project the right to modify, use, and distribute the work from a copyright perspective. Sometimes, you may need to transfer your copyright to the open source project. However, the copyright of works created during the employment period is generally owned by the employer. In other words, the works created by company members are owned by the company. The act of arbitrarily contributing works to open source can trigger unnecessary copyright infringement issues.
Therefore, if there is an open source project you want to contribute to, you must comply with the review request and approval process before making the initial contribution according to the open source contribution process.
However, in the case of simple content such as the following, you can contribute according to the judgment of the member without the review process because the risk of copyright infringement is not high:
- Small code snippets of 10 lines or less
- Questions / Answers on Stack Overflow
- Management activities on GitHub: Creating Issues, Reviewing / Approving Pull Requests, etc.
(2) Only Contribute Code You Have the Right to Contribute
You should only contribute code that you have the right to contribute. In other words, you contribute code that you have written yourself. You should not arbitrarily contribute third-party code.
(3) Be Careful About Intellectual Property Exposure
Do not contribute code or documents that may expose sensitive information or company intellectual property, such as patents.
If the code you want to contribute contains a company patent, you need to check whether this patent can be contributed to the project under an open source license. If there is any ambiguity, contact the OSPO.
(4) Be Careful About Signing the CLA
Some open source projects require all contributors to sign the CLA (Contributor License Agreement). This is an agreement that seeks consent from contributors to reduce copyright disputes that can arise while the project manages the works of multiple contributors. Typically, projects led by large corporations require you to sign the CLA.
The CLA varies from project to project, but it usually contains the following:
- I (or my affiliated company) have the right to contribute the contribution I want to contribute to the project. (In other words, I am the author of this contribution.)
- I (or my affiliated company) grant the project the right to modify, distribute, and manage my contribution.
- I (or my affiliated company) will not revoke the granted rights.
- I (or my affiliated company) grant the project the right to change the license as needed in the future.
Also, although rare, some CLAs require agreement on the following conditions:
- I (or my affiliated company) transfer my copyright to the project or project management organization at the same time as I contribute my contribution.
The company does not allow contributions to open source projects that require copyright transfer to protect its intellectual property. To make this judgment, company members must request a review from the OSPO before signing if the open source project they want to contribute to requires signing the CLA.
(5) Copyright Notice
The intellectual property of the works created by members during their employment is basically owned by the company. Therefore, when members contribute code to an external open source project, they must indicate the company’s copyright.
When contributing one or more files, indicate the copyright and license at the top of the file as follows:
Copyright (c) {$year} {$Company}
SPDX-License-Identifier: {$SPDX_license_name}
Here, $SPDX_license_name is written according to the license policy of the open source project in question.
However, if you are modifying existing code for purposes such as bug fixes, you do not need to indicate copyright for the code modification.
(6) Use of Company Email
When contributing to an open source project, do not use personal email, use company email. Through this, (1) members have a sense of responsibility to communicate with the community on behalf of the company, and (2) the company can improve its recognition as a company that actively contributes to the open source community.
8. Open Source Release
The company respects the value of collaboration with the open source community and encourages the release of internal software to open source projects. However, there are a few rules to follow to protect the company’s intellectual property and prevent unintended copyright infringement.
(1) Approval
Open source release is granting anyone the right to modify, use, and distribute the work through an open source license from a copyright perspective. Generally, the copyright of works created during the employment period is owned by the employer. In other words, the works created by company members are owned by the company. The act of arbitrarily disclosing works to open source can trigger unnecessary copyright infringement issues.
Therefore, if you want to disclose software as open source, you must follow the review request and approval process according to the company’s open source release policy.
If there is anything that seems undesirable in the process of release, do not hesitate to contact the OSPO.
(2) Only Disclose Code You Have the Right to Disclose
One of the worst situations that can occur in an open source project is the inclusion of legally problematic code in the project. Code that the company does not have the right to distribute, or code that infringes on the IP of another company, such as a patent, can cause legal problems. Therefore, while preparing to disclose the code, check the source of all code and remove any code that may be problematic.
(3) Be Careful About Intellectual Property Exposure
Do not disclose code or documents that may expose sensitive information or company intellectual property, such as patents.
If the code you want to disclose contains a company patent, you need to check whether this patent can be disclosed under an open source license. If there is any ambiguity, contact the OSPO.
(4) Disclose Useful Code
In order to be a successful project, it must also be useful to others. If a similar project already exists, participate in the existing project rather than creating a new one.
The open source you want to disclose should (1) provide differentiated value to the open source community, (2) solve problems that the community has not been able to solve, and (3) be expected to attract positive attention by disclosing our technology.
- Do not disclose code that could not be used in actual products or services as open source.
- Do not disclose code that deals with problems already solved in the open source community. In this case, contribute to the existing open source project.
(5) Resource Allocation
- Secure the resources that need to be invested in the project.
- Initially, you need developers at a level similar to general internal projects.
- You need developers who can quickly review contributions from outside.
- The roles of the legal and marketing teams are also needed.
Secure a budget for the infrastructure needed to maintain and manage the project. This includes project hosting tools like GitHub. If you cannot create an environment that supports sufficient resources, do not disclose it as open source.
(6) Use of Company Email
When conducting open source release activities, use company email instead of personal email. This has the following benefits:
- Members have a sense of responsibility to communicate with the community on behalf of the company.
- The company can improve its recognition as a company that actively discloses to the open source community.
9. Response to External Inquiries
(1) Responsibility for Responding to External Inquiries
The Open Source Program Manager is responsible for responding to inquiries and requests about open source from outside.
- The Open Source Program Manager can assign all or part of the processing of inquiries to appropriate personnel within the company. If necessary, consult with a legal officer to handle it.
- Anyone who receives an open source inquiry from outside informs the Open Source Program Manager so that a quick response can be made.
(2) Public Contact Information
The Open Source Program Manager provides contact information publicly so that outsiders can make inquiries and requests related to open source.
- Provide an email address where you can be contacted in the open source notice.
- Provide email address information on the open source website.
- Register your contact information in the Open Compliance Directory of the Linux Foundation.
(3) External Inquiry Response Procedure
If you respond quickly and accurately to open source inquiries from outside, you can greatly reduce the risk of claims or legal litigation. To this end, the company complies with the external inquiry response procedure defined in the company’s open source process to respond to external open source inquiries.
10. Declaration and Maintenance of Compliance with ISO Standards
The company supports the spirit of the OpenChain project of the Linux Foundation for improving the level of open source compliance in the software supply chain and actively participates.
- The company guarantees compliance with ISO/IEC 5230:2020 as of October 1, 2021, by applying this open source policy.
- The company guarantees that it meets all the requirements of OpenChain Specification Version 2.1, ISO/IEC 5230:2020 for more than 18 months after obtaining conformity certification.
- The company reviews conformity at least every 18 months and changes and updates policies as needed.
Appendix 1. Status of Responsible Persons
| No | Role | Responsibility | Required Skills | Responsible Organization | Person in Charge |
|---|---|---|---|---|---|
| 1 | Open Source Program Manager | Responsible for overseeing the company’s open source program. | 1. Understanding of software development process 2. Understanding of intellectual property related to open source licenses such as copyright and patents 3. Expert knowledge of open source compliance 4. Open source development experience 5. Communication skills | CTO | OOO |
| 2 | Legal Officer | Interprets the obligations of open source licenses and provides advice to mitigate legal risks that may arise in utilizing open source to fulfill these obligations. | 1. Basic knowledge of the open source ecosystem 2. Expert knowledge of software copyright 3. Expert knowledge of open source licenses | Legal Team | OOO |
| 3 | IT Officer | Operates and automates open source analysis tools to build a system that allows open source analysis to be performed smoothly for all software for distribution. | 1. Basic knowledge of open source compliance process 2. Understanding of open source analysis tools 3. Expert knowledge of IT infrastructure | IT Infrastructure Team | OOO |
| 4 | Security Officer | Operates open source vulnerability analysis tools to build a system that allows vulnerability analysis to be performed for all software for distribution and ensures that discovered vulnerabilities are remedied according to standards. | 1. Broad understanding of DevSecOps 2. Understanding of open source vulnerability analysis tools 3. Expert knowledge of open source vulnerabilities 4. Communication skills | Security Team | OOO |
| 5 | Development Culture Officer | Supports internal developers to actively utilize open source and participate in internal and external communities to acquire advanced development culture. | 1. Understanding of software development process 2. Basic knowledge of open source compliance 3. Understanding of open source policy | DR | OOO |
| 6 | Business Department | Software development/distribution organizations comply with open source policy and process for proper open source utilization. | 1. Understanding of software development process 2. Basic knowledge of open source compliance 3. Understanding of open source policy 4. Basic knowledge of open source licenses | Development Team | All members |
4.2 - Open Source Process
The OO Company (hereinafter referred to as the “Company”) actively utilizes open source software in the development of products and services that include software. The Company must perform appropriate activities to detect open source security vulnerabilities and follow-up measures, and to comply with the obligations imposed by open source licenses when distributing software, in order to minimize open source risks. We follow the open source process to ensure these activities.
1. Open Source Process
The open source process defines the procedures that the Company must perform to comply with open source license obligations and resolve open source security vulnerabilities according to each development stage for developing and distributing software products and services. All members involved in the development/distribution of software products comply with the following 11 steps of the open source process.
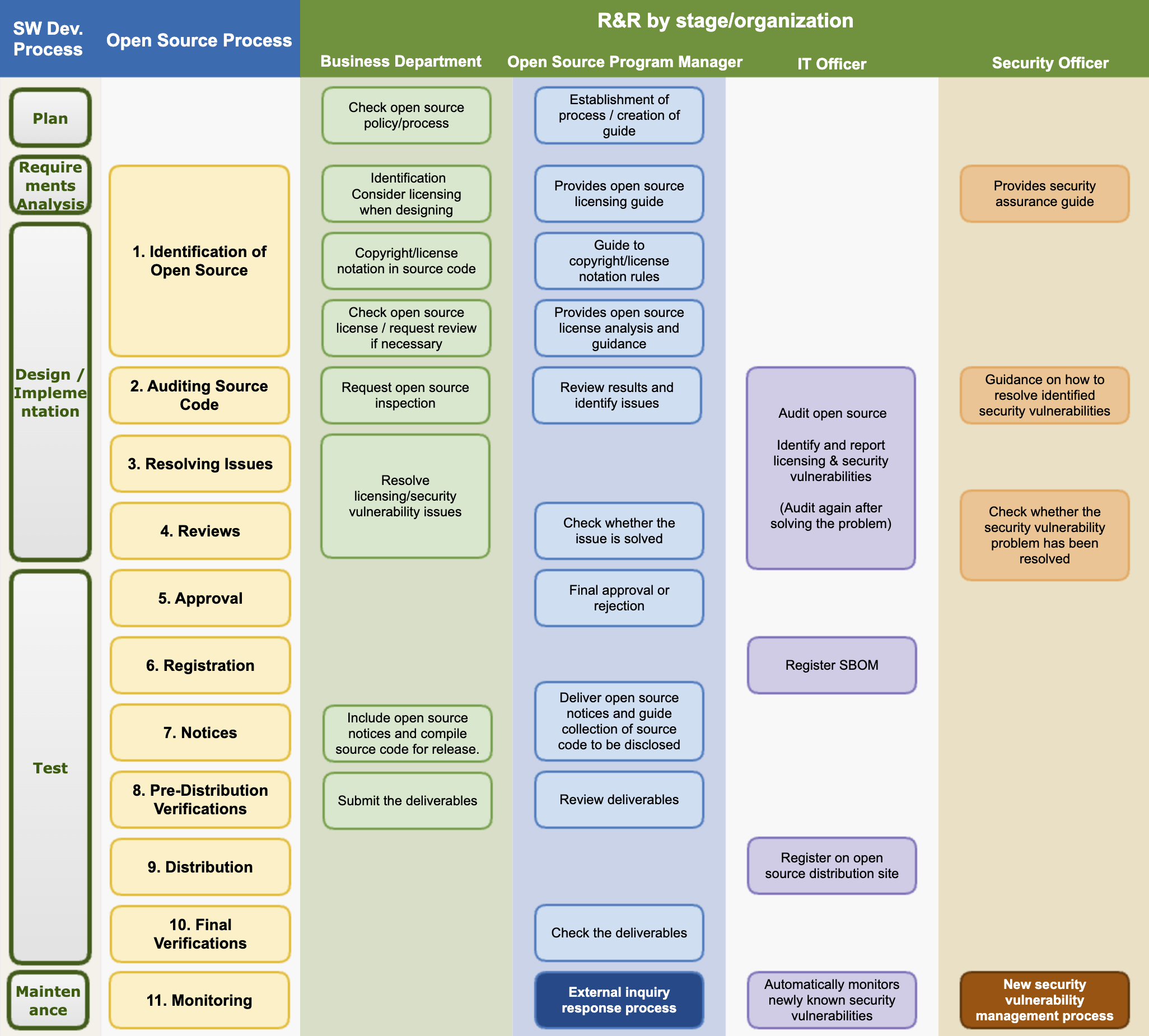
The Company strives to provide safe and stable software products and services to customers by minimizing open source risks through the open source process.
The open source program manager should review the process at least once a year to spread internal best practices and improve areas that are lacking.
(1) Identification of Open Source
The business department complies with the following matters at the software design stage.
- Identify the foreseeable open source usage status and check the license when designing the software.
- Check the obligations of each open source license. The obligations of each license can be checked in the Company’s open source license guide: https://sktelecom.github.io/guide/use/obligation/
- Design the software considering the source code disclosure range of each open source license.
The open source program manager creates and publishes a guide on the obligations, restrictions, and rights of major open source licenses so that the business departments of the entire company can refer to it. This guide should include the following use cases so that general open source license use cases can be managed.
- Distribution in binary form
- Distribution in source form
- Integration with other open sources that trigger additional license obligations
- Inclusion of modified open source
The business department marks copyright and licenses in the source code according to the company’s rules. The company’s rules for marking copyright and licenses in the source code can be checked on the following page. (insert_link)
When the business department reviews the introduction of new open source, it first identifies the license. Check the license obligations, restrictions, and rights according to the company’s open source license guide. If it is a license not explained in the company’s open source license guide, ask the open source program manager about the possibility of introduction and precautions. Create a Jira Ticket for inquiries.
The open source program manager analyzes the obligations of the open source license and guides the software development organization.
- If there is any doubt, request advice from the legal manager and provide clear guidance.
- The newly analyzed license information is reflected in the company-wide license guide.
The security manager provides a guide for the company’s security assurance.
(2) Auditing Source Code
The business department requests an open source inspection according to the guidance of the IT manager and provides the source code.
The IT manager uses an open source analysis tool to inspect the open source and create an SBOM (Software Bill of Materials).
The open source program manager reviews whether the open source license obligations can be complied with and whether there is a conflict between the open source licenses, and if there is an issue, requests the business department to resolve it. Issue matters are created as Jira Tickets and assigned to the business department.
The security manager reviews the known vulnerabilities detected and provides a response guide to the business department according to the pre-defined Risk classification criteria. Risk is classified by CVSS (Common Vulnerability Scoring System) Score, and Critical Risk is advised to establish a plan that can be dealt with within 1 week.
| Risk | CVSS 2.0 | CVSS 3.0 | Recommended action schedule |
|---|---|---|---|
| Low | 0.0 - 3.9 | 0.0 - 3.9 | - |
| Medium | 4.0 - 6.9 | 4.0 - 6.9 | - |
| High | 7.0 - 10.0 | 7.0 - 8.9 | Within 4 weeks |
| Critical | - | 9.0 - 10.0 | Within 1 week |
(3) Resolving Issues
The business department resolves all problems found in the source code inspection stage.
Remove the open source that has become an issue or replace it with open source under a different license. In the case of security vulnerability issues, measures such as replacing with a version in which known vulnerabilities have been fixed are taken.
When the business department resolves all discovered issues, it resolves the Jira Ticket issue and requests a re-review.
(4) Reviews
The open source program manager reviews whether all issues have been properly supplemented. If necessary, the source code inspection is re-performed using an open source analysis tool.
The security manager reviews whether all serious vulnerabilities have been resolved. If there are vulnerabilities that are difficult to resolve, the possibility of approval is reviewed considering the business form and service exposure status.
(5) Approval
The open source program manager finally approves or rejects whether the open source compliance procedure has been properly performed. If rejected, it proposes a reason and a correction method to the business department.
(6) Registration
The open source program manager finalizes the BOM to track the open source usage list for each version of the software.
The IT manager registers the finalized BOM in the system. The BOM includes a list of open sources included in the software for distribution and the following information.
- Product (or service) name and version of the software for distribution
- Open source list
- Open source name / version
- Open source license
The open source program manager finalizes the BOM to track the open source usage list for each version of the software.
(7) Notices
The open source program manager creates an open source notice to comply with the notice obligation. The open source notice includes the following contents.
- Open source contact that can be contacted for open source related inquiries
- Notice content for each open source
- Copyright
- Open source license name
- Copy of open source license
- (If applicable) Written agreement to obtain a copy of the source code
The open source program manager creates an open source notice and delivers it to the business department. At this time, if the source code needs to be disclosed, it guides the business department on how to collect the source code to be disclosed.
The business department includes the open source notice when distributing the product. If it is a product with a screen, it takes measures so that the user can check it through the menu. (Example: App > Menu > Settings > Copyright Information > Open Source License)
The business department collects the source code to be disclosed by checking the source code disclosure range when using open source under a license that requires source code disclosure such as GPL, LGPL, etc.
- The source code collected to comply with the obligations of licenses such as GPL, LGPL, etc. must match the source code that constitutes the binary loaded on the product. In other words, the collected source code should be the same as the binary loaded on the product when built.
(8) Pre-Distribution Verifications
The business department submits the following deliverables to demonstrate that open source compliance activities have been appropriately performed:
- The final open source notice included in the product
- Materials confirming the inclusion of the open source notice in the product (e.g., a screenshot showing the open source notice)
- (If applicable) Source code to be disclosed (submitted as a single compressed file)
The open source program manager reviews the materials submitted by the business department to check for any issues.
(9) Distribution
The open source program manager submits the compliance deliverables provided by the business department to the IT manager.
The IT manager registers the compliance deliverables on the company’s open source distribution site.
(10) Final Verifications
The open source program manager comprehensively verifies whether the compliance deliverables have been properly registered on the company’s open source portal and whether they can be downloaded without issues from outside.
(11) Monitoring
The open source program manager periodically checks for products with inadequate generation of open source compliance deliverables. They also operate a process to respond quickly to external inquiries. The detailed procedure for responding to external inquiries follows [2. External Inquiry Response Process].
The security manager operates a process to monitor and respond to newly known vulnerabilities. The detailed procedure for responding to new security vulnerabilities follows [3. New Security Vulnerability Management Process].
2. New Security Vulnerability Management Process
We adhere to the following process to take appropriate action according to the risk when a new security vulnerability is reported after a product/service has been launched in the market.
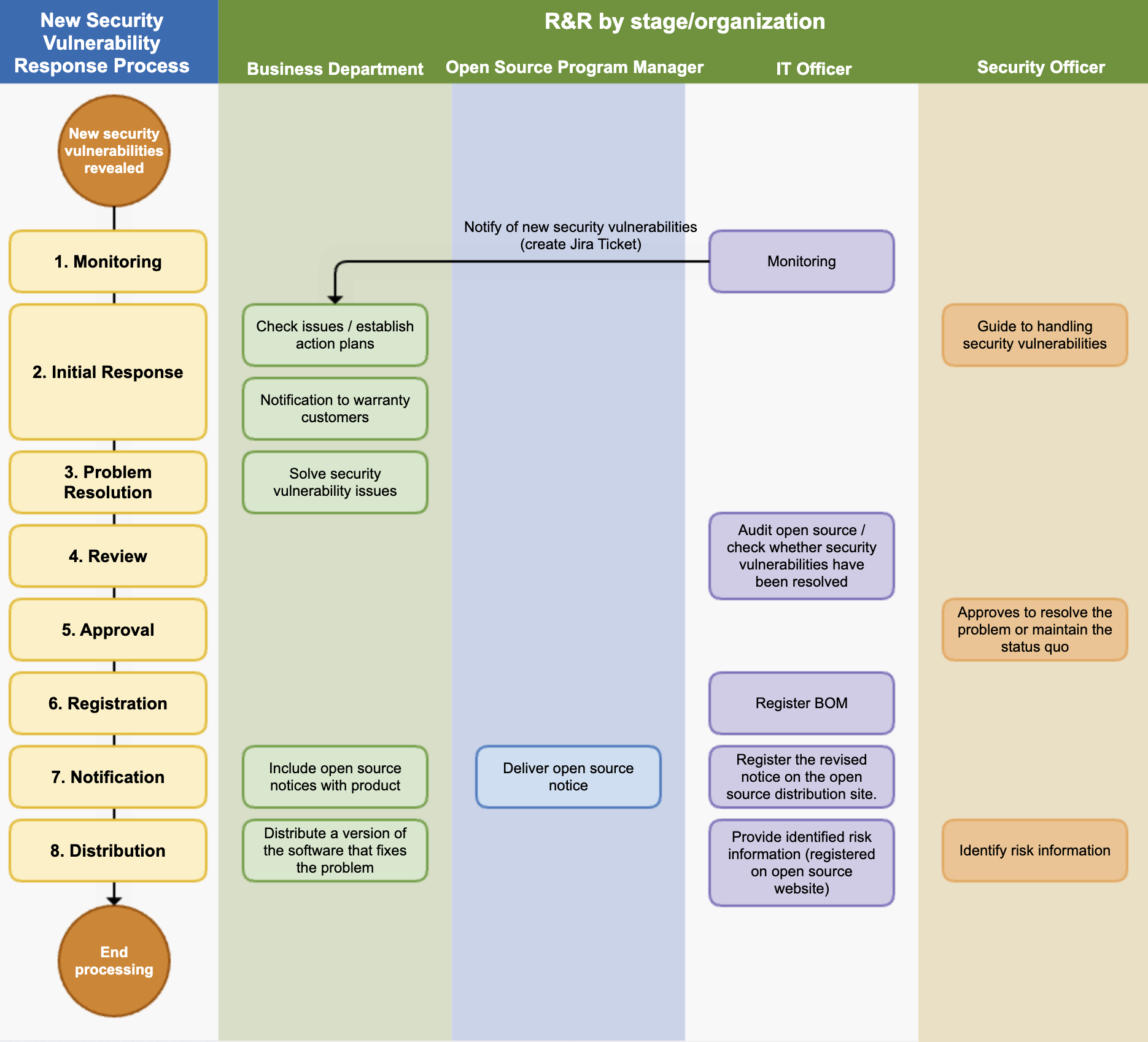
(1) Monitoring
The IT manager operates a system to monitor new security vulnerabilities. This system performs the following functions:
- It periodically collects information about newly disclosed security vulnerabilities.
- If an open source with a newly known vulnerability is used in a product/service that has already been released, it sends a notification to the business department manager responsible for that product/service. From the notification to the review, action, and resolution, everything is documented using the Jira Issue Tracker.
(2) Initial Response
The security manager provides a response guide to the business department according to the predefined risk classification criteria. The risk is classified by the CVSS (Common Vulnerability Scoring System) score, and a plan that can be implemented within one week is recommended for Critical Risk.
| Risk | CVSS 2.0 | CVSS 3.0 | Recommended Action Schedule |
|---|---|---|---|
| Low | 0.0 - 3.9 | 0.0 - 3.9 | - |
| Medium | 4.0 - 6.9 | 4.0 - 6.9 | - |
| High | 7.0 - 10.0 | 7.0 - 8.9 | Within 4 weeks |
| Critical | - | 9.0 - 10.0 | Within 1 week |
If a product/service that has already been released has a new security vulnerability, the business department establishes an action plan according to the response guide provided by the security manager.
If there are customers who need assurance, the business department notifies them of the confirmed known vulnerabilities by email or other means as necessary, depending on the risk.
(3) Problem Resolution
The business department resolves the security vulnerability issue by deleting the problematic open source or replacing it with a patched version, according to the established action plan. Once all issues are resolved, a review is requested.
(4) Review
The IT manager uses open source analysis tools to confirm whether the problem has been appropriately resolved.
(5) Approval
The security manager reviews whether all serious vulnerabilities have been resolved. If there are vulnerabilities that are difficult to resolve, the approval is reviewed considering the business form and service exposure status.
(6) Registration
The IT manager registers the SBOM, which has resolved the open source security vulnerability, in the system.
(7) Notification
The open source program manager generates an open source notice based on the SBOM that has resolved the open source security vulnerability and delivers it to the business department.
The business department replaces the open source notice included in the product distribution.
The IT manager registers the modified open source notice on the company’s open source distribution site.
(8) Distribution
The business department redistributes the software version that has resolved the open source security vulnerability issue.
The security manager identifies whether there is risk information that needs to be disclosed to third parties, and if there is, it is delivered to the IT manager.
The IT manager registers the identified risk information on the open source website so that third parties can check it.
3. External Inquiry Response Process
If you respond quickly and accurately to open source compliance inquiries from outside, you can greatly reduce the risk of proceeding to litigation. To this end, companies comply with the following process to respond to external open source compliance inquiries.
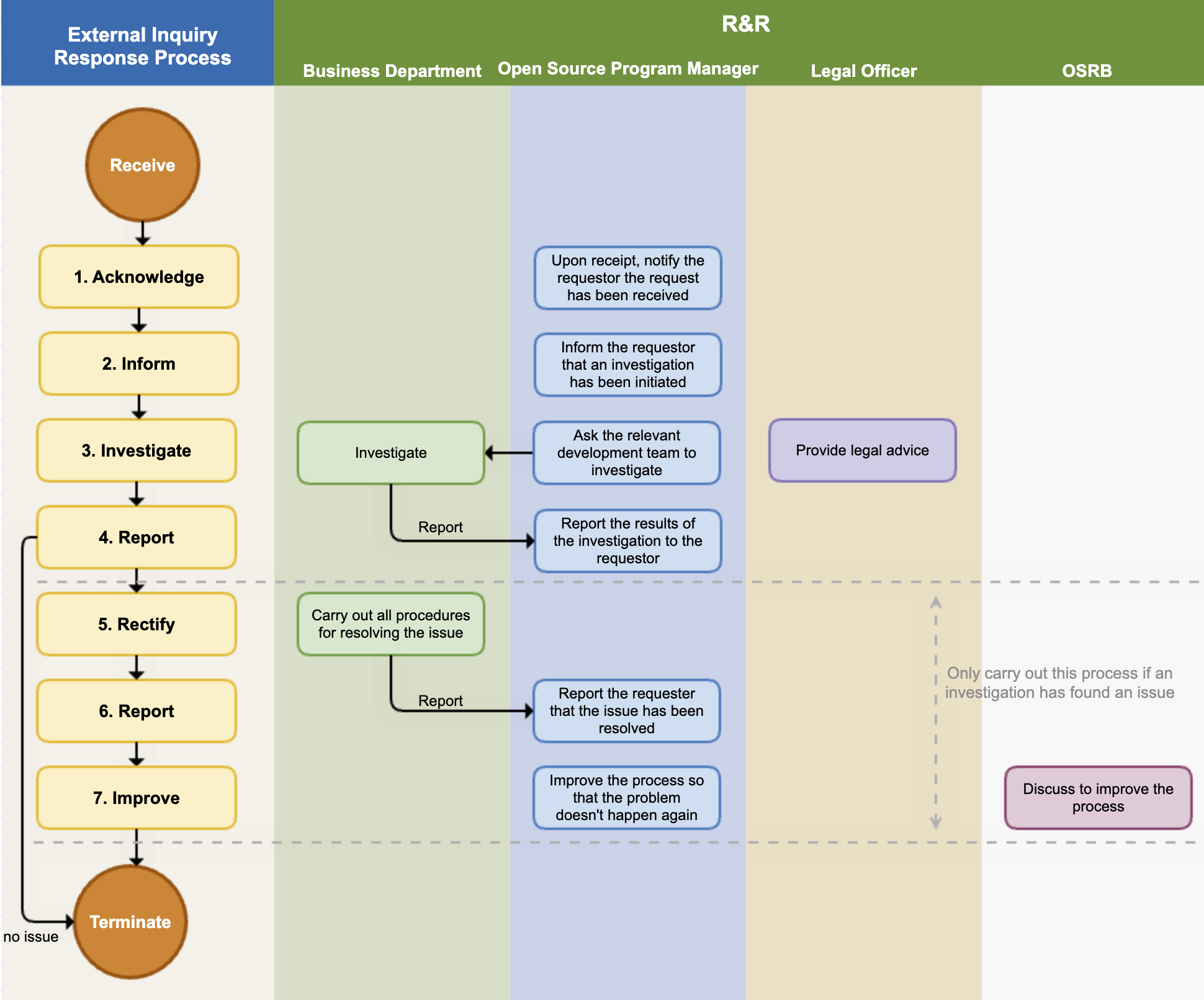
(1) Acknowledge
The open source program manager immediately notifies the requester that the inquiry has been received. At this time, the expected date of action is also notified. If the inquiry is unclear, additional explanation is requested to accurately understand the requester’s intention.
The main contents of the inquiries and requests that require a response are as follows:
- Inquiry about whether open source has been used in a specific product or service
- Request for source code provision under the GPL, LGPL license mentioned in the written agreement
- Explanation and source code disclosure request for open source found in the product but not specified in the open source notice
- Request for provision of missing files and build methods in the source code disclosed due to obligations such as GPL, LGPL
- Request for copyright notice
The open source program manager creates a Jira Issue for the received request and records all the response situations in detail.
(2) Inform
The open source program manager informs the requester that they are conducting open source compliance faithfully and that they are investigating the requester’s inquiry. It is good to notify whenever the internal investigation progress is updated.
(3) Investigate
The open source program manager conducts an internal investigation on the request. They check whether the compliance process has been appropriately performed for the version of the product in question through the BOM and documented review history. If necessary, they request advice from the legal manager.
If it is a matter that needs to be confirmed by a specific business department, the open source program manager requests an investigation from the business department. The business department that received the investigation request immediately checks whether there is a problem with the compliance deliverables and reports the results to the open source program manager.
(4) Report
The open source compliance manager completes the internal investigation within the scheduled date of action and notifies the requester of the result.
- If the requester’s inquiry was a misdirected point due to misunderstanding, they notify the requester and end the process without any additional action.
- If there is a problem, they notify the requester of the exact method and timing to fulfill the obligations of the relevant open source license.
(5) Rectify / Notify
If an actual compliance issue is found in the internal investigation, the relevant business department performs all procedures necessary to resolve the compliance issue.
(6) Report
After resolving the issue, they immediately notify the requester and provide the best way to confirm that the issue has been resolved.
(7) Improve
In case of a compliance issue, the case is reviewed through the OSRB meeting, the circumstances of the occurrence of the problem are identified, and the process is improved so that the problem does not recur.
5 - Tools
5.1 - FOSSology
오픈소스 컴플라이언스를 위해 소프트웨어 내에 포함된 오픈소스와 라이선스 정보를 검출하기 위해 소스코드 스캔 도구를 사용할 수 있다.

Linux Foundation의 FOSSology 프로젝트는 이러한 스캔 도구를 개발하고 오픈소스로 공개해 누구나 자유롭게 사용할 수 있게 한 도구이다.
주요 특징
FOSSology는 웹기반의 프로그램으로 사용자는 웹사이트에 로그인하여 개별 파일 혹은 소프트웨어 패키지를 업로드할 수 있다. FOSSology는 업로드된 파일 내에 라이선스 텍스트와 Copyright 정보를 검출한다. 개발자는 사용하고자 하는 오픈소스의 라이선스가 무엇인지, Copyright은 어떻게 되는지에 대한 정보를 확인하고자 할때 FOSSology를 이용하는 것이 좋다. FOSSology는 개발자가 업로드한 오픈소스 패키지 내의 모든 파일을 스캔하여 각 파일 내 라이선스 관련 텍스트와 Copyright 정보를 자동으로 검출하고, 이를 리포트로 생성한다. FOSSology 주요 특징에 대한 자세한 내용은 다음 페이지를 참고할 수 있다. : https://www.fossology.org/features/
설치
기업 내에서 FOSSology를 사용하기 위해서는 사내에 FOSSology 서버를 구축해야 한다. 이를 위해 리눅스 기반의 서버 시스템에 FOSSology를 설치해야 한다. FOSSology는 다음 세 가지 방법으로 설치할 수 있다.
- Docker 사용
- Vagrant와 VirtualBox 사용
- Source build하여 설치
여기서는 가장 간편한 방법인 Docker를 사용하는 방법에 대해 설명한다.
FOSSology는 컨테이너화 된 Docker 이미지를 Docker Hub (https://hub.docker.com/)를 통해 공개하고 있다. : https://hub.docker.com/r/fossology/fossology
Pre-built 된 Docker 이미지는 다음 명령어를 사용하여 실행할 수 있다.
$ docker run -p 8081:80 fossology/fossology
Docker 이미지는 다음 URL과 계정 정보로 사용할 수 있다. : http://[IP_OF_DOCKER_HOST]:8081/repo
- Username : fossy
- Passwd : fossy
설치와 관련한 자세한 내용은 다음 페이지를 참고할 수 있다. : https://github.com/fossology/fossology/blob/master/README.md
테스트 서버
FOSSology를 설치할 수 있는 시스템 구축이 곤란한 상황이라면, FOSSology Project에서 제공하는 테스트 서버를 이용할 수 있다. FOSSology 프로젝트에서는 테스트를 위한 환경을 제공한다. (테스트 서버는 예고없이 중단될 수 있다.)
사용자는 다음 계정으로 FOSSology 테스트 서버에 접속하여 FOSSology 기능을 시험해볼 수 있다.
테스트 서버 URL: https://fossology.osuosl.org/
- Username: fossy
- Password: fossy

Basic Workflow
FOSSology의 기본 사용 절차는 다음과 같다.
- 사용하고자 하는 오픈소스의 라이선스와 Copyright 정보를 확인하기 위해 오픈소스의 소스 코드를 하나의 파일로 압축하여 FOSSology에 업로드한다.
- 이를 위해 메뉴 > Upload > From File을 선택합니다.
- 업로드할 파일을 선택하고 Upload 버튼을 클릭한다.
- 업로드가 완료되면 Job Agent에 의해 자동으로 분석을 수행한다.
- 메뉴 > Jobs > My Recent Jobs에서 분석 중인 Status를 확인할 수 있다.
- 분석이 완료되면 메뉴 > Browse에서 분석 결과를 확인할 수 있다.
- 개별 파일을 선택하면 FOSSology가 검출한 라이선스 관련 텍스트가 무엇인지 확인할 수 있다.
- 메뉴 > Browser > 파일 혹은 디렉터리를 선택 > Copyright/Email/Url/Author에서는 FOSSology가 검출한 Copyright/Email/Url/Author 정보를 보여다.
사용자는 FOSSology는 이렇게 분석한 결과가 유효한지 여부에 대해 확인 후 잘못 검출된 항목에 대해서는 분석 결과에서 제외시키는 작업을 할 수 있다. FOSSology는 이를 Clearing 과정이라고 설명하며, 자세한 사항은 다음 페이지를 참고할 수 있다. : https://www.fossology.org/get-started/basic-workflow/
위와 같은 방법으로 사용하고자 하는 오픈소스의 라이선스는 무엇인지, Copyright 정보는 어떻게 되는지를 간단히 확인할 수 있다.
5.2 - SW360
(Updated on August 29, 2023.)
오픈소스를 포함하는 제품을 개발하고 배포하는 기업이라면 각 제품과 릴리스 버전마다 사용한 오픈소스의 버전, 라이선스 등의 정보를 수집하고 추적해야 한다. 이를 통해 기업은 올바른 오픈소스 컴플라이언스 활동을 수행할 수 있다.
특히, NVD (https://nvd.nist.gov/vuln)에서 특정 오픈소스 버전에 보안 취약점이 보고 되었을때, 해당 버전을 사용하고 있는 제품이 무엇인지 추적을 할 수 없다면, 그 기업은 어느 제품에 보안 패치를 적용해야 할 지 알 수 없는 상황에 처하게 되고, 그 기업의 제품들은 보안취약점에 그대로 노출이 될 수 밖에 없다.
이렇듯, 오픈소스 정보를 추적하는 활동은 꼭 필요하다. 기업들은 이를 위해 자체 시스템을 구축하거나, 상용 서비스를 구매하여 사용하기도 한다. SW360은 Eclipse 재단에서 후원하는 오픈소스로서 소프트웨어 BOM에 대한 정보를 수집 및 추적하기 위한 웹 애플리케이션 및 저장소를 제공한다.

주요 특징
SW360은 웹 기반의 UI를 제공하며 주요 기능은 다음과 같다.
- 제품에 사용된 컴포넌트 추적
- 보안 취약점 평가
- 라이선스 의무 관리
- 고지문 등 법적 문서 생성
설치
SW360은 다음과 같이 구성된다.
- Frontend : Liferay-(Tomcat-)based portal application
- Backend : Tomcat-based thrift service
- Database : CouchDB
Project 구조와 설치를 위해 요구되는 소프트웨어 등 자세한 내용은 README의 Required software 부분에서 확인할 수 있다. : https://github.com/eclipse-sw360/sw360
SW360은 다음 두 가지의 설치 방법을 제공한다. 사용자는 이 중 하나를 선택하여 설치할 수 있다.
- Docker를 통해 Deploy 할 수 있다. : https://github.com/eclipse-sw360/sw360/blob/main/README_DOCKER.md
- SW360의 구성요소를 개별적으로 설치할 수 있다. : https://github.com/eclipse/sw360
- Vagrant (https://www.vagrantup.com/) 기반 설치 : Vagrant는 가상화 인스턴스를 관리하는 도구로서 sw360vagrant에서는 SW360을 한 번에 Deploy 하기 위한 환경을 제공한다. : https://github.com/sw360/sw360vagrant
- Vagrant 기반 설치 가이드는 여기에서 확인할 수 있다. (단, 가이드 작성 시점과 현재 코드가 상이하여 정상동작하지 않을 가능성이 있습니다.)
이 가이드에서는 Docker로 Deploy하는 방법을 소개한다. 자세한 사항은 README를 참고한다. : https://github.com/eclipse-sw360/sw360/blob/main/README_DOCKER.md
1. 코드 다운로드
Docker Image 빌드를 위해 코드를 다운로드 한다. 테스트가 완료된 코드는 여기서 받을 수 있다. : https://github.com/haksungjang/sw360/tree/docker_build
git clone -b docker_build https://github.com/haksungjang/sw360.git
2. 빌드
먼저 Docker를 설치한다. (기업 개발자가 사용하려면 유료 구매가 필요할 수 있음에 주의하세요.)
아래와 같이 docker_build.sh를 실행하여 빌드한다.
cd sw360
./docker_build.sh
정상적으로 빌드가 완료되면 아래와 같이 생성된 이미지를 확인할 수 있다.
docker image ls
REPOSITORY TAG IMAGE ID CREATED SIZE
eclipse-sw360/sw360 18-development ab0fd848bf80 8 minutes ago 2.95GB
eclipse-sw360/sw360 latest ab0fd848bf80 8 minutes ago 2.95GB
ghcr.io/eclipse-sw360/sw360 18-development ab0fd848bf80 8 minutes ago 2.95GB
ghcr.io/eclipse-sw360/sw360 latest ab0fd848bf80 8 minutes ago 2.95GB
eclipse-sw360/binaries 18-development aa7debf0a1fc 8 minutes ago 347MB
eclipse-sw360/binaries latest aa7debf0a1fc 8 minutes ago 347MB
ghcr.io/eclipse-sw360/binaries 18-development aa7debf0a1fc 8 minutes ago 347MB
ghcr.io/eclipse-sw360/binaries latest aa7debf0a1fc 8 minutes ago 347MB
eclipse-sw360/base 18-development e5147733fc88 37 minutes ago 1.52GB
eclipse-sw360/base latest e5147733fc88 37 minutes ago 1.52GB
ghcr.io/eclipse-sw360/base 18-development e5147733fc88 37 minutes ago 1.52GB
ghcr.io/eclipse-sw360/base latest e5147733fc88 37 minutes ago 1.52GB
ghcr.io/eclipse-sw360/thrift 0.18.1 0012d7998058 4 weeks ago 152MB
ghcr.io/eclipse-sw360/thrift latest 0012d7998058 4 weeks ago 152MB
eclipse-sw360/thrift 0.18.1 0012d7998058 4 weeks ago 152MB
eclipse-sw360/thrift latest 0012d7998058 4 weeks ago 152MB
3. 실행
docker-compose up 명령으로 생성된 이미지를 실행한다.
docker-compose up
정상적으로 실행이 완료되면 아래와 같이 세개의 container가 실행된 것을 볼 수 있다.
docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
4299fd39010c eclipse-sw360/sw360 "/app/entry_point.sh" 3 minutes ago Up 3 minutes 0.0.0.0:8080->8080/tcp, 0.0.0.0:11311->11311/tcp sw360
13fd5696b140 postgres:14 "docker-entrypoint.s…" 3 minutes ago Up 3 minutes (healthy) 0.0.0.0:5438->5432/tcp sw360-postgresdb-1
7bb70f2daaf4 couchdb "tini -- /docker-ent…" 3 minutes ago Up 3 minutes (healthy) 4369/tcp, 9100/tcp, 0.0.0.0:5984->5984/tcp sw360-couchdb-1
이 상태에서 http://localhost:8080/로 접근하면 다음과 같은 화면에 진입한다.

설정
SW360을 정상적으로 설치한 후에는 아래의 절차대로 초기 설정이 필요하다. 자세한 내용은 여기에서 확인할 수 있다. : SW360 Initial Setup Configuration
1. User, Login 설정
설정을 위해 다음 계정으로 로그인한다.
- id : setup@sw360.org
- pw : sw360fossy
로그인을 하면 아래와 같이 Not Found라는 표시가 나타나게 된다.

화면 우상단의 아이템 아이콘(큐브 모양)을 클릭하고 Control Panel 탭을 선택한다.

SECURITY > Password Policies > Default Password Policy > PASSWORD CHANGES > Change Requried를 활성화한다.

그리고, 다시 Control Panel탭에서 CONFIGURATION > Instance Settings을 선택한다. 그러면, PLATFORM메뉴를 볼 수 있다.

거기서 Users를 선택한다. 그리고, Default User Associations 메뉴로 진입하고, Apply to Existing Users를 체크한다. 그리고 Save한다.

이번에는 Instance Settings > PLATFORM에서 User Authentication를 선택한다. General로 진입하여 모든 항목을 Uncheck한다. (관리 목적상 필요한 항목은 Check하여 활성화할 수 있다.) 그리고 Save한다.

끝으로, jquery와 font awesome을 활성화시켜야 한다. 이를 위해 Control Panel 탭에서 CONFIGURATION > System Settings으로 진입하면 PLATFORM 하위에 Third Party를 볼 수 있다.

Third Party에 진입하여 JQuery와 Font Awesome을 각각 Enable시킨다.


브라우저를 새로 실행하면 변경 사항이 적용된다.
2. LAR 파일 import
SW360 설정을 위해서는 *.lar 파일들을 import해야 한다. 이를 설정하기 위해서는 메뉴로 진입해야 하는데, 메뉴 버튼은 화면 좌측 상단에 있다.

메뉴에서 Publishing > Import에 진입한다.

우측의 + 버튼을 눌러 LAR 파일을 업로드 할 수 있는데, LAR 파일은 SW360 소스 파일 내 frontend/configuration 폴더 하위에 있다. (예: https://github.com/haksungjang/sw360/tree/docker_build/frontend/configuration)
먼저, Public_Pages_7_4_3_18_GA18.lar 파일을 업로드하고 Continue 버튼을 누른다.

File Summary 화면에서 업로드된 LAR 파일 세부 내용을 볼 수 있다.

제일 아래의 AUTHORSHIP OF THE CONTENT를 Use the Current User as Author로 변경하고 Import 버튼을 누른다.

그러면 Import가 성공적으로 완료된 걸 볼 수 있다.

이와 유사하게 Private_Pages_7_4_3_18_GA18.lar 파일을 Import한다. File Summary 화면에서 아래와 같이 PAGES > Private Pages로 변경한다.

그리고, PERMISSIONS, UPDATE DATA, AUTHORSHIP OF THE CONTENT 항목을 각각 아래 이미지와 같이 선택하고, Import버튼을 눌러 Import를 수행한다.

여기까지 수행을 마친 후 메뉴 상단의 Home 버튼을 누른다.

그럼 아래와 같이 Welcome to SW360! 화면에 진입한다.

Start 버튼을 눌러 SW360 첫 화면에 진입할 수 있다. (모든 항목이 비어있다.)

3. User Account 설정 (테스트용)
SW360 메뉴에서 Admin > User를 선택한다.

화면 하단의 UPLOAD USERS 메뉴에서 테스트를 위한 User 리스트를 업로드 한다. (테스트를 위한 User 리스트는 여기에서 다운 받을 수 있다. : test_users_with_passwords_12345.csv )

그러면 다음과 같이 9개의 User 리스트가 업로드 된 것을 볼 수 있다.

여기서 보이는 User 리스트 중 하나인 user@@sw360.org 계정으로 다시 로그인을 시도한다. Password는 12345이다.
Basic Workflow
1. License 등록
SW360을 처음 설치하면 먼저 자주 사용하는 오픈소스 라이선스 들을 등록해야 한다. 라이선스 다음과 같은 정보를 포함한다.
- Full Name
- Short Name
- License Type
- GPL-2.0 Compatibility (예: yes, no)
- License Text
메뉴 > Licenses > Add License를 선택하면 다음과 같이 Create License 화면으로 진입한다.
이와 같이 라이선스를 하나씩 수동으로 등록하는 일은 상당히 수고스러울 수 있는데, 다행히 SW360은 SPDX License List를 한 번에 Import 하는 기능을 제공한다. 메뉴 > Admin < Import SPDX Information을 클릭한다.
그러면, 곧 SPDX License List가 자동으로 등록됩니다. 메뉴 > Licenses에서 338개의 License가 등록된 것을 확인할 수 있다.
2. Component 및 Release 등록
SW360에서 Component는 하나의 소프트웨어 단위이다. 여기에는 다양한 형태의 소프트웨어가 해당할 수 있으며, 그 예는 다음과 같다.
- 오픈소스 소프트웨어
- 라이브러리
- 3rd party 소프트웨어
Component는 다음과 같은 정보를 포함한다.
- Component Name
- Main Licenses
- Categories (예: Library, Cloud, Mobile, …)
- Component Type (예: OSS, Internal, InnerSource, Service, Freeware)
- Default Vendor
- Homepage URL
Release는 Component에서 하나의 Version을 가리키는 단위이다. 따라서 하나의 Component는 여러 개의 Release를 가질 수 있다. Release는 하나의 Component 하위에 생성되어 관리된다.
Release는 다음과 같은 정보들을 포함한다.
- Component Name
- Version
- License
- Download URL
- CPE ID (예: cpe:2.3:a:apache:maven:3.0.4)
예를 들어, zlib-1.2.8을 등록해야 한다면, 먼저 Component에 zlib을 먼저 등록한 후, Release에 zlib 1.2.8을 등록한다. Menu > Components > Add Component를 선택하면 Create Component 화면으로 진입하여 zlib에 대한 정보를 등록할 수 있다.
Component를 생성하면, Components > Releases > Add Release에서 zlib-1.2.8 version에 대한 정보를 등록할 수 있다.
하나의 zlib이라는 Component에 1.2.8과 1.2.11 version을 각각의 Release로 등록하였을 때, Release Overview 화면에서 다음과 같이 2개의 Release가 존재하는 것을 볼 수 있다.
SW360은 다수의 Component 정보를 Import 시키기 위한 기능을 제공한다. 메뉴 > Admin > Import / Export에 CSV template에 등록을 원하는 Component 정보를 입력 후 Import 할 수 있다.
단, 이 기능은 2020년 2월 기준 아직 안정적으로 동작하지 않을 수 있다.
3. Project 생성
Project는 하나의 제품을 가리킨다. 사업 유형에 따라 제품일수도 있고, 서비스 혹은 소프트웨어 일수도 있다. Project에는 제품에 사용된 Component/Release를 등록하여 관리한다.
Project 생성 시에는 다음과 같은 정보를 등록한다.
- Project Name
- Version
- Project type (예: Product, Customer Project, Service, Internal Project, InnerSource)
메뉴 > Projects > Add Project를 통해 Project를 생성할 수 있다.
Project를 생성하고 나면, 포함하는 Release나 하위 Project를 등록한다. 메뉴 > Projects에서 해당 Project를 선택하면 “Linked Releases and Projects”에서 Linked Projects와 Linked Releases를 등록할 수 있다.
다음은 SuperCalc라는 Project에 OpenSSL 1.0.1과 zlib 1.2.8을 Linked Releases로 등록한 이후의 화면이다.
4. 보안 취약점 관리
SW360은 등록된 Release에 대해 보안 취약점이 있는지 자동으로 확인할 수 있다. 이를 위해 SW360은 CVE 정보를 주기적으로 수집하도록 스케쥴링하는 기능을 제공한다. 메뉴 > Admin > Schedule 에서 CVE SEARCH 정보를 24시간마다 수집하도록 스케쥴링을 설정할 수 있다.
이렇게 스케쥴링을 설정하면 SW360은 정해진 시간에 CVE Search 사이트(https://cve.circl.lu/)에서 CVE 정보를 수집한다. 수집한 CVE 정보는 메뉴 > Vulnerabilities에서 확인할 수 있다.
이렇게 Vulnerabilities 정보가 수집된 이후에는 생성한 Project에 보안 취약점이 있는지 조회할 수 있다. 위에서 생성한 SuperCalc Project에서는 85개의 보안 취약점이 보고된 것을 확인할 수 있다.
이와 같은 방법으로 기업에서 개발/배포하는 소프트웨어를 SW360에 등록하여 관리한다면, 오픈소스 컴플라이언스뿐만 아니라 보안 취약점에 대해서도 리스크를 최소화할 수 있는 형태로 관리가 가능하다.
또한 SW360은 위와 같은 Web Interface 뿐만 아니라 대부분의 기능을 REST API로 제공하여서 FOSSology 등의 다른 도구와의 연동이 가능하다. : https://github.com/eclipse/sw360/wiki/Dev-REST-API
즉, 소스 코드 스캐닝 도구의 분석 결과를 SW360에 Import 시키는 등의 방법으로 DevOps에 Integration 시켜서 Project, Release 등록을 자동화시켜서 관리한다면 효율성이 크게 증가될 것이다.
6 - [out of date] Open Source Governance for Enterprises
OpenChain ISO/IEC 5230 is the International Standard for open source license compliance. It defines key requirements that companies distributing software must comply with in order to use open source properly. Here, ISO/IEC 5230 is briefly introduced and how companies can build open source governance based on it.
This content is the result of a study conducted by the Korea Copyright Commission open source expert community in 2021.
Author : Haksung Jang (haksung@sktelecom.com) / CC BY 4.0
References
This guide has referenced the following resources:
6.1 - 1. What is ISO/IEC 5230
You can find everything about ISO/IEC 5230 on the OpenChain project website. : https://www.openchainproject.org/

6.2 - 2. Essential elements
Essential elements of an open source program
You need the following components to build an effective open source governance for your comapny.
Among the above elements, in order to establish an open source governance suitable for all items required by ISO/IEC 5230, a company must have the following five core elements.

6.3 - 3. Team
Identify the roles and the corresponding responsibilities
In order to establish a company’s open source governance, it is necessary to appoint a person in charge of it. It may be called an open source program manager, an open source compliance officer, etc., and this person in charge is responsible for the overall open source compliance of the company.
A person with the following competencies is suitable for this role.
- Understanding and development experience in the open source ecosystem
- Broad understanding of the company’s business
- Passion and communication skills to spread the effective use of open source to members of the company
An open source program manager should be guaranteed to be able to perform the role as full-time as possible.
Global ICT companies are working hard to hire such excellent open source program managers, and you can check various job postings at the following site. : https://github.com/todogroup/job-descriptions
To establish open source governance, you need to define the needs of each role and determine what responsibilities should be assigned. For small businesses, it is possible for an open source program manager to perform all the roles alone. Depending on the size of the enterprise, an infrastructure person who operates open source tools may be required, and the role of a legal person may be required to provide professional legal advice.
In general, the following roles are required to establish a corporate open source governance system.
- Legal
- Infrastructure
- Development culture
- Security
If you do the above, you can prepare the following evidence required by ISO/IEC 5230.
ISO/IEC 5230
- 3.1.2.1 : A documented list of roles with corresponding responsibilities for the different participants in the program.
Self Certify
- 1.c : A documented list of roles with corresponding responsibilities for the different participants in the program.
Define competencies
Once you have defined each role and its responsibilities, you need to figure out what competencies the person performing that role should have. This is because, through this, it is necessary to evaluate whether the person in charge of each role has the capability to perform the role, and if there is not enough, the company must provide the necessary training to him.
If you do this, you can prepare the following evidence required by ISO/IEC 5230.
ISO/IEC 5230
- 3.1.2.2 A document that identifies the competencies for each role.
Self Certify
- 1.d : Have you identified and documented the competencies required for each role?
Identify person or group
The open source program manager, in consultation with the relevant department, designates and documents the person in charge for each role. Of course, for this, it will be necessary to report the goals and directions for establishing an open source compliance system to the top decision makers such as the CEO to receive the necessary support.
Open source-related person and group in charge do not necessarily have to participate in open source work full-time. You can organize a virtual group in the form of an OSRB (Open Source Review Board) and perform the necessary roles.
SK Telecom has formed the OSRB to create open source policies and processes, and prepare countermeasures when issues arise.
If you do this, you can prepare the following evidence required by ISO/IEC 5230.
ISO/IEC 5230
- 3.2.2.1 Document with name of persons, group or function in program role(s) identified.
Self Certify
- 2.d : Have you documented the persons, group or function supporting the Program role(s) identified?
The table below is a sample representative that specifies the roles of open source-related organizations and people in charge, and the required competencies. You can refer to this and form an open source organization and document it.
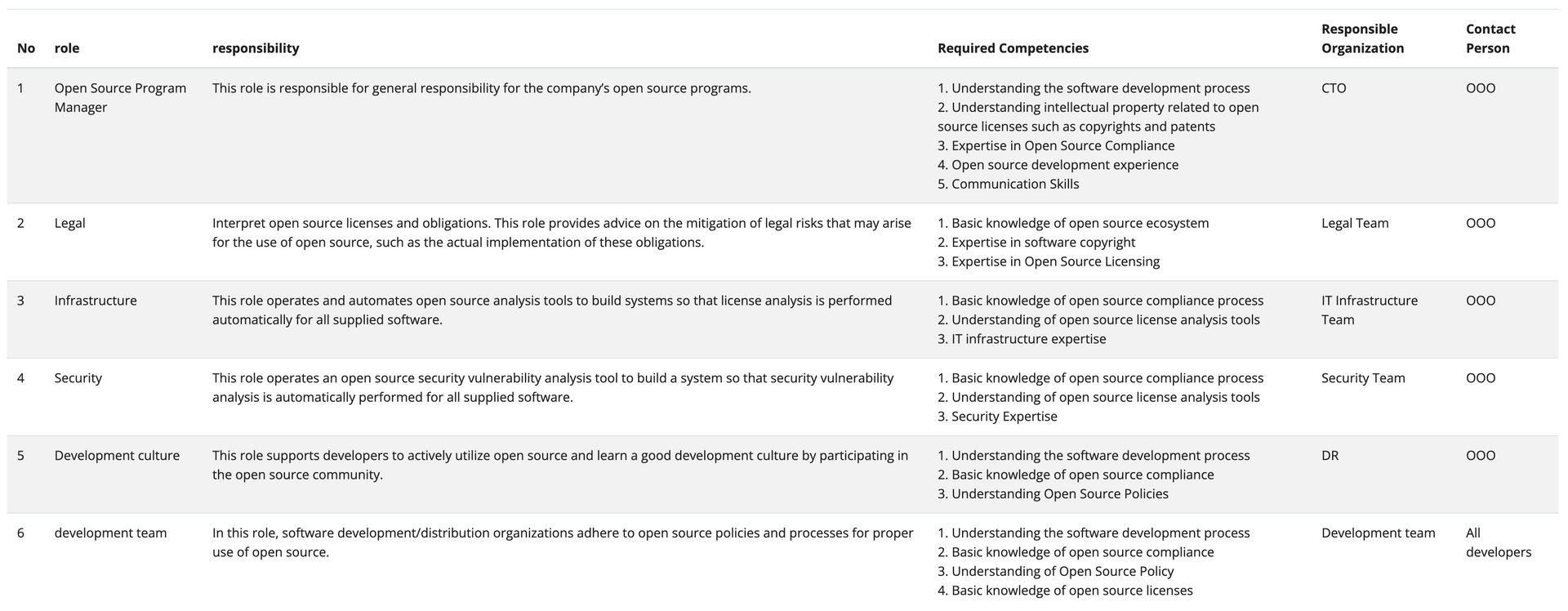
This can also be found on this page. : appendix-1-list-of-persons-in-charge
If you organize in this way, you will now meet the following three requirements among the requirements of ISO/IEC 5230.
6.4 - 4. Policy
Document open source policy
A company should establish, document, and disseminate an open source policy composed of principles for a company to properly use open source in software development, service, and distribution.
Common open source policies include:
- Principles for creating and distributing software products and services using open source
- Principles for contributing to the external open source community
- Principles for releasing open source
The following pages provide sample open source policy documents that meet the requirements of ISO/IEC 5230. : “Appendix 1. Open Source Poicy (Sample)”
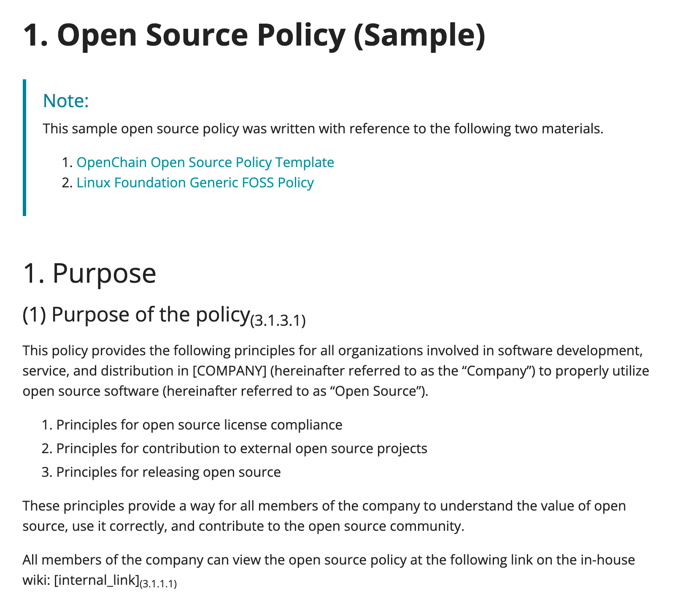
Each company can use this sample policy by modifying it according to the company’s business strategy and environment.
If you do this, you can prepare the following evidence required by ISO/IEC 5230.
ISO/IEC 5230
- 3.1.1.1 A documented open source policy.
Self Certify
- 1.a : Do you have a documented policy that governs open source license compliance of the Supplied Software distribution (e.g., via training, internal wiki, or other practical communication method)?
Define scope
An open source program does not necessarily apply to the entire organization. The scope can be specified differently depending on the characteristics of each organization and product within the company. Different open source programs can be applied to different organizations and products. Similarly, organizations that do not distribute software at all may be excluded from the scope of the open source program. A company can clearly define the scope and limits of the application of an open source program in consideration of the characteristics of the organization and product, and specify it in the open source policy.
As a company’s organization and its products and services change with the business environment, it may be necessary to determine or modify the scope of the program. A company should prepare a procedure to manage it as in the following example.
- When starting a new project, the open source program manager determines whether the project falls within the scope of the program’s coverage.
- If it is determined that the project is not included, a proposal to include the project in the scope of application is submitted to the OSRB.
- If accepted by OSRB, the scope of the open source program will be modified accordingly.
- Other than that, if the open source program manager determines that it is necessary to review the program scope, it may start the program scope review according to the same process.
The following examples can be included in the open source policy.
2. Scope
This policy applies to the following three parts:
1. Applies to [all products provided or distributed by the company externally].
However, the open source only for internal use is not included in the scope of
this policy.
2. Applied when contributing to external open source projects.
3. Applied when releasing internal code as open source.
The scope can be changed according to the business environment of the company,
and the procedure for this is as follows.
1. If the open source program manager determines that it is necessary to change
the scope of policy according to changes in the company's business environment,
such as a new business or reorganization, submit a proposal for this to the OSRB.
2. OSRB approves proposals for scope changes at the appropriate level.
3. OSRB modifies the open source policy to change the scope of the policy.
If you do this, you can prepare the following evidence required by ISO/IEC 5230.
ISO/IEC 5230
- 3.1.4.1 A written statement that clearly defines the scope and limits of the program.
Self Certify
- 1.g : Do you have a process for determining the scope of your Program?
- 1.h : Do you have a written statement that clearly defines the scope and limits of the Program?
Respond to external inquiries
For products or services developed using open source, customers and open source copyright holders may raise open source related inquiries, requests and claims to companies. The main contents of external inquiries and requests are as follows.
- Ask if open source is used for certain products and services
- Request to provide source code under the GPL, LGPL license mentioned in the Written Offer
- A request for a description of the open source found in the product and disclosure of the source code, although not specified in the open source notice
- Request to provide missing files and build methods in the source code published under GPL, LGPL, etc.
- Request for copyright notice
You should designate a contact person to handle these external inquiries. This is usually done by an open source program manager.
In addition, even if an external open source developer wants to contact a company representative to discuss an issue related to a specific company’s open source compliance, they cannot find a way to contact them and eventually file a legal claim. In order to prevent this, you must always disclose publicly how to contact the company from outside to make inquiries and requests related to open source.
To disclose your contact information so that external open source related inquiries can be received, (1) publicly disclosed the email address of the company’s open source program manager, or (2) the Linux Foundation’s [Open Compliance Directory] (https://compliance.linuxfoundation. org/references/open-compliance-directory/).
It is also a good idea to disclose the representative email address of the company open source program office in the open source notice that accompanies the product and service.
These contents can be included in the open source policy as in the example below.
Respond to external inquiries
(1) Responsibility for responding to external inquiries
The open source program manager is responsible for responding
to inquiries and requests for open source compliance from
outside.<sub>(3.2.1.2)</sub>
* The open source program manager may assign all or part of
the handling of inquiries to appropriate personnel within the
company. If necessary, contact the legal team to deal with it.
* Anyone who receives an inquiry about open source compliance
from outside will notify the open source program manager so
that a prompt response can be made.
(2) Disclosure of contact information
The open source program manager publicly provides the contact
information of the person in charge so that external inquiries
and requests related to open source can be submitted to the
company.<sub>(3.2.1.1)</sub>
* Include the email address of the person in charge in the open
source notice.
* Register your contact in the Linux Foundation's Open Compliance
Directory.
(3) External Inquiry Response Procedure
If you respond quickly and accurately to open source compliance
inquiries from outside, you can significantly reduce the risk of
going to a lawsuit. To this end, in order to respond to external
open source compliance inquiries, you should follow the external
inquiry response process defined in the company's open source
compliance process.<sub>(3.2.1.2)</sub>
If you do this, you can prepare the following evidence required by ISO/IEC 5230.
ISO/IEC 5230
- 3.2.1.1 Publicly visible method that allows any third party to make an open source license compliance inquiry (e.g., via a published contact email address, or the Linux Foundation’s Open Compliance Directory).
Self Certify
- 2.a : Do you have a documented procedure that assigns responsibility for receiving and responding to open source compliance inquiries?
- 2.b : Is the Open Source Liaison function publicly identified (e.g. via an email address and/or the Linux Foundation’s Open Compliance Directory)?
Provide staff and funding
You must provide sufficient resources for open source programs to function properly. Staff for each role in the program should be appropriately assigned, and sufficient funding and working hours should be ensured. If there is a shortage, there should be a procedure to make up for it. The following example sentences can be added to the open source policy document.
4. Roles, Responsibilities and Competencies
The head of the organization responsible for each role designates
a person in charge within the organization, and allocates appropriate
time and budget for the person in charge to fulfill the role.
* The person in charge of each role should raise an issue with
the open source program manager if appropriate support is not
provided while performing his/her role.
* The open source program manager discusses problem solving with
the head of the organization. If not properly resolved, the open
source program manager may request the OSRB to resolve the issue.
* OSRB shares the problem with the head of the higher level organization
and asks for a solution.
If you do this, you can prepare the following evidence required by ISO/IEC 5230.
ISO/IEC 5230
- 3.2.2.2 The identified program roles have been properly staffed and adequate funding provided.
Self Certify
- 2.e : Have the identified Program roles been properly staffed and has adequate funding provided?
Identify Legal Expertise
You should provide a way for the person in charge of each role to seek legal advice when a legal review is needed to resolve an open source compliance issue.
The legal team within the company provides legal advice first, and if the issue is complex, you can seek advice from an external law firm with an open source lawyer. An example of an open source policy for this is as follows.
4. Roles, Responsibilities and Competencies
(2) Open Source Program Manager
* Provides a way to request legal advice on open source.
If you do this, you can prepare the following evidence required by ISO/IEC 5230.
ISO/IEC 5230
- 3.2.2.3 Identification of legal expertise available to address open source license compliance matters which could be internal or external.
Self Certify
- 2.f : Is legal expertise pertaining to internal and external open source compliance identified?
For reference, the OpenChain project provides a list of global law firms that provide open source-related advice through partner programs. : https://www.openchainproject.org/partners
Assigns internal responsibilities
There should be a process for assigning internal responsibilities for open source compliance. This is the role of an open source program manager. The open source program manager must identify the issues and assign them appropriately to the person in charge of each role. To do this, you should include this in your open source policy document as follows:
4. Roles, Responsibilities and Competencies
(2) Open Source Program Manager
The open source program manager is responsible for the overall
responsibility for the company's open source programs.
To ensure open source compliance of products and services using
open source, open source program manager is responsible for:
- Define the roles required for open source compliance, and
designate a responsible person and group in charge of each
role. Consult with OSRB if necessary.
If you do this, you can prepare the following evidence required by ISO/IEC 5230.
ISO/IEC 5230
- 3.2.2.4 A documented procedure that assigns internal responsibilities for open source compliance.
Self Certify
- 2.g : Do you have a documented procedure assigning internal responsibilities for Open Source compliance?
Handle non-compliant cases
Businesses should document procedures for promptly reviewing and responding to non-compliance cases. Refer to the following examples and include them in your open source policy.
6. Use open source
(5) Compliance Issue Remediation Procedure
Should a non-compliance issue be raised, the Open Source Program Manager
responds promptly by performing the following procedures.
1. Acknowledge receipt of the query and state a reasonable time for resolution;
2. Determine whether the query discloses a genuine issue or not
(and if not, respond to the querier accordingly);
3. If the issue is genuine, apply to prioritise, and determine the appropriate response.
4. Carry out response and, where necessary, improve open source compliance processes.
5. Document the above using Jira Tracker.
If you do this, you can prepare the following evidence required by ISO/IEC 5230.
ISO/IEC 5230
- 3.2.2.5 A documented procedure for handling the review and remediation of non-compliant cases.
Self Certify
- 2.7 : Do you have a documented procedure for handling review and remediation of non-compliant cases?
Open Source Contribution Policy
Global IT companies value not only the use of open source to make products and services, but also the strategic value that can be created by contributing to open source projects. However, if you contribute without a sufficient understanding and strategy for the open source project ecosystem and how the community operates, unexpected legal risks may arise and the company’s reputation may be damaged. Therefore, it is important for companies to create strategies and policies for participation and contribution to open source projects.
The following pages provide sample open source contribution policy documents. : 7. Open Source Contribution
If you do this, you can prepare the following evidence required by ISO/IEC 5230.
ISO/IEC 5230
- 3.5.1.1 A documented open source contribution policy
Self Certify
- 5.a : Do you have a policy that governs contributions to open source projects on behalf of the organization?
If you even establish an open source policy that includes the above, the following green items among the ISO/IEC 5230 requirements will be satisfied.
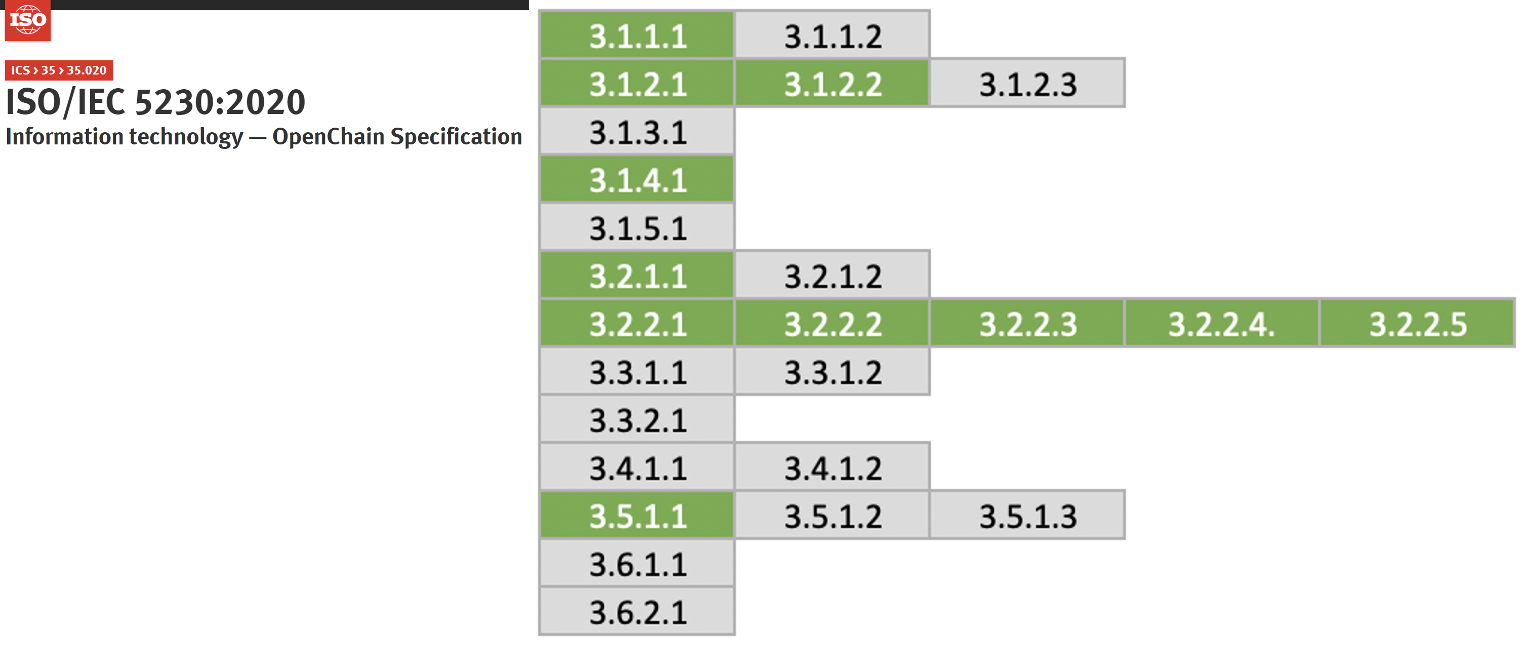
6.5 - 5. Process
A process is an actionable procedure that enables a company to comply with open source policies during software development/distribution. Simply put, the open source compliance process is an activity to comply with the obligations required by each license for the open source used while developing and distributing software, and it generates artifacts such as open source notices and source code to be disclosed.

If the open source compliance process is subdivided and schematized, it is shown in the figure below.
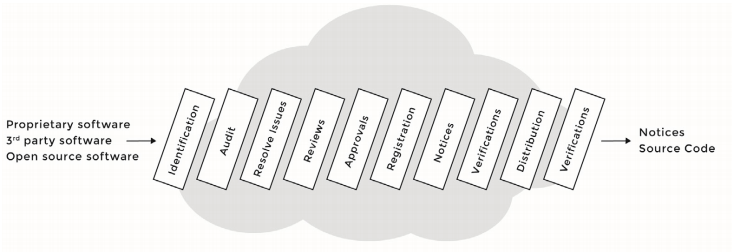
The image below is a sample open source compliance process that companies can commonly use.
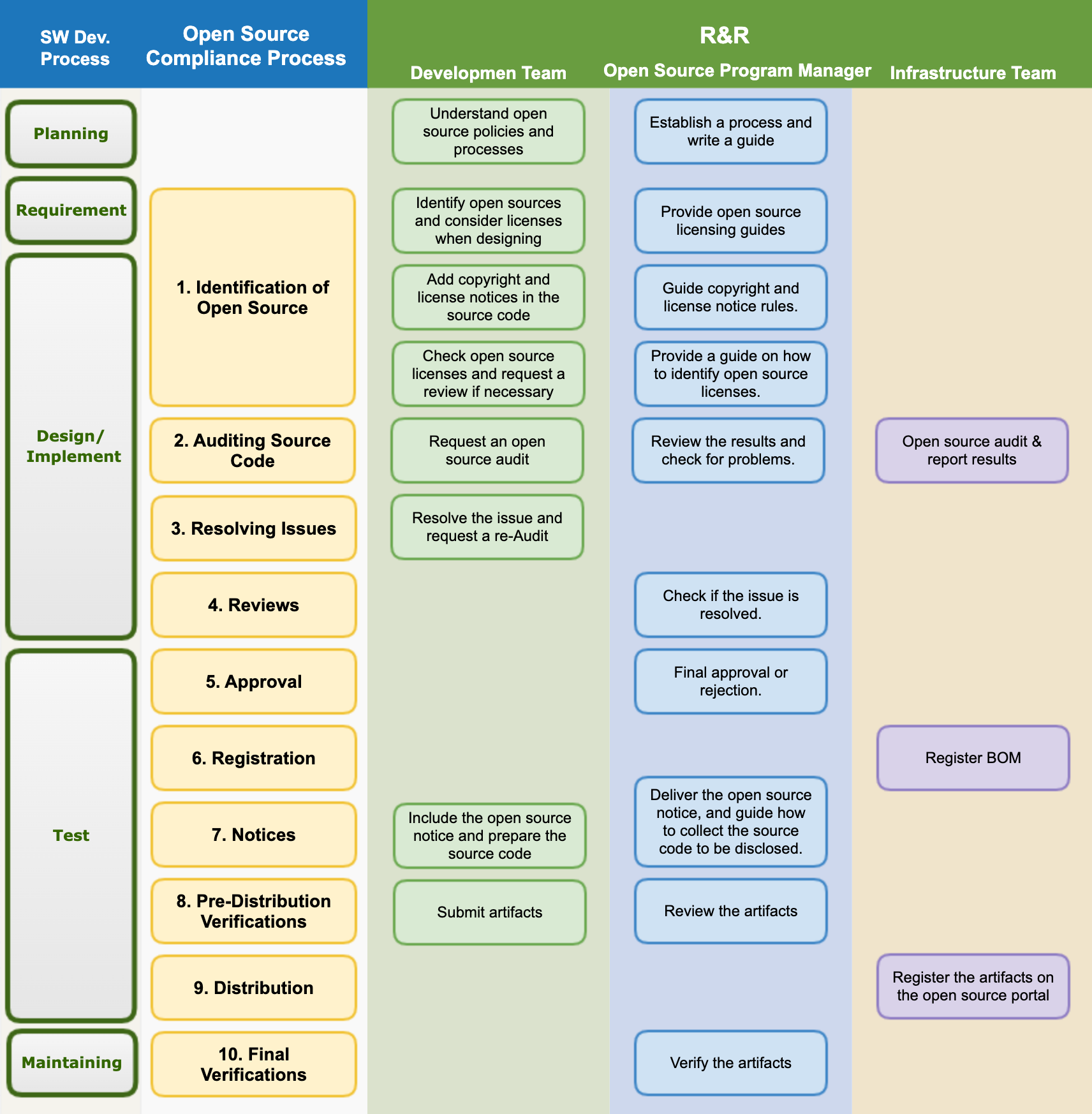
You can refer to the next page for more details on this. : 2. Open Source Compliance Process (Sample)
This chapter describes the elements that an open source compliance process should include.
Identify and audit
In order to determine whether an open source can be used, it is necessary to first identify the license of the open source to be used and check the obligations required by the license. You should review and record whether you used open source, what the licenses are, and what obligations each license gives you. An example of the procedure for this is as follows.
- The development team makes a preliminary assessment of the license based on the open source policy.
- In case of any doubt, contact the open source program manager, and if necessary, the open source program manager refers the question to external legal experts.
- The outcome of any determination, and associated rationale (whether internal or external) is recorded.
The Identification of Open Source, Auditing Source Code, Resolving Issues, Reviews, and Approval steps are an example of a documented process for reviewing and documenting the obligations, restrictions and rights imposed by each identified license.
If you prepare such a procedure, you can prepare the following evidence required by ISO/IEC 5230.
ISO/IEC 5230
- 3.1.5.1 A documented procedure to review and document the obligations, restrictions and rights granted by each identified license.
Self Certify
- 1.i : Do you have a process for reviewing open source license obligations, restrictions and rights?
In the open source identification and audit phase, you use a code scan tool to inspect the source code. For details on this, refer to “6. Tool”.
Create Bill of Materials
The most basic of open source compliance activities is to determine open source included in the supplied software. It is necessary to establish a process for creating and managing a Bill of Materials (BOM) containing the information by identifying the open source included in the supplied software and identified license. This is because it is necessary to know which open source is included in each version of the supplied software so that when distributing the software, you can comply with the obligations required by the identified license of each open source.
All open source must be reviewed and approved prior to integration into the supplied software. It should be reviewed in advance whether it can meet license requirements as well as the function and quality of open source. For this, a review request → review → approval process is required.
Appendix 2. Open Source Compliance Process (Sample) explains all the processes for open source compliance. BOM is created and managed through the process from 1. Identification of Open Source to 6. Registration.
The tool for managing the open source BOM is described in detail in “6. Tool”.
In addition, all processes and results of such an open source compliance process should be documented. Rather than using e-mail, it is better to use an issue tracking system such as [Jira] (https://www.atlassian.com/software/jira) and [Bugzilla] (https://www.bugzilla.org/) to effectively document this process.
If you prepare such a procedure, you can prepare the following evidence required by ISO/IEC 5230.
ISO/IEC 5230
- 3.3.1.1 A documented procedure for identifying, tracking, reviewing, approving, and archiving information about the collection of open source components from which the supplied software is comprised.
Self Certify
- 3.a : Do you have a documented procedure for identifying, tracking and archiving information about the collection of open source components from which a Supplied Software release is comprised?
Create Artifacts
As mentioned above, the most basic of open source compliance activities is to determine the open source included in the supplied software. This is to properly meet the open source license requirements, which are the core of open source compliance. In other words, a process for generating a set of compliance artifacts for open source included in the supplied software should be established.
Compliance artifacts are divided into two main categories.
Open Source Notice: A document to provide full open source license and copyright information
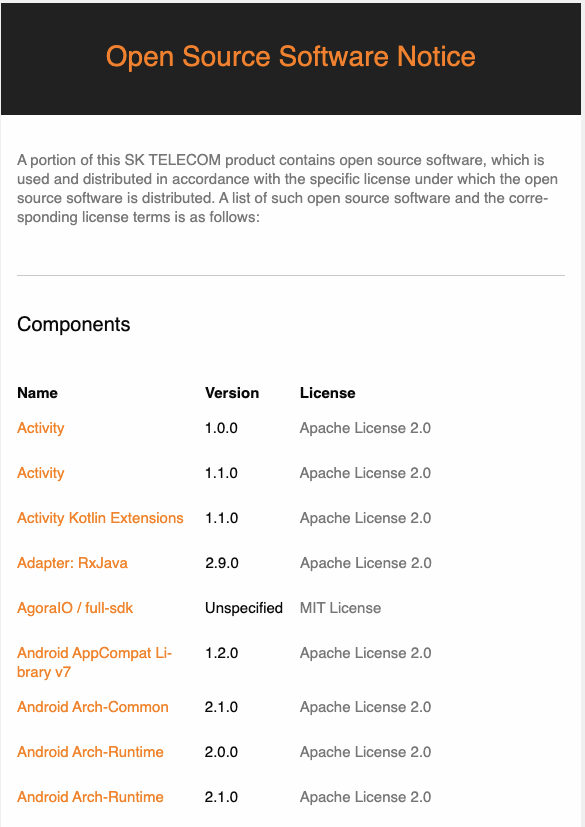
- The method of automatically generating an open source notice corresponding to an open source BOM is further described in “6. Tool”.
Source code package to be disclosed: A package that collects source codes to be disclosed to fulfill open source license obligations that require source code disclosure such as GPL, LGPL, etc.
Compliance artifacts must be provided when distributing supplied software.
In “Appendix 2. Open Source Compliance Process (Sample)”, the compliance artifacts are created and distributed through 7. Notices to 9. Distribution.
When distributing supplied software, if it is difficult to enclose the source code package to be disclosed, it can be replaced by providing a written offer to provide the source code for at least 3 years. Typically, a written offer is provided through the product’s user manual, examples of which are as follows.
The software included in this product contains copyrighted software
that is licensed under the GPL. A copy of that license is included
in this document on page X. You may obtain the complete Corresponding
Source code from us for a period of three years after our last shipment
of this product, which will be no earlier than 2011-08- 01, by sending
a money order or check for $5 to:
GPL Compliance Division
Our Company
Any Town, US 99999
Please write“source for product Y” in the memo line of your payment.
You may also find a copy of the source at http://www.example.com/sources/Y/.
This offer is valid to anyone in receipt of this information.
<SFLC Guide to GPL Compliance>
Therefore, a process must be established to store compliance artifacts for at least 3 years. To this end, a company needs to build an open source website, which is described in detail in “6. Tool”.
If you prepare such a procedure, you can prepare the following evidence required by ISO/IEC 5230.
ISO/IEC 5230
- 3.4.1.1 A documented procedure that describes the process under which the compliance artifacts are prepared and distributed with the supplied software as required by the identified licenses.
Self Certify
- 4.a : Do you have a documented procedure that describes a process that ensures the Compliance Artifacts are distributed with Supplied Software as required by the Identified Licenses?
Respond to third party inquiries
It is important for a company to respond to third party inquiries as quickly and accurately as possible in order to avoid legal litigation. For this, a company must have a process that can respond quickly and effectively to third party open source inquiries.
The figure below shows the process a company must have to respond to third party inquiries.
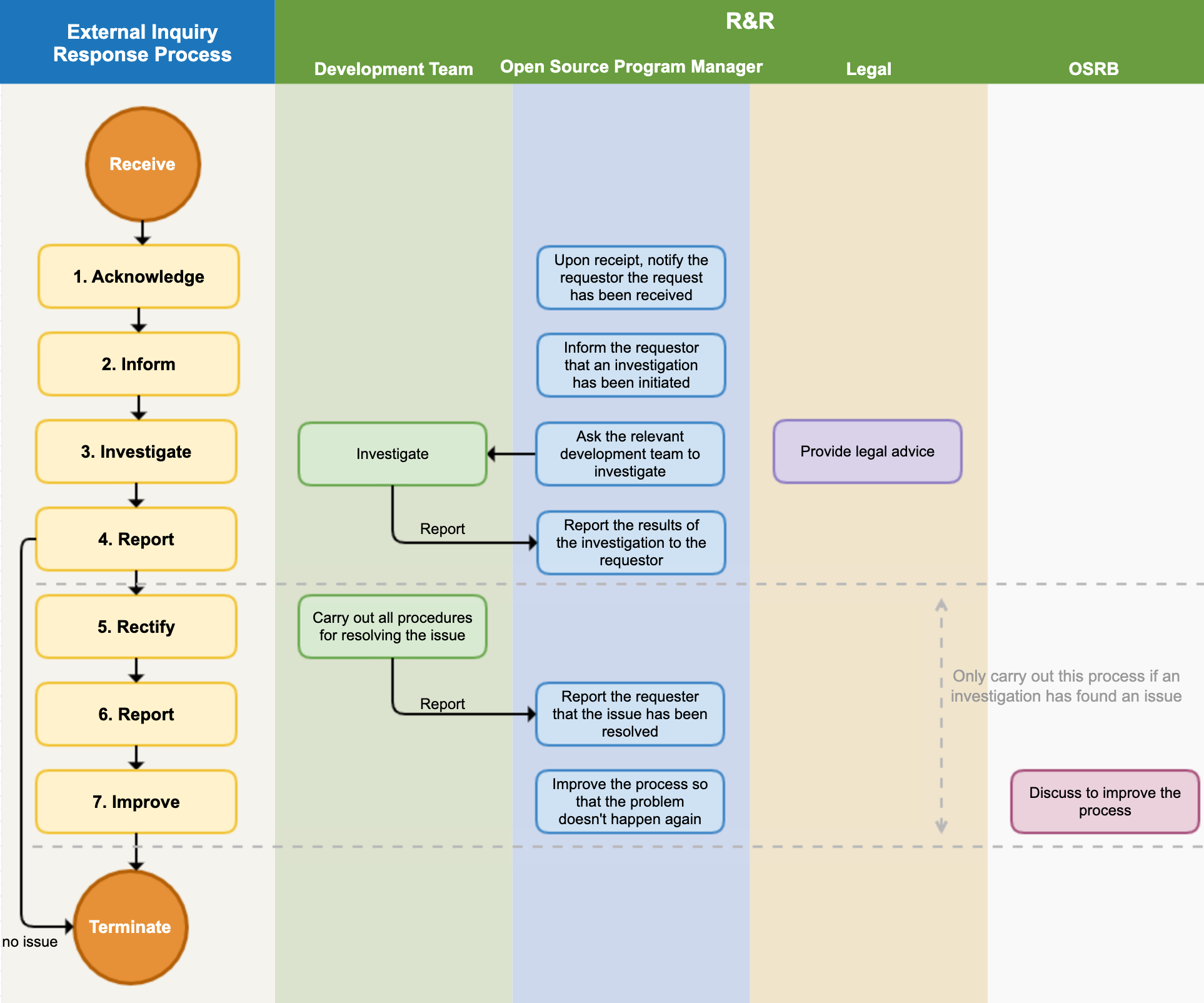
Details can be found in “Appendix 2. Open Source Compliance Process (Sample) 2. External Inquiry Response Process”.
If you prepare such a procedure, you can prepare the following evidence required by ISO/IEC 5230.
ISO/IEC 5230
- 3.2.1.2 An internal documented procedure for responding to third party open source license compliance inquiries.
Self Certify
- 2.c : Do you have a documented procedure that assigns responsibility for receiving and responding to open source compliance inquiries?
Open Source Contribution Process
If you have a policy to allow contributions to external open source projects, there should be a documented procedure to manage how in-house developers can contribute to external projects.
The Open Source Contribution Procedure released by SK telecom is a good example.
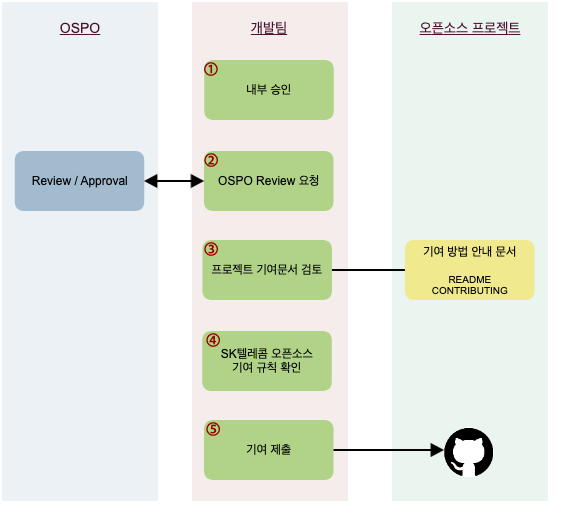 https://sktelecom.github.io/guide/contribute/process/
https://sktelecom.github.io/guide/contribute/process/
If you prepare such a procedure, you can prepare the following evidence required by ISO/IEC 5230.
ISO/IEC 5230
- 3.5.1.2 A documented procedure that governs open source contributions
Self Certify
- 5.b : Do you have a documented procedure that governs Open Source contributions?
If you build the process up to this point, you will comply with the ISO/IEC 5230 requirements as follows.
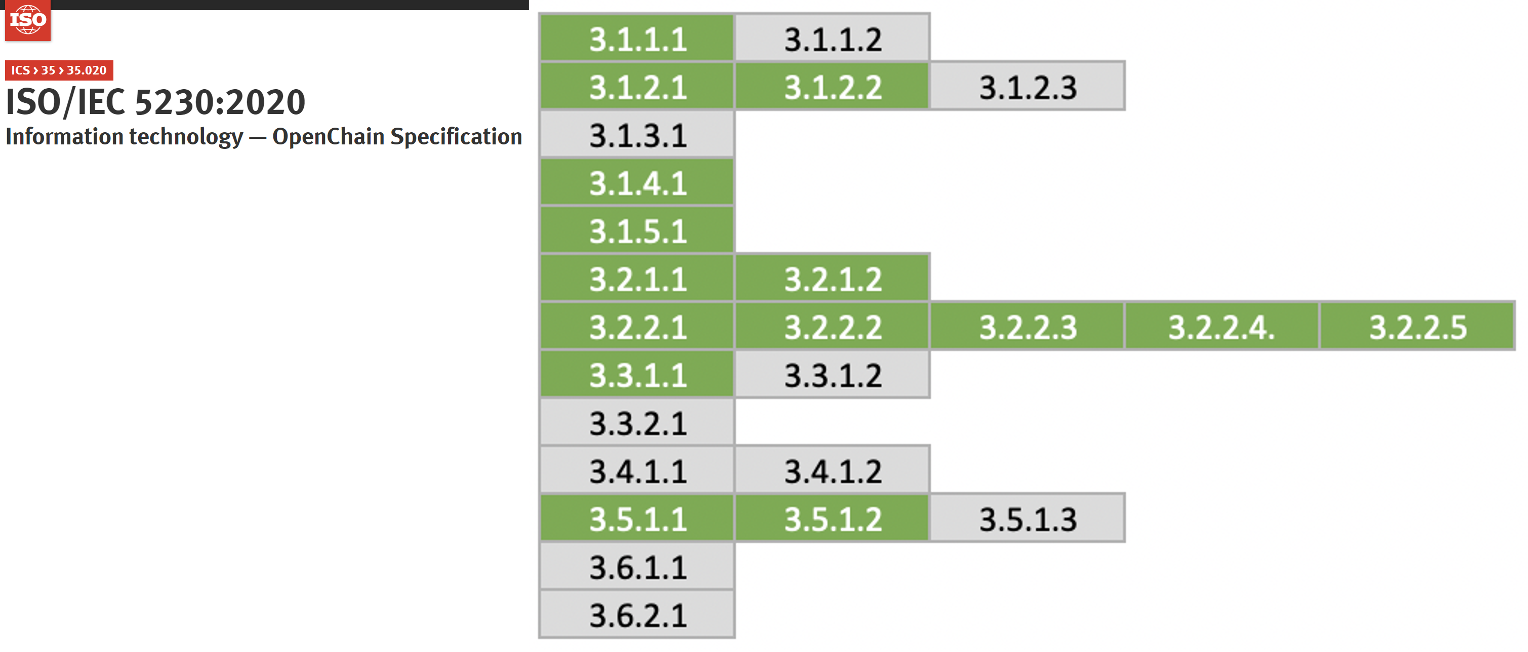
6.6 - 6. Tool
Source code scanning tool
You should use a source code scanning tool during the identification of open source and audit phase of the open source compliance process. Source code scanning tools range from freely available, open source-based tools to commercial tools, each with their own strengths and weaknesses, but none of them seem to provide complete functionality to solve all problems. Therefore, companies can choose the appropriate tool for the characteristics and requirements of the product.
Many companies use a combination of these automated source code scanning tools and manual reviews. Linux Foundation’s FOSSology project is an open source source code scanning tool that companies can use for free.

For instructions on how to install and use FOSSology, refer to Get Started.
Dependency analysis tool
In recent software development, build environments that support Package Manager such as Gradle and Maven are used. In such a build environment, even if there is no source code, the required dependency library at build time is received from the remote to compose the supplied software. At this time, the dependency library is included in the supplied software, but it is not detected by the source code scanning tool. Therefore, it is also important to utilize a tool for dependency analysis.
The OSS Review Toolkit provides a dependency analysis tool called Analyzer.

LG Electronics has released FOSSLight Dependency Scanner as an open source. FOSSLight Dependency Scanner supports various package managers such as Gradle, Maven, NPM, PIP, Pub, and Cocoapods.
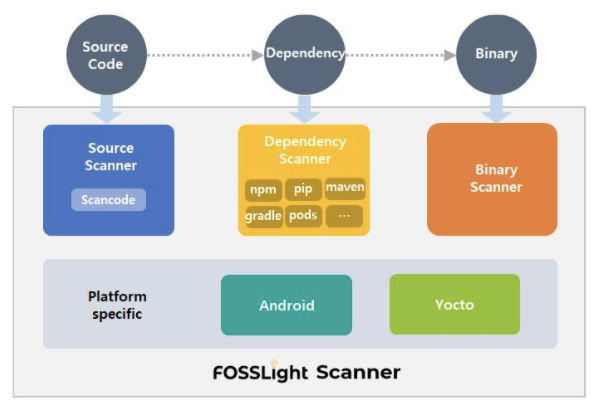
Open Source BOM Management Tool
3.3.1.2 of the ISO/IEC 5230 standard requires that the open source BOM list included in the supplied software be documented and kept. The open source BOM can also be managed with a spreadsheet program such as Excel. However, if the number and version of supplied software exceed hundreds, it is not easy to manage them manually. Therefore, it is better to use an automated tool to manage it.
SW360, an open source project hosted by the Eclipse Foundation, provides a function to track the list of open source BOM included in the supplied software.
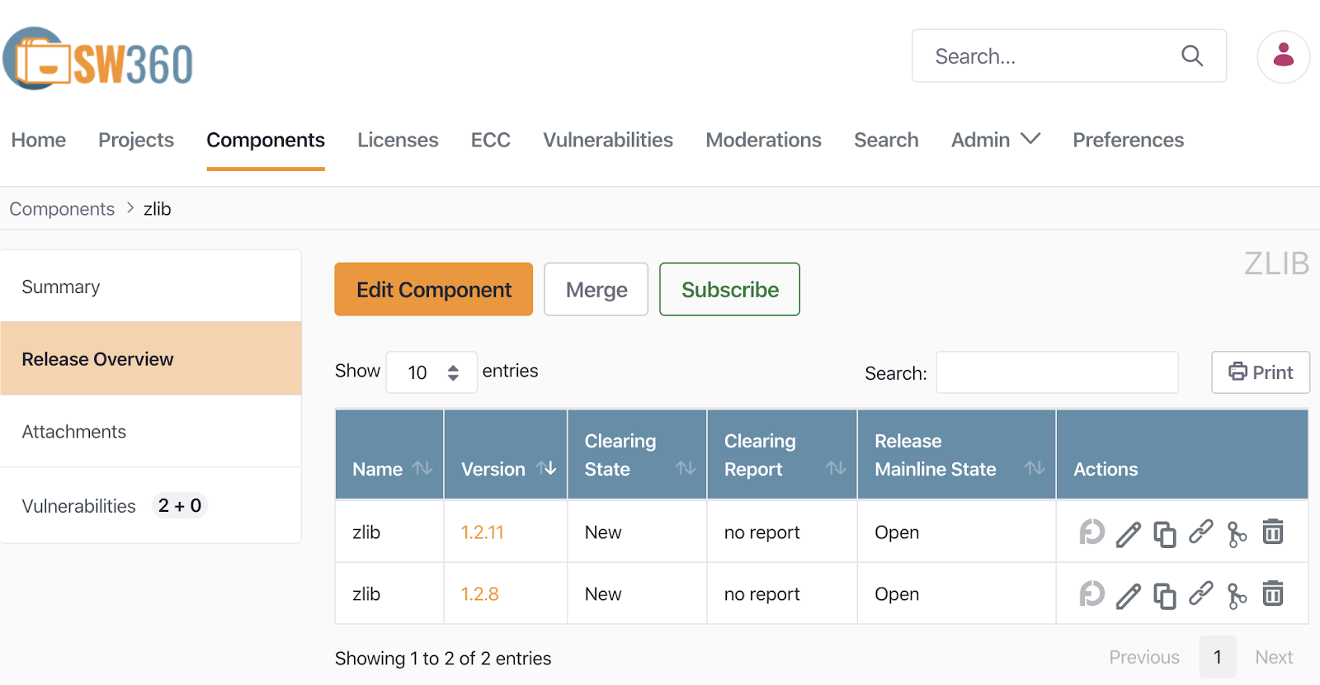
How to install and use SW360 is SW360 wiki
And FOSSLight, an open source released by LG Electronics mentioned above, also provides a function for open source BOM management.
LG Electronics developed FOSSLight on its own and has been managing the open source BOM for supplied software for all business divisions for the past several years, and in June 2021, it announced that it had been released as an open source for anyone to use.
For detailed installation and usage instructions, refer to the following English guide. : https://fosslight.org/fosslight-guide-en/
If you have the above tools, you can prepare the following evidence required by ISO/IEC 5230.
ISO/IEC 5230
- 3.3.1.2 Open source component records for the supplied software that demonstrates the documented procedure was properly followed.
Self Certify
- 3.b : Do you have open source component records for each Supplied Software release which demonstrates the documented procedure was properly followed?
Create artifacts
It is better to use a tool that automatically generates an open source notice, which is an open source compliance product, rather than writing it manually.
You can automatically generate an open source notice by registering an open source BOM using the FOSSLight tool. The open source disclaimer generated by FOSSLight also includes a Written Offer to provide source code.
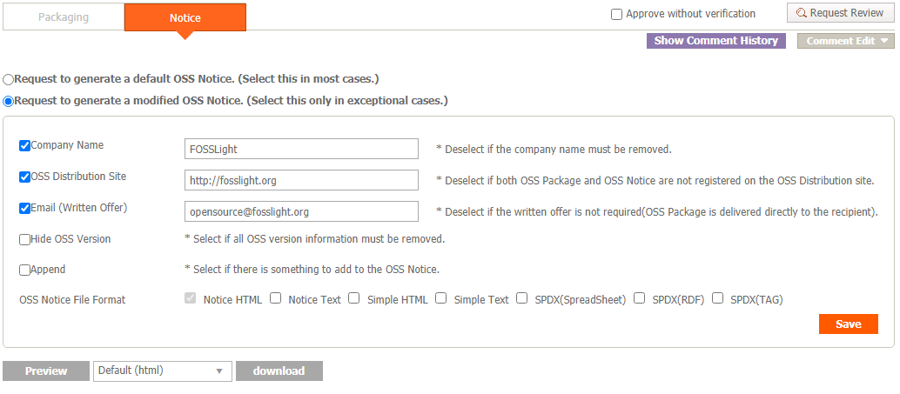
In addition, SK Telecom is planning to release the open source automatic notice generation tool used in-house.
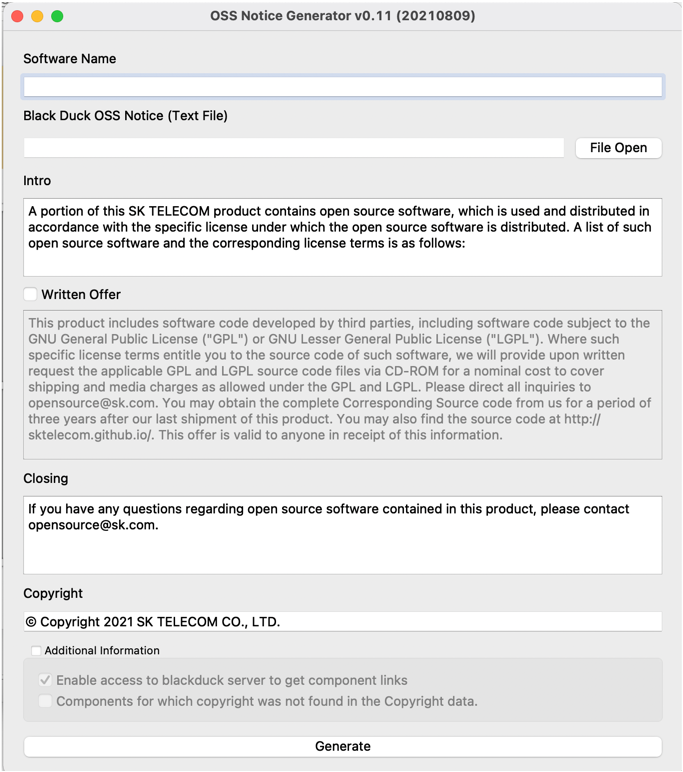
Archive open source artifacts
It is recommended that companies create an open source website and register open source compliance artifacts to provide convenience so that external customers can download open source notices and source code packages to be disclosed at any time.
You can refer to SK Telecom’s open source website.
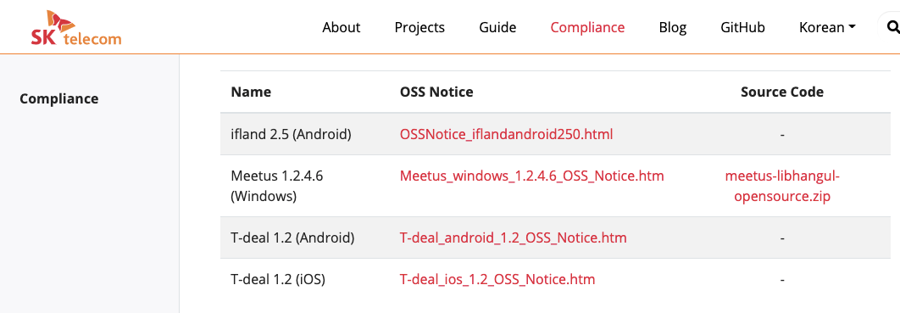
In particular, this website was developed as an open source, and since the source code is open, you can easily build a website by referring to it.
If you build a tool environment like this, you can prepare the following evidence required by ISO/IEC 5230.
ISO/IEC 5230
- 3.4.1.2 A documented procedure for archiving copies of the compliance artifacts of the supplied software - where the archive is planned to exist for a reasonable period of time (determined by domain, legal jurisdiction and/or customer contracts) since the last offer of the supplied software; or as required by the identified licenses (whichever is longer). Records exist that demonstrate the procedure has been properly followed.
Self Certify
- 4.b : Do you archive copies of the Compliance Artifacts of the Supplied Software?
- 4.c : Are the copies of the Compliance Artifacts archived for at least as long as the Supplied Software is offered or as required by the Identified Licenses (whichever is longer)?
If you build the tool environment in this way, you will comply with the ISO/IEC 5230 requirements as follows.
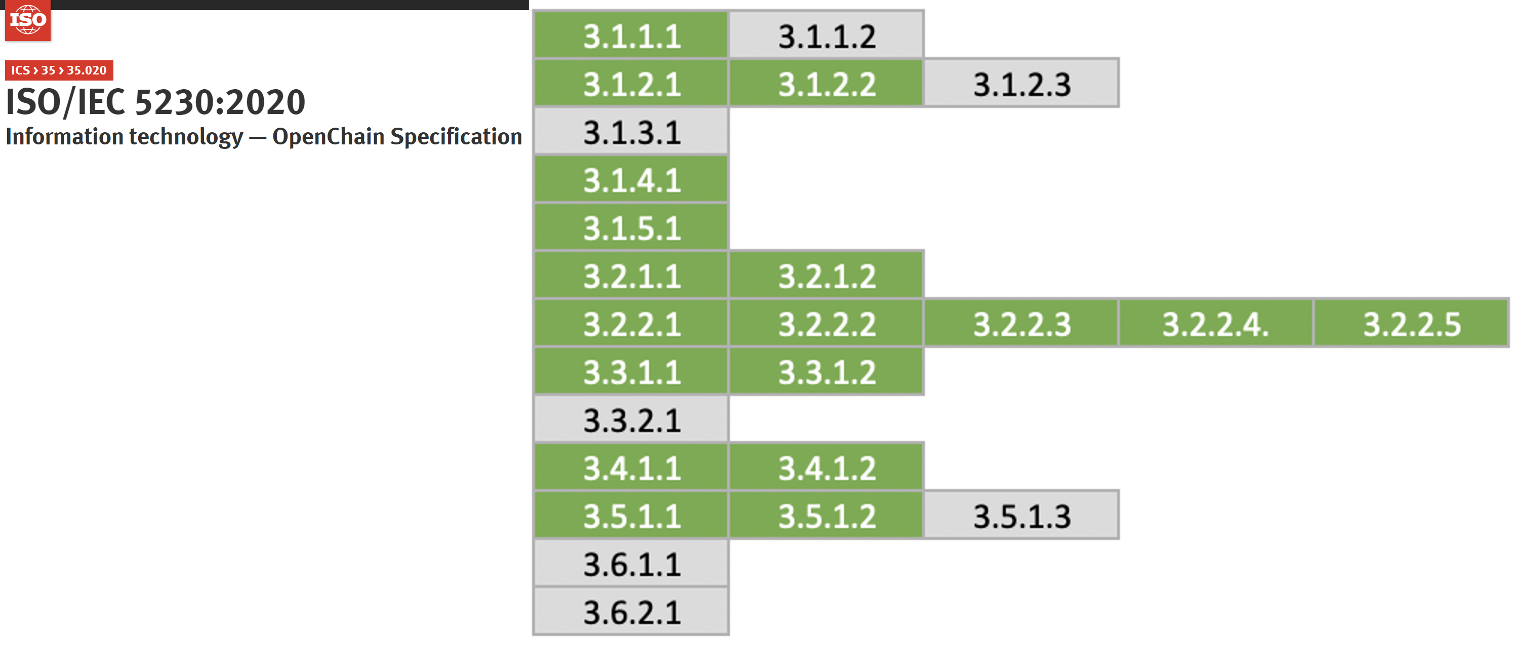
6.7 - 7. Training
Training
No matter how good policies and processes are in place, they will be useless if no one in the company understands and follows them. In order for the open source policy and open source compliance process to work effectively in the company, it is important to educate employees.
You should provide practical methods, such as training and internal wikis, to ensure that all program participants are aware that there is an open source policy within the company and can take necessary actions. Program participants here mean all employees involved in the development, distribution, and contribution of software by a company, including software developers, distribution engineers, and quality engineers.
Many companies publish open source policy documents through their in-house wiki site, so that any employee can see what they need. In addition, training on open source policy is mandatory for new hires during training, and regular training is provided annually or every two years to program participants so that all program participants are aware of the existence of open source policies. . In other words, you should write these methods as the following example and include the open source policy document.
5. Training and Assessment
All program participants should take the open source mandatory
training provided by [Learning Portal] every year. Through training,
all participants should be familiar with open source policies and
processes. Training history is stored in [Learning Portal].
If you build an educational environment like this, you can prepare the following evidence required by ISO/IEC 5230.
ISO/IEC 5230
- 3.1.1.2 A documented procedure that makes program participants aware of the existence of the open source policy (e.g., via training, internal wiki, or other practical communication method).
Self Certify
- 1.b : Do you have a documented procedure that communicates the existence of the open source policy to all Software Staff? (e.g., via training, internal wiki, or other practical communication method)
In addition, you should ensure that program participants are aware of the company’s open source policies, the relevant open source objectives, the contributions expected to ensure the effectiveness of the Program, and the implications of failing to follow the Program requirements. To this end, you should provide training and conduct assessments to ensure that program participants are properly aware. The assessment results are documented and stored.
To do this, you can include the example below in your company’s open source policy.
1. Purpose
(1) Purpose of the policy<sub>(3.1.3.1)</sub>
This policy provides the following principles for all organizations
involved in software development, service, and distribution in OOO
Company (hereinafter referred to as the "Company") to properly utilize
open source software (hereinafter referred to as "Open Source").
1. Principles for open source license compliance
2. Principles for contribution to external open source projects
3. Principles for releasing open source
These principles provide a way for all members of the company to
understand the value of open source, use it correctly, and contribute
to the open source community.
(2) Impact of non-compliance
It is important that [COMPANY] adheres to this policy. Failure to do
so may lead to:
- legal claims from the holders of copyright or other intellectual
property rights in code we use
- claims from our customers;
- the inadvertent release of [COMPANY] proprietary code;
- breach of regulatory obligations by [COMPANY] potentially leading to fines;
- loss of reputation;
- loss of revenue;
- breach of contract with suppliers and customers.
For this reason, we take breaches of this policy seriously, and any
individual breaching the policy may find themselves subject to [COMPANY]'s
disciplinary procedure.
(3) How to contribute to the effectiveness of the Program
All members of the company can contribute to the effectiveness of the
program and improvement of the company's compliance level by understanding
the rationale and content of this policy and faithfully performing the
Assessment will be described in more detail later.
If you include the content of such education in your policy, you can prepare the following evidence required by ISO/IEC 5230.
ISO/IEC 5230
- 3.1.3.1 Documented evidence of assessed awareness for the program participants - which should include the program’s objectives, one’s contribution within the program, and implications of program non-conformance.
Self Certify
- 1.f : Do you have evidence documenting the awareness of your personnel of the following topics?
i - The open source policy and where to find it;
ii - The relevant open source objectives;
iii - The contributions expected to ensure the effectiveness of the Program;
iv - The implications of failing to follow the Program requirements.
Open source training also includes content on the open source contribution policy. Even if an open source contribution policy has been created, if program participants are not aware of its existence, there is a risk of harm to individuals and companies due to unexpected copyright infringement. You should provide open source training so that all program participants are aware of the existence of the open source contribution policy.
If you provide training on the contribution policy in this way, you can prepare the following evidences required by ISO/IEC 5230.
ISO/IEC 5230
- 3.5.1.3 A documented procedure that makes all program participants aware of the existence of the Open Source contribution policy (e.g., via training, internal wiki, or other practical communication method)
Self Certify
- 5.c Do you have a documented procedure that makes all Software Staff aware of the existence of the Open Source contribution policy?
If you want to create a new educational material, it may not be easy for the person in charge who is starting the job for the first time. The OpenChain Project has released the reference training slides for anyone to refer to.

NCSOFT, a Korean game company, has published teaching plans (PPT) and lecture scripts on GitHub so that anyone can use in-house open source educational materials (Korean only).

In addition, Kakao, a representative platform company in Korea, has also released open source training materials for in-house developers so that anyone can refer to it (Korean only).

If you have not yet created training materials, it is also a good way to use open source training materials from these excellent open source management companies.
Assessment
Once you have designated a person in charge for each role, you should ensure that the person assigned is qualified to perform the role based on education, training and experience. Training should also be provided to program participants with insufficient competencies so that they can acquire sufficient competencies. And the company should assess each participant’s competencies and archive the results.
- Provide training so that each participant has the necessary competencies.
- Assess based on education content.
- Keep the assessment results in the company’s training system or HR team.
If it is difficult to provide training because there are more than hundreds of participants in the program, it is also a good idea to use the company’s online training and assessment system.
You can include this in your company’s open source policy as follows.
4. Roles, Responsibilities and Competencies
In order to ensure the effectiveness of the policy, the roles and
responsibilities and the competencies that the person in charge of
each role should have are defined as follows.
The person/group in charge of each role and the required competency
level are defined in [Appendix 1. Status of Person in Charge].
5. Training and Assessment
All members in charge of each role defined in Chapter 4 should take
the advanced open source training course provided by [Learning Portal].
Training history and evaluation results are stored in [Learning Portal]
for at least 3 years.
If you have this training and evaluation system, you can prepare the following evidence required by ISO/IEC 5230.
ISO/IEC 5230
- 3.1.2.3 Documented evidence of assessed competence for each program participant.
Self Certify
- 1.e : Have you documented evidence of assessed competence for each Program participant?
Open Source License Guide
To properly comply with open source licenses, you must know exactly what each open source license requires. However, since it is difficult for a software developer to figure it out on their own, it is recommended that an open source program manager identify requirements / conditions for common use cases for frequently used open source licenses and share them within the company.
The Open Source License Guide should include requirements specific to common open source licensing use cases to ensure that software developers use open source and comply with its license obligations properly.
For general guides on open source licenses and summary of license obligations, refer to the Open Source License Checklists provided by the OSADL.
The document Obligations by license in SK Telecom’s open source guide is also a good resource (Korean only).
 https://sktelecom.github.io/guide/use/obligation/gpl-2.0/
https://sktelecom.github.io/guide/use/obligation/gpl-2.0/
If you provide this open source licensing guide, you can prepare the following evidence required by ISO/IEC 5230.
ISO/IEC 5230
- 3.3.2.1 A documented procedure for handling the common open source license use cases for the open source components of the supplied software.
Self Certify
- 3.c Have you implemented a procedure that handles at least the following common open source license use cases for the open source components of each supplied Supplied Software release?
i - distributed in binary form;
ii - distributed in source form;
iii - integrated with other open source such that it may trigger copyleft obligations;
iv - contains modified open source;
v - contains open source or other software under an incompatible license interacting with other components within the Supplied Software;
vi - contains open source with attribution requirements.
If you build an environment for providing training, assessment and guide in this way, you will comply with ISO/IEC 5230 requirements as follows.
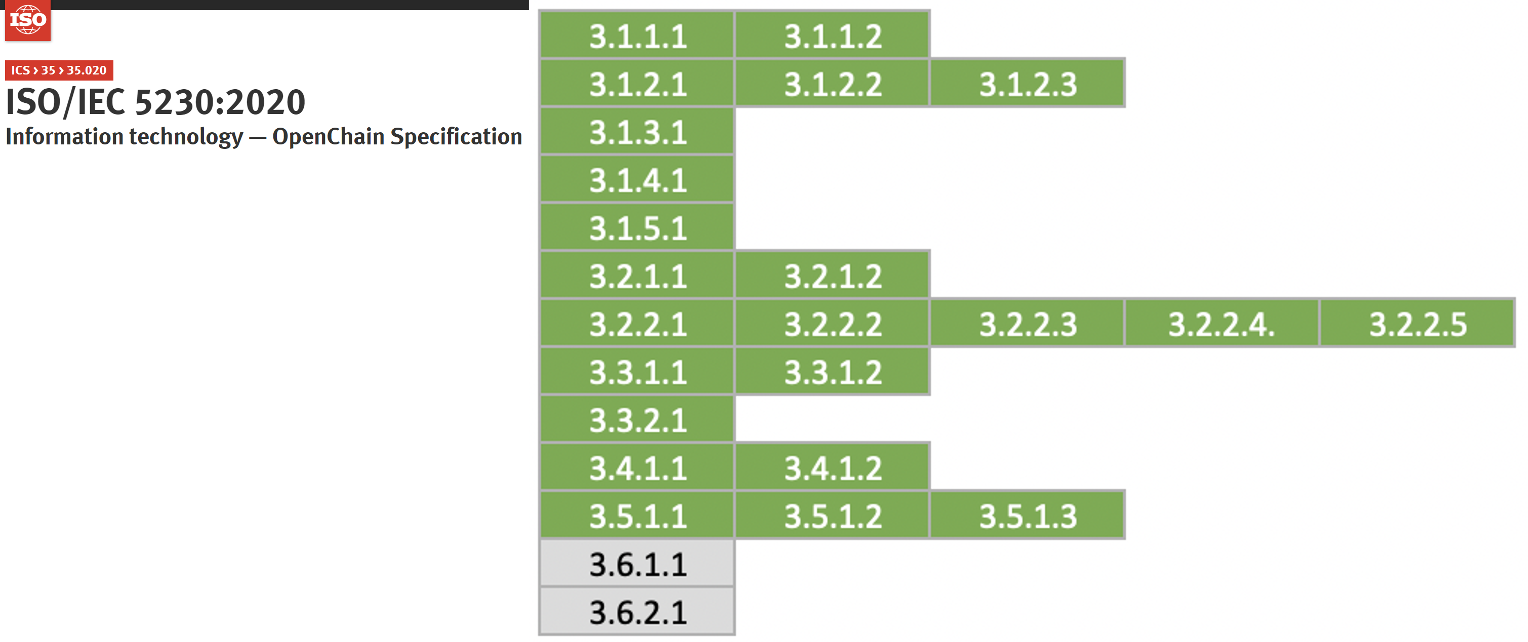
6.8 - 8. Conformance
If you build an open source program (open source policy / process / tool / organization) that complies with all requirements except Article 6 of the ISO/IEC 5230 standard, you can write and publish a document specifying the following two.
- A document affirming the program specified in requirement §3.1.4 satisfies all the requirements of this specification.
- A document affirming the program meets all the requirements of this version of the specification (version 2.1), within the past 18 months of obtaining conformance validation
You may include the above document in the open source policy, or you may publish it through an externally public website.
As shown in the image below, you can refer to the content that SK Telecom posted on the open source portal site.
 https://sktelecom.github.io/en/compliance/iso5230/
https://sktelecom.github.io/en/compliance/iso5230/
If you document that you meet all the requirements of ISO/IEC 5230 in this way, you can prepare the following evidence required by ISO/IEC 5230.
ISO/IEC 5230
- 3.6.1.1 A document affirming the program specified in requirement §3.1.4 satisfies all the requirements of this specification.
- 3.6.2.1 A document affirming the program meets all the requirements of this version of the specification (version 2.1), within the past 18 months of obtaining conformance validation
Self Certify
- 6.a : Do you have documentation confirming that your Program meets all the requirements of this specification?
- 6.b : Do you have documentation confirming that your Program conformance was reviewed within the last 18 months?
If you’ve made it this far, your company will finally meet all the requirements of ISO/IEC 5230.
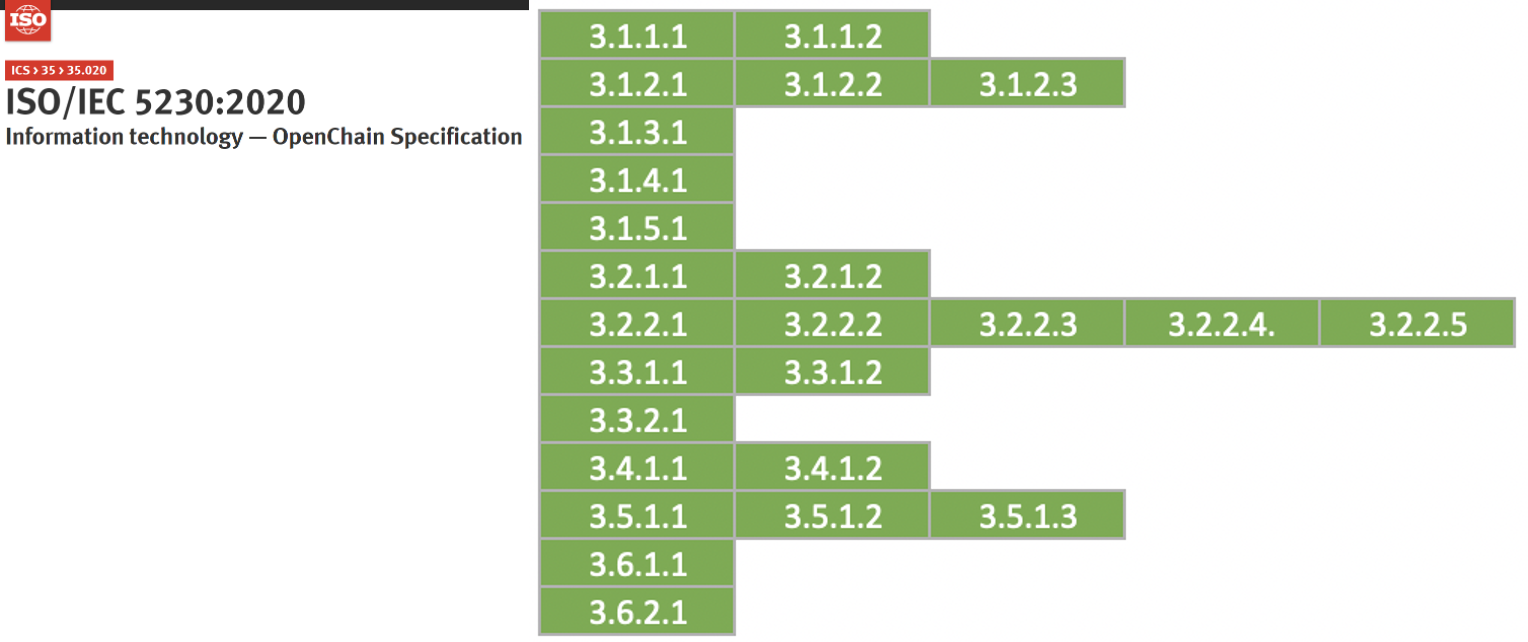
6.9 - Appendix
6.9.1 - 1. Open Source Policy (Sample)
Note:
This sample open source policy was written with reference to the following two materials.
1. Purpose
(1) Purpose of the policy(3.1.3.1)
This policy provides the following principles for all organizations involved in software development, service, and distribution in [COMPANY] (hereinafter referred to as the “Company”) to properly utilize open source software (hereinafter referred to as “Open Source”).
- Principles for open source license compliance
- Principles for contribution to external open source projects
- Principles for releasing open source
These principles provide a way for all members of the company to understand the value of open source, use it correctly, and contribute to the open source community.
All members of the company can view the open source policy at the following link on the in-house wiki: [internal_link](3.1.1.1)
(2) Impact of non-compliance
It is important that [COMPANY] adheres to this policy. Failure to do so may lead to:
- legal claims from the holders of copyright or other intellectual property rights in code we use
- claims from our customers;
- the inadvertent release of [COMPANY] proprietary code;
- breach of regulatory obligations by [COMPANY] potentially leading to fines;
- loss of reputation;
- loss of revenue;
- breach of contract with suppliers and customers. For this reason, we take breaches of this policy seriously, and any individual breaching the policy may find themselves subject to [COMPANY]’s disciplinary procedure.
(3) How to contribute to the effectiveness of the Program
All members of the company can contribute to the effectiveness of the program and improvement of the company’s compliance level by understanding the rationale and content of this policy and faithfully performing the necessary activities.
2. Scope(3.1.4.1)
This policy applies to the following three parts:
- Applies to [all products provided or distributed by the company externally]. However, the open source only for internal use is not included in the scope of this policy.
- Applied when contributing to external open source projects.
- Applied when releasing internal code as open source.
The scope can be changed according to the business environment of the company, and the procedure for this is as follows.
- If the open source program manager determines that it is necessary to change the scope of policy according to changes in the company’s business environment, such as a new business or reorganization, submit a proposal for this to the OSRB.
- OSRB approves proposals for scope changes at the appropriate level.
- OSRB modifies the open source policy to change the scope of the policy.
3. Terms
- “compliance artifacts” - a collection of artifacts that represent the output of a compliance program and accompany the supplied software. The collection may include (but is not limited to) one or more of the following: attribution notices, source code, build and install scripts, copy of licenses, copyright notices, modification notifications, written offers, open source component bill of materials, and SPDX documents.
- “open source” - software subject to one or more licenses that meet the Open Source Definition published by the Open Source Initiative (see opensource.org/osd) or the Free Software Definition published by the Free Software Foundation (see gnu.org/philosophy/free-sw.html) or similar license.
- “program” - the set of policies, processes and personnel that comprise an organization’s open source license compliance activities.
- “program participants” - any organization employee or contractor that defines, contributes to or has responsibility for preparing supplied software. Depending on the organization, that may include (but is not limited to) software developers, release engineers, quality engineers, product marketing and product management.
- “SPDX” - the format standard created by the Linux Foundation’s SPDX (Software Package Data Exchange) Working Group for exchanging bill of materials for a given software package, including associated license and copyright information (see spdx.org).
- “supplied software” - software that an organization distributes to third parties (e.g., other organizations or individuals).
4. Roles, Responsibilities and Competencies(3.1.2.1)
In order to ensure the effectiveness of the policy, the roles and responsibilities and the competencies that the person in charge of each role should have are defined as follows.
The person/group in charge of each role and the required competency level are defined in [Appendix 1. Status of Person in Charge].(3.1.2.2)
- The open source program manager periodically updates the list according to the company’s business situation.(3.2.2.1)
- The head of the organization responsible for each role designates a person in charge within the organization, and allocates appropriate time and budget for the person in charge to fulfill the role.(3.2.2.2)
- The person in charge of each role should raise an issue with the open source program manager if appropriate support is not provided while performing his/her role.
- The open source program manager discusses problem solving with the head of the organization. If not properly resolved, the open source program manager may request the OSRB to resolve the issue.
- OSRB shares the problem with the head of the higher level organization and asks for a solution.
(1) OSRB
OSRBOpen Source Review Board is a consultative body composed of an open source program manager, legal team, patent team, development team, and infrastructure team for the company’s open source compliance.
- Create policies and processes for open source compliance, and define roles and responsibilities within the company to implement them.
- When an open source compliance issue occurs within the company, discuss solutions and prepare countermeasures.
- If necessary, report issues to the executive team to receive feedback on risk mitigation measures.
(2) Open Source Program Manager
The open source program manager is responsible for the overall responsibility for the company’s open source programs. To ensure open source compliance of products and services using open source, open source program manager is responsible for:(3.2.2.4)
- Define the roles required for open source compliance, and designate a responsible person and group in charge of each role. Consult with OSRB if necessary.
- Supervise and assess open source compliance training.
- Serves as the chair of the OSRB and directs its activities.
- Respond to inquiries and requests related to open source use and compliance from outside.
- Review and approve requests for use of open source.
- Maintain open source BOM records.
- Provides a way to request legal advice on open source.(3.2.2.3)
- Maintain a repository for open source notices and source code disclosure.
(3) OSPO
OSPOOpen Source Program Office is responsible for supporting and nurturing the growth of open source activities inside and outside the company.
- Establish, improve and disseminate open source policies.
- Provides a guide for contributing code to external open source projects.
- Provides a guide for releasing an in-house project as an open source.
- Develop and operate an open source portal.
- Develop and select open source tools.
- Sponsor open source project events.
- Manage relationships with the open source community.
(4) Legal team
The legal team provides advice on legal risks and mitigation measures that may arise in the process of using open source, such as interpreting open source licenses and obligations.
- Advise on licensing and intellectual property issues, including conflicts due to incompatible open source licenses.
- When contributing to external open source projects, review necessary legal matters such as open source licenses and CLAContributor License Agreement.
(5) IT infrastructure team
The IT infrastructure team operates and automates open source analysis tools to build a system so that license analysis is performed automatically for supplied software.
- Operate an open source license analysis tool.
- Automate license analysis by integrating with DevOps.
- Establish systems and processes so that license analysis is performed for supplied software.
- Obtain and maintain an open source BOM for supplied software.
(6) Security Officer
The security officer operates an open source security vulnerability analysis tool to build a system so that security vulnerability analysis is performed smoothly for supplied software.
- Operate an open source security vulnerability analysis tool.
- Automate open source security vulnerability analysis by integrating with DevSecOps.
- Establish systems and processes so that open source security vulnerability analysis is performed for supplied software.
(7) Development Culture
The development culture manager supports developers to actively utilize open source and participate in the open source community to learn a good development culture.
- Encourage developers to participate in the open source community.
- Create a culture where activities in open source projects can be recognized as achievements.
- Create a development culture that can be perceived as an attractive company to open source developers.
(8) Quality Responsible
The organization responsible for quality, such as QA, checks whether the open source license obligations have been properly performed when distributing software.
- Check whether open source compliance activities are performed in accordance with the development process.
- Check that the artifacts are generated as required by the open source license.
- When distributing software, make sure that the open source notice and the source code to be released are provided together.
- If an issue is found, notify the software development/deployment team and guide them to fix the issue immediately.
5. Training and Assessment
All program participants should take the open source mandatory training provided by [Learning Portal] every year. Through training, all participants should be familiar with open source policies and processes. Training history is stored in [Learning Portal].(3.1.1.2)
All members in charge of each role defined in Chapter 4 should take the advanced open source training course provided by [Learning Portal]. Training history and assessment results are stored in [Learning Portal] for at least 3 years.(3.1.2.3)
6. Use open source
If you use open source to develop and distribute products and services, you should comply with the obligations required by each open source license. The activities that companies perform for this purpose are called open source compliance.
For proper open source compliance activities, software development/distribution organizations should comply with the following:(3.3.1.1)
- All processes of the open source compliance process are recorded and preserved in Jira Issue Tracker.
(1) Identify open source and review license obligations.
When using open source to develop products / services, first identify what an open source license is, and review and investigate the obligations that the license requires.
The company’s [Open Source License Guide] provides a guide for frequently used open source licenses, and explains the obligations for each type of distribution as follows for each license.(3.3.2.1)
- Distributed in binary form;
- Distributed in source form;
- Integrated with other open source such that it triggers additional licensing obligations;
- Contains modified open source;
- Contains open source or other software under an incompatible license interacting with other components within the supplied software; and/or
- Contains open source with attribution requirements.
Software development/distribution teams can refer to this guide when reviewing their open source license obligations. If you need to review an open source license not mentioned in this guide, contact your open source program manager.
(2) Design software considering open source licenses.
Identify open source dependencies and design your software architecture so that your code is not subject to open source licenses. .
The company’s [Open Source Licensing Guide] describes the source code disclosure scope for each open source license and design methods to prevent disclosure of own code.
(3) Create an open source compliance artifact.
The most basic of open source compliance activities is to identify open sources included in supplied software. This is to properly meet the open source license requirements, which are the core of open source compliance. That is, a set of compliance artifacts for open source included in the supplied software should be generated.(3.4.1.1)
Open source compliance artifacts are divided into two main categories.
- Open source notice: A document to provide full open source license and copyright notice
- Source code package to be disclosed: A package that collects source code to be disclosed to fulfill open source license obligations that require source code disclosure such as GPL, LGPL, etc.
To collect, distribute and store these compliance artifacts, the following should be complied with.(3.4.1.2)
- Open source notices or source code packages to be disclosed are collected according to the conditions required by each license. For example, a license requires the accompanying full text of the license, but not just a link.
- Collected artifacts are stored in a separate storage.
- When providing source code to be made public by a written agreement, provide a download link so that the external general public can access the repository of the collected artifacts.
Follow the company’s open source compliance process to create and provide open source compliance artifacts as above.
(4) Create open source Bill of Materials (BOM)
Create and manage the Bill of Materials (BOM) included in the supplied software.(3.3.1.2)
Follow the company’s open source compliance process to create and preserve open source BOMs using open source tools.
(5) Compliance Issue Remediation Procedure
Should a non-compliance issue be raised, the Open Source Program Manager responds promptly by performing the following procedures.(3.2.2.5)
- Acknowledge receipt of the query and state a reasonable time for resolution;
- Determine whether the query discloses a genuine issue or not (and if not, respond to the querier accordingly);
- If the issue is genuine, apply to prioritise, and determine the appropriate response.
- Carry out response and, where necessary, improve open source compliance processes.
- Document the above using Jira Tracker.
7. Open Source Contributions
The company encourages participation and contribution to external open source projects to create business value in open source. However, in this process, you should be careful about unintentional exposure of the company’s intellectual property or infringement of the rights of third parties. Therefore, members of the company should comply with the following when contributing to external open source projects.(3.5.1.1)
(1) Request a review and get approval.
An open source contribution is to grant an open source project the right of an author to modify/use/distribute a work from a copyright point of view. In some cases, you may need to transfer your copyright to an open source project. In general, however, the copyright of a work created during employment is owned by the employer. In other words, works created by company members are owned by the company. Contributing to open source works created while you were employed may raise unnecessary copyright infringement issues.
Therefore, if there is an open source project that you would like to contribute to, follow the review request and approval procedures before making the initial contribution according to the open source contribution process.
However, in the case of a small contribution as follows, since the risk of copyright infringement is not large, you can contribute at your own discretion without the review process.
- Small code snippets of 10 lines or less
- Inquiries and answers on Stack Overflow
- Activities on GitHub: Issue creation, Pull Request Review / Approve, etc.
(2) Contribute only code that you have the right to contribute
Only contribute code for which you have the right to contribute. In other words, contribute your own code, not third-party code.
(3) Be careful not to expose the company’s intellectual property
Do not contribute code or documents that may expose the company’s intellectual property such as sensitive information or patents.
- If the code you want to contribute includes [Company]’s patent, you should check whether you can contribute to the project under the open source license. If there is any ambiguity, contact OSPO.
(4) Be careful about signing the CLA.
Some open source projects require all contributors to sign a CLAContributor License Agreement. This is an agreement to seek consent from contributors to reduce copyright disputes that may arise when a project manages the works of multiple contributors. Typically, a company-led project requires a CLA to be signed.
The CLA varies from project to project, but primarily includes agreement to the following:
- I (or my company) have the right to contribute to the project the contribution I intend to contribute. (i.e. I am the author of this contribution.)
- I (or my company) grant the project the right to modify, distribute, and manage my contributions to the project.
- I (or my company) will not revoke the authority granted to me.
- I (or my company) grant the project the right to change the license according to future needs of the project.
In addition, in rare cases, some CLAs also require consent to the following terms and conditions:
- I (or my company) transfer my copyright to the project or project management organization at the same time as I contribute my contribution.
[Company] does not allow contributions to open source projects that require transfer of copyright to protect the company’s intellectual property. Therefore, if the open source project you want to contribute to requires the CLA to be signed, be sure to ask OSPO for a review before signing.
(5) Add company copyright notice
The intellectual property of the work you create during your employment is basically owned by the company. Therefore, you should add your company’s copyright notice when contributing code to external open source projects.
When contributing more than one file, add the copyright and license notices at the top of the files, like this:
Copyright (c) {$year} {$Company}
SPDX-License-Identifier: {$SPDX_license_name}
Here, $SPDX_license_name is written according to the license of the corresponding open source project.
However, if your contribution is only to modify existing code for the purpose of fixing a bug, you do not need to add a copyright notice for that code modification.
(6) Use your company email
When contributing to an open source project, use your company email, not your personal email. This will (1) give you a sense of responsibility to communicate with the community on behalf of the company, and (2) improve the awareness of the company that actively contributes to the open source community.
8. Open Source Release
[Company] respects the value of collaboration with the open source community and encourages the release of internal software as an open source project. However, there are several rules that should be followed to protect the company’s intellectual property and prevent unintentional copyright infringement.
(1) Get approval
From a copyright point of view, releasing as open source means that the author grants the right to modify/use/distribute the work by anyone through an open source license. In general, the copyright of a work created during employment is owned by the employer. In other words, the work you create is owned by the company. The act of arbitrarily releasing a work as open source may cause unnecessary copyright infringement issues.
Therefore, if you want to release the software as open source, follow the review request and approval procedure according to the company’s open source release policy.
Do not hesitate to contact OSPO if anything in your open source process appears to be undesirable.
(2) Release only the code you have the right to publish.
One of the worst things that can happen to an open source project is that the project contains legally problematic code. Code that the company does not have the right to release, or code that infringes IP, such as another company’s patent, can cause legal problems. Therefore, while preparing the code to be released, check the source of all code and delete problematic code.
(3) Be careful about the exposure of the company’s intellectual property.
Do not release code or documents that may expose sensitive information or patents to the company’s intellectual property.
If the code you want to release contains [Company] patent, see if you can release it under the open source license. If there are any ambiguities, please contact OSPO.
(4) Publish useful code
To be a successful project, it should also be useful to others. If a similar project already exists, join the existing project rather than create a new one.
An open source that intends to release should be able to expect: (1) provide differentiated value to the open source community; (2) to solve problems that the community has not been able to solve; (3) We receive positive attention by releasing our technology.
- If the code we haven’t used in our products or services, don’t even release it as open source.
- Do not publish code that addresses a problem that has already been addressed by the open source community. If this is the case, contribute to an existing open source project.
(5) Prepare the resource
Prepare in advance the resources that will be put into the open source project, including developers.
- In the beginning, the number of developers similar to that of a general in-house project is required.
- Get developers who can quickly review external contributions.
- The role of the legal team and marketing team is also required.
- Secure a budget for the infrastructure required to maintain and manage the project. This includes tools for hosting projects like Github.
If you can’t create an environment with enough resources to support it, don’t release it as open source.
(6) Use your company email
For open source release activities, do not use personal emails, but use company emails. This will (1) give you a sense of responsibility to communicate with the community on behalf of the company, and (2) improve the awareness of the company that actively contributes to the open source community.
9. Respond to external inquiries
(1) Responsibility for responding to external inquiries
The open source program manager is responsible for responding to inquiries and requests for open source compliance from outside.(3.2.1.2)
- The open source program manager may assign all or part of the handling of inquiries to appropriate personnel within the company. If necessary, contact the legal team to deal with it.
- Anyone who receives an inquiry about open source compliance from outside will notify the open source program manager so that a prompt response can be made.
(2) Disclosure of contact information
The open source program manager publicly provides the contact information of the person in charge so that external inquiries and requests related to open source can be submitted to the company.(3.2.1.1)
- Include the email address of the person in charge in the open source notice.
- Register your contact in the Linux Foundation’s Open Compliance Directory.
(3) External Inquiry Response Procedure
If you respond quickly and accurately to open source compliance inquiries from outside, you can significantly reduce the risk of going to a lawsuit. To this end, in order to respond to external open source compliance inquiries, you should follow the external inquiry response process defined in the company’s open source compliance process.(3.2.1.2)
10. OpenChain
[COMPANY] supports the Linux Foundation’s OpenChain project. This policy has been carefully designed to be compliant with the OpenChain Specification v2.1, ISO/IEC 5230:2020.
- [COMPANY] affirms that as of [insert date] it is in compliance with the OpenChain Specification v 2.1, ISO/IEC 5230:2020.(3.6.1.1)
- [COMPANY] affirms that within the past 18 months of obtaining conformance validation, the program meets all the requirements of the OpenChain Specification v2.1, ISO/IEC 5230:2020.(3.6.2.1)
- [COMPANY]’s affirmation of conformance will be reviewed and renewed if appropriate at intervals of at least [12|18 months].
Appendix 1. List of persons in charge
| No | role | responsibility | Required Competencies | Responsible Organization | Contact Person |
|---|---|---|---|---|---|
| 1 | Open Source Program Manager | This role is responsible for general responsibility for the company’s open source programs. | 1. Understanding the software development process 2. Understanding intellectual property related to open source licenses such as copyrights and patents 3. Expertise in Open Source Compliance 4. Open source development experience 5. Communication Skills | CTO | OOO |
| 2 | Legal | Interpret open source licenses and obligations. This role provides advice on the mitigation of legal risks that may arise for the use of open source, such as the actual implementation of these obligations. | 1. Basic knowledge of open source ecosystem 2. Expertise in software copyright 3. Expertise in Open Source Licensing | Legal Team | OOO |
| 3 | Infrastructure | This role operates and automates open source analysis tools to build systems so that license analysis is performed automatically for all supplied software. | 1. Basic knowledge of open source compliance process 2. Understanding of open source license analysis tools 3. IT infrastructure expertise | IT Infrastructure Team | OOO |
| 4 | Security | This role operates an open source security vulnerability analysis tool to build a system so that security vulnerability analysis is automatically performed for all supplied software. | 1. Basic knowledge of open source compliance process 2. Understanding of open source license analysis tools 3. Security Expertise | Security Team | OOO |
| 5 | Development culture | This role supports developers to actively utilize open source and learn a good development culture by participating in the open source community. | 1. Understanding the software development process 2. Basic knowledge of open source compliance 3. Understanding Open Source Policies | DR | OOO |
| 6 | development team | In this role, software development/distribution organizations adhere to open source policies and processes for proper use of open source. | 1. Understanding the software development process 2. Basic knowledge of open source compliance 3. Understanding of Open Source Policy 4. Basic knowledge of open source licenses | Development team | All developers |
6.9.2 - 2. Open Source Compliance Process (Sample)
OOO Corporation (hereinafter referred to as the “Company”) actively uses open source software (hereinafter referred to as “Open Source”) while developing products and services including the software. When a company distributes its software, it should perform activities to comply with the obligations imposed by the open source license, which is called open source compliance.
1. Process for software development/distribution
This open source compliance process defines the procedures a [company] should follow to comply with its open source license obligations for each stage of development for developing and distributing software products and services. All employees involved in developing/distributing software products should follow these 10 steps of the Open Source Compliance Process.
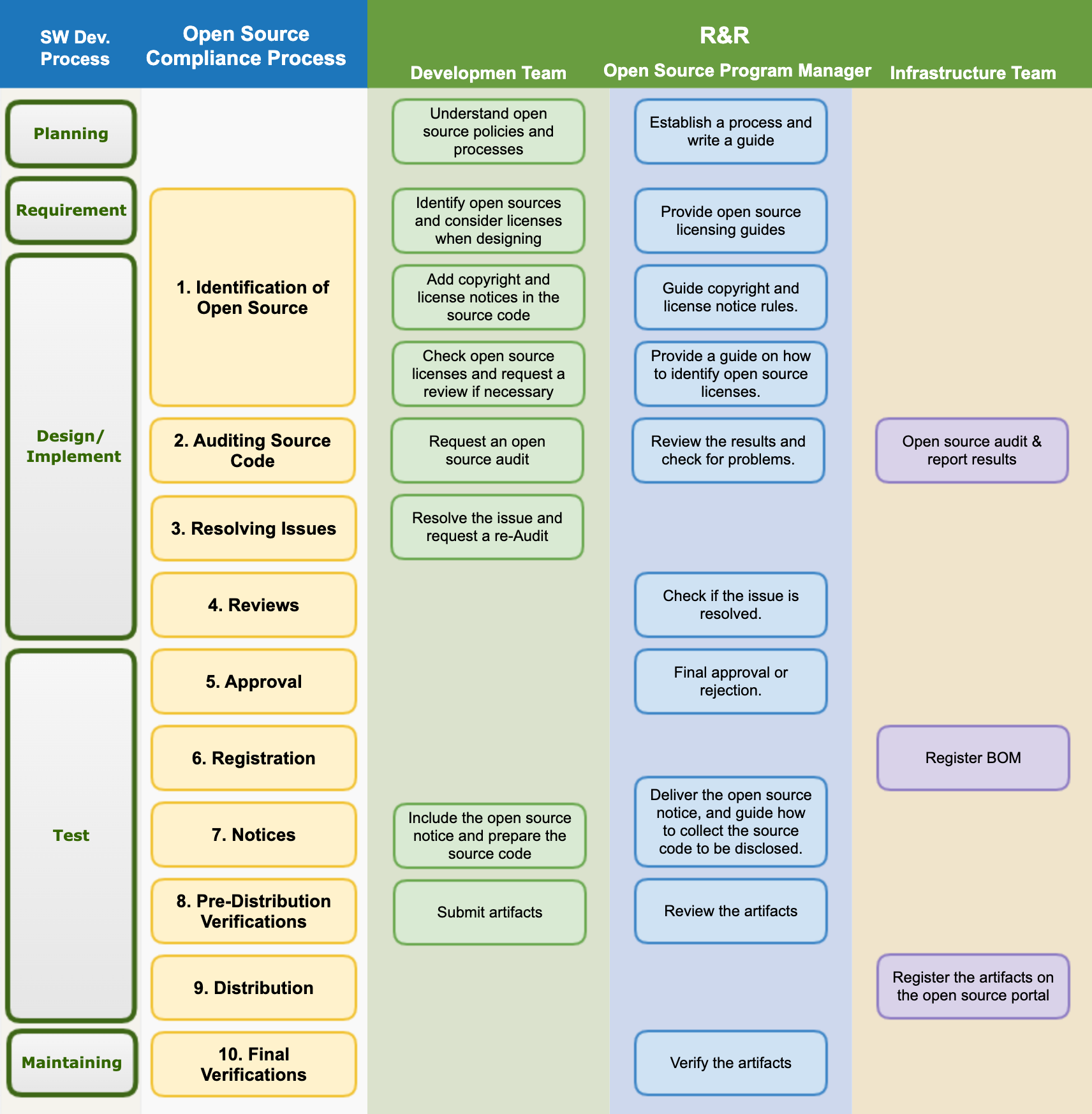
1. Identification of Open Source
The development team should adhere to the following during the software design phase.
- Identify predictable open source usage and check licenses while designing software.
- Check the obligations for each open source license. You can check the obligations for each license in the company’s Open Source Licensing Guide.
- Design software considering the source code disclosure scope of each open source license.
Open source program managers should write a guide on the obligations, restrictions, and rights of frequently used open source licenses, and make them available for reference to the development team.
The development team should display the copyright and license in the source code according to the company’s policy. The copyright and license notation rules in the company’s source code can be found on the following page. : (insert_link)
When a development team needs to use a new open source, first identify the license. Check your license obligations, restrictions, and rights according to your company’s Open Source Licensing Guide. If the license is not described in the company’s open source license guide, ask the open source program manager whether it can be introduced or not. Create a Jira Ticket and inquire.
Open source program managers guide the software development team by analyzing their open source license obligations.
- If in doubt, seek advice from the Legal Department to provide clear guidance.
- Add newly analyzed open source licenses to the guide.
2. Auditing Source Code
The development team requests open source audit by providing the source code according to the guidance of the infrastructure team.
The development team uses the open source analysis tool provided by the infrastructure team to audit the open source and generate the open source BOM.
The open source program manager reviews whether the obligations of the open source license can be complied with and whether there is an open source license conflict, and if there is an issue, ask the development team to resolve it. Create issues with Jira Tickets and assign them to the development team.
3. Resolving Issues
The development team should resolve any issues found during the source code inspection phase. Take action, such as removing the open source that has become an issue, or replacing it with an open source under a different license.
When the development team resolves all issues found, Resolve the Jira Ticket issue and request a review.
4. Reviews
Open source program managers review that all issues have been properly addressed. If necessary, re-audit the source code using an open source analysis tool.
5. Approval
The open source program manager should finally approve or reject whether the open source compliance process has been properly performed. In case of rejection, explain the reason and suggest to the development team how to fix it.
6. Registration
The open source program manager confirms the BOM for tracking the list of open source usage by version of the software.
The person in charge of infrastructure registers the confirmed BOM in the system. Include in the BOM a list of the open sources included with the supplied software and information such as:
- Product (or service) name and version of the supplied software
- Open Source List
- Open source name / version
- Open source license
7. Notices
Open Source Program Managers create Open Source Notices to comply with notice obligations. Include the following in the Open Source Notice.
- Open source contact information for external inquiries related to open source
- Notice by open source
- Copyright notice
- Open source license name
- A copy of the open source license
- Written Offer to receive a copy of the source code (if applicable)
The open source program manager creates an Open Source Notice and delivers it to the development team. In this case, if it is necessary to disclose the source code, guide the development team on how to collect the source code to be disclosed.
The development team should enclose the Open Source Notice when distributing the product. In the case of a product with a screen, take measures so that the user can check it through the menu. (Example: Apps > Menu > Settings > Copyright Information > Open Source License)
If the development team uses open source under a license that requires source code disclosure, such as GPL or LGPL, check the source code disclosure scope for this and collect the source code to be disclosed.
- The source code collected to comply with license obligations such as GPL and LGPL should match the source code that creates the binaries loaded in the product. In other words, when the compiled source code is built, it should be the same as the binary loaded on the product.
8. Pre-Distribution Verifications
The development team should submit the following artifacts demonstrating that the open source compliance activities were properly conducted.
- Final Open Source Notice included in the product
- Materials confirming that the product includes Open Source Notice (eg, screen capture image showing Open Source Notice)
- (if applicable) source code to be disclosed (compressed and submitted in one file)
The open source program manager should review the data submitted by the development team and check for any abnormalities.
9. Distribution
Open source program managers should submit compliance artifacts submitted by the development team to the infrastructure team.
The infrastructure team registers the compliance artifacts on the company’s open source distribution site.
10. Final Verifications
The open source program manager should comprehensively check whether the compliance product is registered on the company’s open source portal without any abnormality or whether it is downloaded from outside the company.
2. External Inquiry Response Process
If you respond quickly and accurately to open source compliance inquiries from outside, you can greatly reduce the risk of going to a lawsuit. Therefore, you should follow the following process to respond to external open source compliance inquiries.
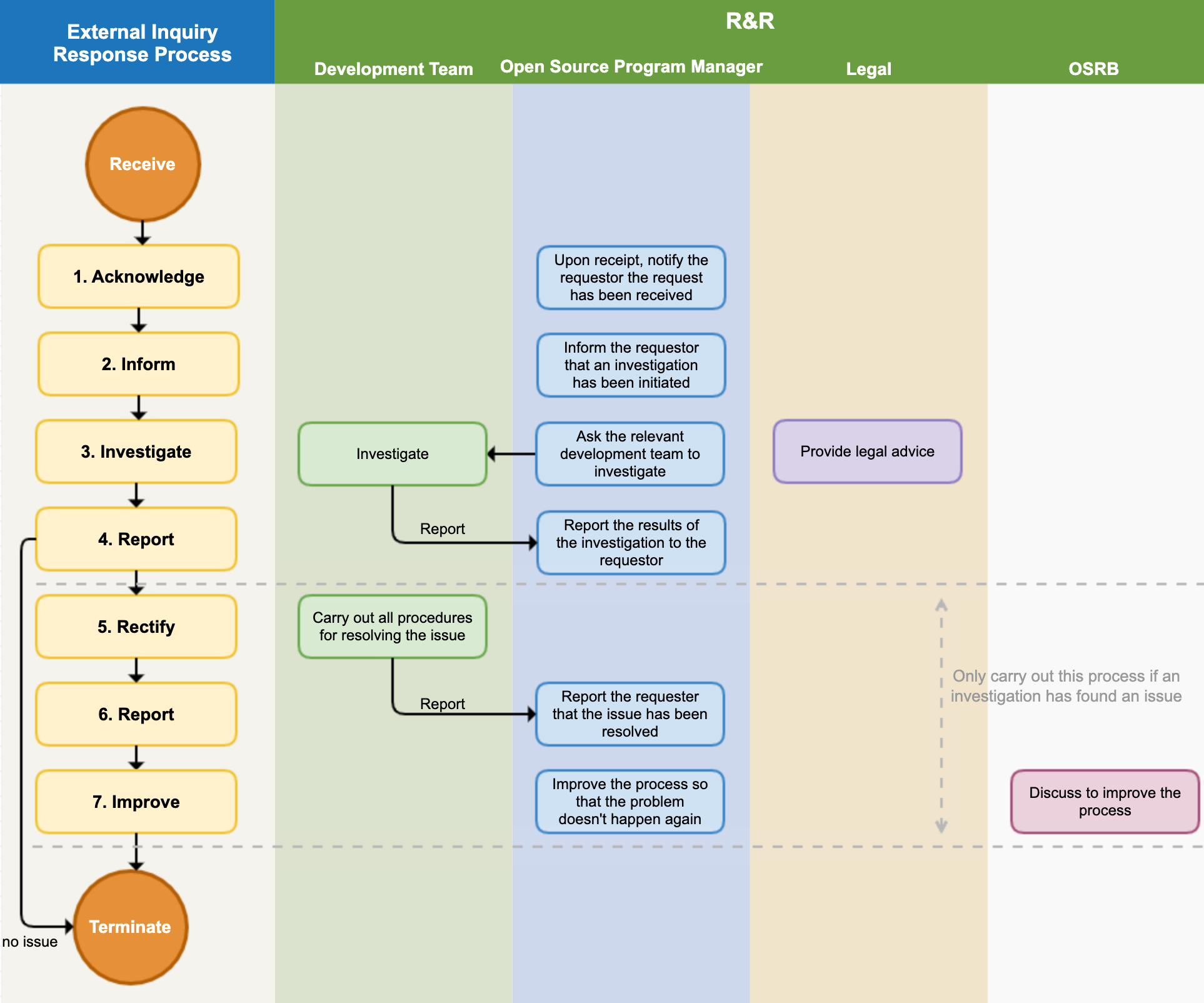
1. Acknowledge
The open source program manager immediately informs the requester that the inquiry has been received. In this case, inform the requester of the expected date of action. Since it’s important to know exactly what the requester’s intent is, ask for further clarification if the inquiry is unclear.
The main contents of inquiries and requests that require response are as follows.
- Inquiries about whether open source has been used for certain products and services
- Request to provide source code under the GPL, LGPL license mentioned in the Written Offer
- Request for clarification of open source found in the product and disclosure of source code even though it is not specified in the Open Source Notice
- Request to provide missing files and build methods in the source code published due to GPL, LGPL, etc.
- Request for copyright notice
The open source program manager creates a Jira Issue for the received request and records all responses in detail.
2. Inform
The open source program manager informs the requester that it is faithfully performing open source compliance and is investigating the requester’s inquiry. Notify the requestor whenever possible internal investigation progress is updated.
3. Investigate
The open source program manager conducts an internal investigation of the request. Check the BOM and documented review history to ensure that the compliance process has been properly implemented for the version of the product in question. Seek advice from the Legal Department if necessary.
If a specific development team needs confirmation, the open source program manager should ask the development team to investigate. The development team requested to be investigated immediately identifies any issues with the compliance artifacts and reports the findings to the open source program manager.
4. Report
The open source program manager should complete the internal investigation within the due date for action and inform the requester of the results.
- If the requester’s complaint was a misunderstanding rather than a compliance issue, notify the requester without further action and terminate the procedure.
- If any compliance issues are discovered, inform the requester of the exact method and timing to fulfill the obligations of the applicable open source license.
5. Rectify
If an internal investigation reveals an actual compliance issue, the development team should take all necessary steps to resolve the compliance issue.
6. Report
After resolving the issue, notify the requester immediately and provide the best way to confirm that the issue has been resolved.
7. Improve
If there are compliance issues, conduct an OSRB meeting to review the case, find out how the issue arose, and improve the process so that the issue does not recur.